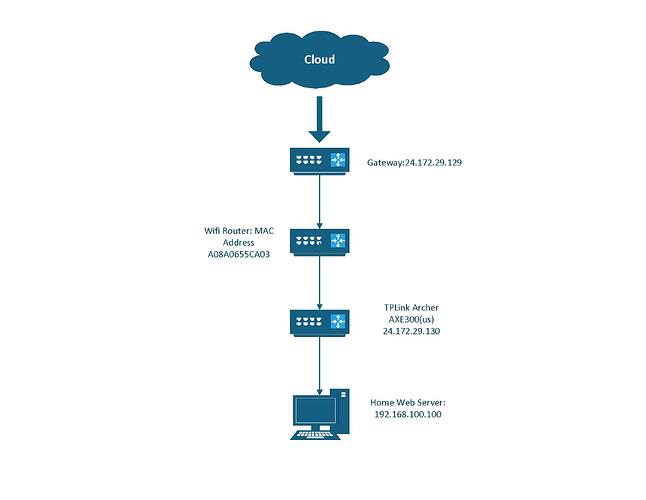
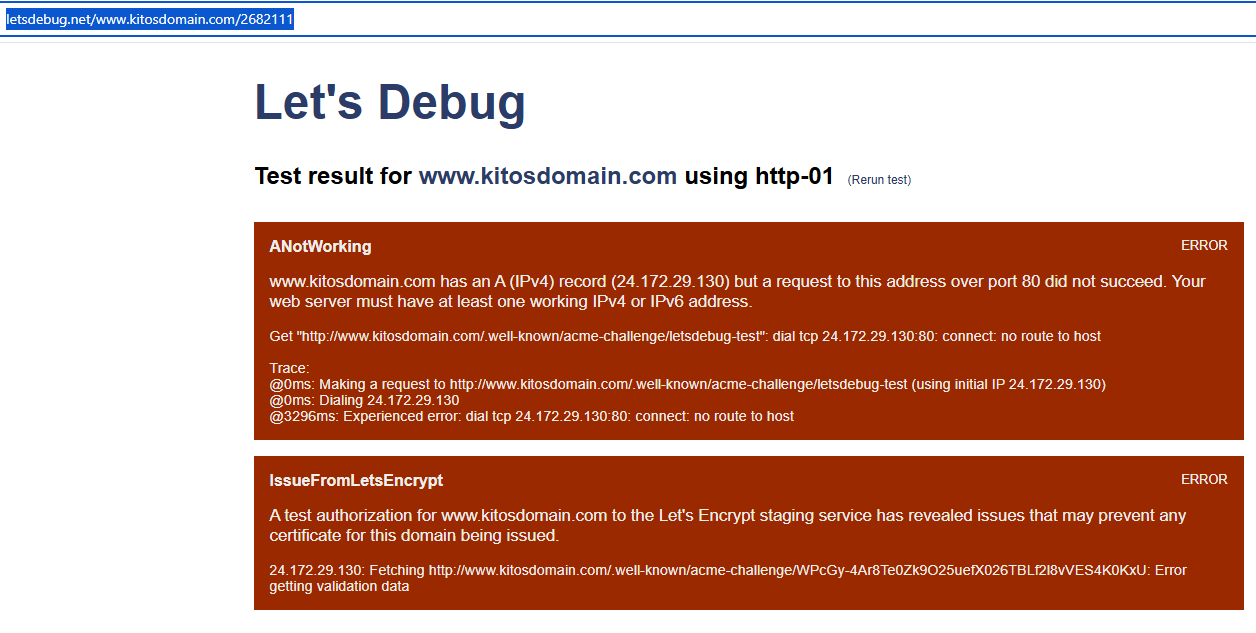
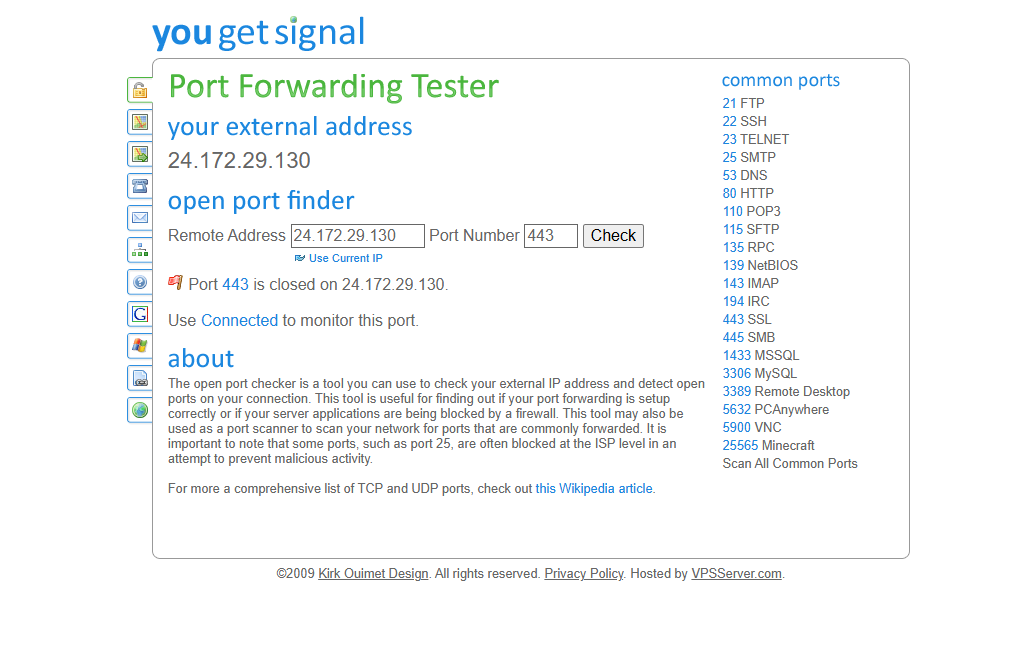
letsencrypt.log_old.txt (25.1 KB)
2026-01-11 16:42:32,524:DEBUG:certbot._internal.main:certbot version: 4.1.1
2026-01-11 16:42:32,524:DEBUG:certbot._internal.main:Location of certbot entry point: /usr/sbin/certbot
2026-01-11 16:42:32,524:DEBUG:certbot._internal.main:Arguments: ['--apache', '-v']
2026-01-11 16:42:32,524:DEBUG:certbot._internal.main:Discovered plugins: PluginsRegistry(PluginEntryPoint#apache,PluginEntryPoint#manual,PluginEntryPoint#null,PluginEntryPoint#standalone,PluginEntryPoint#webroot)
2026-01-11 16:42:32,533:DEBUG:certbot._internal.log:Root logging level set at 20
2026-01-11 16:42:32,534:DEBUG:certbot._internal.plugins.selection:Requested authenticator apache and installer apache
2026-01-11 16:42:32,596:DEBUG:certbot_apache._internal.configurator:Apache version is 2.4.66
2026-01-11 16:42:32,985:DEBUG:certbot._internal.plugins.selection:Single candidate plugin: * apache
Description: Apache Web Server plugin
Interfaces: Authenticator, Installer, Plugin
Entry point: EntryPoint(name='apache', value='certbot_apache._internal.entrypoint:ENTRYPOINT', group='certbot.plugins')
Initialized: <certbot_apache._internal.override_fedora.FedoraConfigurator object at 0x7f3941b86ba0>
Prep: True
2026-01-11 16:42:32,985:DEBUG:certbot._internal.plugins.selection:Selected authenticator <certbot_apache._internal.override_fedora.FedoraConfigurator object at 0x7f3941b86ba0> and installer <certbot_apache._internal.override_fedora.FedoraConfigurator object at 0x7f3941b86ba0>
2026-01-11 16:42:32,985:INFO:certbot._internal.plugins.selection:Plugins selected: Authenticator apache, Installer apache
2026-01-11 16:42:33,060:DEBUG:certbot._internal.main:Picked account: <Account(RegistrationResource(body=Registration(key=None, contact=(), agreement=None, status=None, terms_of_service_agreed=None, only_return_existing=None, external_account_binding=None), uri='https://acme-v02.api.letsencrypt.org/acme/acct/2955412526', new_authzr_uri=None, terms_of_service=None), 3a11d45f9b534764e185000436950237, Meta(creation_dt=datetime.datetime(2026, 1, 11, 21, 26, 44, tzinfo=datetime.timezone.utc), creation_host='kitoshomeserver.kitosdomain.com', register_to_eff='kitojoseph@gmail.com'))>
2026-01-11 16:42:33,060:DEBUG:acme.client:Sending GET request to https://acme-v02.api.letsencrypt.org/directory.
2026-01-11 16:42:33,062:DEBUG:urllib3.connectionpool:Starting new HTTPS connection (1): acme-v02.api.letsencrypt.org:443
2026-01-11 16:42:33,318:DEBUG:urllib3.connectionpool:https://acme-v02.api.letsencrypt.org:443 "GET /directory HTTP/1.1" 200 1033
2026-01-11 16:42:33,319:DEBUG:acme.client:Received response:
HTTP 200
Server: nginx
Date: Sun, 11 Jan 2026 21:42:33 GMT
Content-Type: application/json
Content-Length: 1033
Connection: keep-alive
Cache-Control: public, max-age=0, no-cache
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
{
"4cuOK-cknt4": "Adding random entries to the directory",
"keyChange": "https://acme-v02.api.letsencrypt.org/acme/key-change",
"meta": {
"caaIdentities": [
"letsencrypt.org"
],
"profiles": {
"classic": "Profiles - Let's Encrypt",
"shortlived": "Profiles - Let's Encrypt",
"tlsclient": "Profiles - Let's Encrypt",
"tlsserver": "Profiles - Let's Encrypt"
},
"termsOfService": "https://letsencrypt.org/documents/LE-SA-v1.6-August-18-2025.pdf",
"website": "https://letsencrypt.org"
},
"newAccount": "https://acme-v02.api.letsencrypt.org/acme/new-acct",
"newNonce": "https://acme-v02.api.letsencrypt.org/acme/new-nonce",
"newOrder": "https://acme-v02.api.letsencrypt.org/acme/new-order",
"renewalInfo": "https://acme-v02.api.letsencrypt.org/acme/renewal-info",
"revokeCert": "https://acme-v02.api.letsencrypt.org/acme/revoke-cert"
}
2026-01-11 16:42:33,320:DEBUG:certbot.util:Not suggesting name "127.0.0.1"
Traceback (most recent call last):
File "/usr/lib/python3.14/site-packages/certbot/util.py", line 395, in get_filtered_names
filtered_names.add(enforce_le_validity(name))
~~~~~~~~~~~~~~~~~~~^^^^^^
File "/usr/lib/python3.14/site-packages/certbot/util.py", line 583, in enforce_le_validity
domain = enforce_domain_sanity(domain)
File "/usr/lib/python3.14/site-packages/certbot/util.py", line 643, in enforce_domain_sanity
raise errors.ConfigurationError(
...<2 lines>...
"bare IP address.".format(domain))
certbot.errors.ConfigurationError: Requested name 127.0.0.1 is an IP address. The Let's Encrypt certificate authority will not issue certificates for a bare IP address.
2026-01-11 16:42:40,423:DEBUG:certbot._internal.display.obj:Notifying user: Requesting a certificate for www.kitosdomain.com
2026-01-11 16:42:40,425:DEBUG:acme.client:Requesting fresh nonce
2026-01-11 16:42:40,425:DEBUG:acme.client:Sending HEAD request to https://acme-v02.api.letsencrypt.org/acme/new-nonce.
2026-01-11 16:42:40,493:DEBUG:urllib3.connectionpool:https://acme-v02.api.letsencrypt.org:443 "HEAD /acme/new-nonce HTTP/1.1" 200 0
2026-01-11 16:42:40,493:DEBUG:acme.client:Received response:
HTTP 200
Server: nginx
Date: Sun, 11 Jan 2026 21:42:40 GMT
Connection: keep-alive
Cache-Control: public, max-age=0, no-cache
Link: https://acme-v02.api.letsencrypt.org/directory;rel="index"
Replay-Nonce: Pihtai8mraAWPmw2olcA478RsON3MfFVilXoVOsdMTsz3pox2Qo
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
2026-01-11 16:42:40,494:DEBUG:acme.client:Storing nonce: Pihtai8mraAWPmw2olcA478RsON3MfFVilXoVOsdMTsz3pox2Qo
2026-01-11 16:42:40,494:DEBUG:acme.client:JWS payload:
b'{\n "identifiers": [\n {\n "type": "dns",\n "value": "www.kitosdomain.com"\n }\n ]\n}'
2026-01-11 16:42:40,498:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/new-order:
{
"protected": "eyJhbGciOiAiUlMyNTYiLCAia2lkIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMjk1NTQxMjUyNiIsICJub25jZSI6ICJQaWh0YWk4bXJhQVdQbXcyb2xjQTQ3OFJzT04zTWZGVmlsWG9WT3NkTVRzejNwb3gyUW8iLCAidXJsIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL25ldy1vcmRlciJ9",
"signature": "gIWrx1TvdheidVP_-APbNM65MHxnXG8TP0tFhy5zKRuUWrvc3By10RDYb7EZIXn7V6TDxarDZoD39Hq2PQsiVLN0Xa7nrG2c_ny5SeVPRN3tErIdinRWIeuOXdRfgX1VlnVv2hEL0D6E-lSNZ9khnDzMCojgXIUxVnhYxdTM0uakn3Cb79_KYTfOL37jEhmv9R5viFjEWgllVtSwP9648-ZPAR66UgpkfFE92pbauPzLhwWYGQvxvIwaqMfW7HRLyRkBJfNEzO6oiz_8TWUmEiN9X589u_ijwJolwVjIZv2YiP9safv3ve5dhgGfXd9WvorL4zqTBvYKQWPxuV0D2g",
"payload": "ewogICJpZGVudGlmaWVycyI6IFsKICAgIHsKICAgICAgInR5cGUiOiAiZG5zIiwKICAgICAgInZhbHVlIjogInd3dy5raXRvc2RvbWFpbi5jb20iCiAgICB9CiAgXQp9"
}
2026-01-11 16:42:40,722:DEBUG:urllib3.connectionpool:https://acme-v02.api.letsencrypt.org:443 "POST /acme/new-order HTTP/1.1" 201 353
2026-01-11 16:42:40,723:DEBUG:acme.client:Received response:
HTTP 201
Server: nginx
Date: Sun, 11 Jan 2026 21:42:40 GMT
Content-Type: application/json
Content-Length: 353
Connection: keep-alive
Boulder-Requester: 2955412526
Cache-Control: public, max-age=0, no-cache
Link: https://acme-v02.api.letsencrypt.org/directory;rel="index"
Location: https://acme-v02.api.letsencrypt.org/acme/order/2955412526/468503491646
Replay-Nonce: Pihtai8mhRUHcBwONLrHOBLf8uxJ7sDoASSmkrFfB46GG37Ahcs
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
{
"status": "pending",
"expires": "2026-01-18T21:42:40Z",
"identifiers": [
{
"type": "dns",
"value": "www.kitosdomain.com"
}
],
"authorizations": [
"https://acme-v02.api.letsencrypt.org/acme/authz/2955412526/641639778556"
],
"finalize": "https://acme-v02.api.letsencrypt.org/acme/finalize/2955412526/468503491646"
}
2026-01-11 16:42:40,723:DEBUG:acme.client:Storing nonce: Pihtai8mhRUHcBwONLrHOBLf8uxJ7sDoASSmkrFfB46GG37Ahcs
2026-01-11 16:42:40,724:DEBUG:acme.client:JWS payload:
b''
2026-01-11 16:42:40,726:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/authz/2955412526/641639778556:
{
"protected": "eyJhbGciOiAiUlMyNTYiLCAia2lkIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMjk1NTQxMjUyNiIsICJub25jZSI6ICJQaWh0YWk4bWhSVUhjQndPTkxySE9CTGY4dXhKN3NEb0FTU21rckZmQjQ2R0czN0FoY3MiLCAidXJsIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2F1dGh6LzI5NTU0MTI1MjYvNjQxNjM5Nzc4NTU2In0",
"signature": "i_qByA10n02DH4_Lc-va-z9U0v2Ur_VNS4JaLJyPF8NOK_IQDmVKfLQDDD1G1BHdc9EA3hJG4qDdPn2LiWP9JD3K7MsMyLhsOH9SPiosAwNZ7YJIYFeqbvwjc8LDFSDwco8xWQft-AZkqsRJT8yBoOAK3Q_UiDiKV1GCVCwhmKciG-9Moz_tIrnCM9j2mGqWwB0sTfQvhT-LNUCjCJKCldToBYI5wjulebulM7yKOTzlZhAE-Xqo-5HU628dJprX2XNfDdiFePu3qVBf3JXgQSD3nl0_6qDO0LpOulQBGhWMU3SYlBUPlD2dqSl_rV7m1TOotMFECkWNhH54Se-FTA",
"payload": ""
}
2026-01-11 16:42:40,806:DEBUG:urllib3.connectionpool:https://acme-v02.api.letsencrypt.org:443 "POST /acme/authz/2955412526/641639778556 HTTP/1.1" 200 827
2026-01-11 16:42:40,807:DEBUG:acme.client:Received response:
HTTP 200
Server: nginx
Date: Sun, 11 Jan 2026 21:42:40 GMT
Content-Type: application/json
Content-Length: 827
Connection: keep-alive
Boulder-Requester: 2955412526
Cache-Control: public, max-age=0, no-cache
Link: https://acme-v02.api.letsencrypt.org/directory;rel="index"
Replay-Nonce: lXCKneqJo02TVKy22LZF0vkuXvVfeDMgxQ5rSqyuFPmRn6V4pcI
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
{
"identifier": {
"type": "dns",
"value": "www.kitosdomain.com"
},
"status": "pending",
"expires": "2026-01-18T21:42:40Z",
"challenges": [
{
"type": "dns-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall/2955412526/641639778556/iGw4fw",
"status": "pending",
"token": "TIm7sCdxnMQqAYxK6pAV1jEcjkzujqaCrm2LWg7ZNBg"
},
{
"type": "tls-alpn-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall/2955412526/641639778556/6maOgA",
"status": "pending",
"token": "TIm7sCdxnMQqAYxK6pAV1jEcjkzujqaCrm2LWg7ZNBg"
},
{
"type": "http-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall/2955412526/641639778556/d6rP2w",
"status": "pending",
"token": "TIm7sCdxnMQqAYxK6pAV1jEcjkzujqaCrm2LWg7ZNBg"
}
]
}
2026-01-11 16:42:40,807:DEBUG:acme.client:Storing nonce: lXCKneqJo02TVKy22LZF0vkuXvVfeDMgxQ5rSqyuFPmRn6V4pcI
2026-01-11 16:42:40,808:INFO:certbot._internal.auth_handler:Performing the following challenges:
2026-01-11 16:42:40,808:INFO:certbot._internal.auth_handler:http-01 challenge for www.kitosdomain.com
2026-01-11 16:42:40,855:DEBUG:certbot_apache._internal.http_01:Adding a temporary challenge validation Include for name: www.kitosdomain.com in: /etc/httpd/conf.d/kitosdomain.conf
2026-01-11 16:42:40,856:DEBUG:certbot_apache._internal.http_01:Adding a temporary challenge validation Include for name: None in: /etc/httpd/conf.d/ssl.conf
2026-01-11 16:42:40,856:DEBUG:certbot_apache.internal.http_01:writing a pre config file with text:
RewriteRule ^/.well-known/acme-challenge/([A-Za-z0-9-=]+)$ /var/lib/letsencrypt/http_challenges/$1 [END]
2026-01-11 16:42:40,857:DEBUG:certbot_apache._internal.http_01:writing a post config file with text:
RewriteEngine on
<Directory /var/lib/letsencrypt/http_challenges>
Require all granted
<Location /.well-known/acme-challenge>
Require all granted
2026-01-11 16:42:40,924:DEBUG:certbot.reverter:Creating backup of /etc/httpd/conf.d/kitosdomain.conf
2026-01-11 16:42:40,925:DEBUG:certbot.reverter:Creating backup of /etc/httpd/conf.d/ssl.conf
2026-01-11 16:42:44,051:DEBUG:acme.client:JWS payload:
b'{}'
2026-01-11 16:42:44,053:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/chall/2955412526/641639778556/d6rP2w:
{
"protected": "eyJhbGciOiAiUlMyNTYiLCAia2lkIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMjk1NTQxMjUyNiIsICJub25jZSI6ICJsWENLbmVxSm8wMlRWS3kyMkxaRjB2a3VYdlZmZURNZ3hRNXJTcXl1RlBtUm42VjRwY0kiLCAidXJsIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2NoYWxsLzI5NTU0MTI1MjYvNjQxNjM5Nzc4NTU2L2Q2clAydyJ9",
"signature": "N3huH35Nfz0HW1zlIgccSvKljoElrP-tKGrvS5iIORW91IRJiDg5EU5JeIWxkL6jDk23gI-lel-Y4lBDMOLyEww2Q5ALntcgsx4pxjEdSzdT9ZY2TI2FIfK9sFEG24sQ-jUU4sN6Z49pXbTVKqGJ5rCW2oJm-DsMF3-2WigrNtWGXHt1xCnvl1fUtX9buK_BqccUdmG4VeTo4SL3dJaK9NKn9QAAI7gfiSgOh9FXe0XxCSQD-vN4etBEVv3114Jy5NU8TKwTa__52UJM9gpzx9vUs2lQaKoC7pm6FH5YOmQNhuDLy3LZB49OhkjXk8nV4rJeWkTylIDaVP4iHFNqlg",
"payload": "e30"
}
2026-01-11 16:42:44,190:DEBUG:urllib3.connectionpool:https://acme-v02.api.letsencrypt.org:443 "POST /acme/chall/2955412526/641639778556/d6rP2w HTTP/1.1" 200 195
2026-01-11 16:42:44,190:DEBUG:acme.client:Received response:
HTTP 200
Server: nginx
Date: Sun, 11 Jan 2026 21:42:44 GMT
Content-Type: application/json
Content-Length: 195
Connection: keep-alive
Boulder-Requester: 2955412526
Cache-Control: public, max-age=0, no-cache
Link: https://acme-v02.api.letsencrypt.org/directory;rel="index", https://acme-v02.api.letsencrypt.org/acme/authz/2955412526/641639778556;rel="up"
Location: https://acme-v02.api.letsencrypt.org/acme/chall/2955412526/641639778556/d6rP2w
Replay-Nonce: Pihtai8mBRsmA3U5WbF-HSNHSSlEmp8K6KINHiqITUdWpdhliRQ
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
{
"type": "http-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall/2955412526/641639778556/d6rP2w",
"status": "pending",
"token": "TIm7sCdxnMQqAYxK6pAV1jEcjkzujqaCrm2LWg7ZNBg"
}
2026-01-11 16:42:44,190:DEBUG:acme.client:Storing nonce: Pihtai8mBRsmA3U5WbF-HSNHSSlEmp8K6KINHiqITUdWpdhliRQ
2026-01-11 16:42:44,191:INFO:certbot.internal.auth_handler:Waiting for verification...
2026-01-11 16:42:45,191:DEBUG:acme.client:JWS payload:
b''
2026-01-11 16:42:45,193:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/authz/2955412526/641639778556:
{
"protected": "eyJhbGciOiAiUlMyNTYiLCAia2lkIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMjk1NTQxMjUyNiIsICJub25jZSI6ICJQaWh0YWk4bUJSc21BM1U1V2JGLUhTTkhTU2xFbXA4SzZLSU5IaXFJVFVkV3BkaGxpUlEiLCAidXJsIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2F1dGh6LzI5NTU0MTI1MjYvNjQxNjM5Nzc4NTU2In0",
"signature": "jvLoDE8tLid52m4HaJ3zW0B_LRB8b3NG5NawFSlJH7T3iMq-bbhaeGLxRc3cwPVqfIQbFrx_buQ7VvNE27lIbt6oxMuUHkWjw1yd-ZaksxePX7Sq89bfFofhA67HEkKTD4G9hVoHELlUDQG1SMlEDfAYna8zBci6wRjTZxHompnCQCUf_-QH7tWSJ7QPTqZzUbMudhEA_o6onuk9LFjwVwVLHVuos2PD_a5W4wEF7akwUv6AOuvmyTA8CuQulTzZfqLtRd_T8o3S5ssDBzghenT2KOuLnTO3gAi1ORZV1weyGId_sfZdYzTJRxQiQdeusafZuENjXXvhdXe4jmnCA",
"payload": ""
}
2026-01-11 16:42:45,267:DEBUG:urllib3.connectionpool:https://acme-v02.api.letsencrypt.org:443 "POST /acme/authz/2955412526/641639778556 HTTP/1.1" 200 827
2026-01-11 16:42:45,268:DEBUG:acme.client:Received response:
HTTP 200
Server: nginx
Date: Sun, 11 Jan 2026 21:42:45 GMT
Content-Type: application/json
Content-Length: 827
Connection: keep-alive
Boulder-Requester: 2955412526
Cache-Control: public, max-age=0, no-cache
Link: https://acme-v02.api.letsencrypt.org/directory;rel="index"
Replay-Nonce: Pihtai8mG-AIVVlOKN5ZxKIXBRObkU7LmvvzoRCYC3GGoiS1tKU
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
{
"identifier": {
"type": "dns",
"value": "www.kitosdomain.com"
},
"status": "pending",
"expires": "2026-01-18T21:42:40Z",
"challenges": [
{
"type": "http-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall/2955412526/641639778556/d6rP2w",
"status": "pending",
"token": "TIm7sCdxnMQqAYxK6pAV1jEcjkzujqaCrm2LWg7ZNBg"
},
{
"type": "tls-alpn-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall/2955412526/641639778556/6maOgA",
"status": "pending",
"token": "TIm7sCdxnMQqAYxK6pAV1jEcjkzujqaCrm2LWg7ZNBg"
},
{
"type": "dns-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall/2955412526/641639778556/iGw4fw",
"status": "pending",
"token": "TIm7sCdxnMQqAYxK6pAV1jEcjkzujqaCrm2LWg7ZNBg"
}
]
}
2026-01-11 16:42:45,268:DEBUG:acme.client:Storing nonce: Pihtai8mG-AIVVlOKN5ZxKIXBRObkU7LmvvzoRCYC3GGoiS1tKU
2026-01-11 16:42:48,269:DEBUG:acme.client:JWS payload:
b''
2026-01-11 16:42:48,271:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/authz/2955412526/641639778556:
{
"protected": "eyJhbGciOiAiUlMyNTYiLCAia2lkIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMjk1NTQxMjUyNiIsICJub25jZSI6ICJQaWh0YWk4bUctQUlWVmxPS041WnhLSVhCUk9ia1U3TG12dnpvUkNZQzNHR29pUzF0S1UiLCAidXJsIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2F1dGh6LzI5NTU0MTI1MjYvNjQxNjM5Nzc4NTU2In0",
"signature": "U_ji2C3epwuNvdXogNuQp1noxY7RFCLfBPLKnkgF8ydnYDq3pw5ipg35f7to4dofvMtTk02iWGkj2cTxHx_LFbdcAkHQjn4oDmqHsBO21PJ0KZAclKO62ia9QokRnJbHQ2t7jcvSOIIjPDuCKyFTmiijMVFYMs93Oczx77x-IHi58kjxw3sYMphlerVdew6XR2Tdm_4SVT2A3Az7T-rBRA56OC9hjdnKa7Mkt5ZD5bq67L_R7yuNvGlJKMqEFHTWdYGolNthW0WSpr2VHg96rz18x6DX232xTh00WCb7bnySXWiKoOmUgr3pgKm_givyp5H-oH8BOpJZHUVlRpG5iw",
"payload": ""
}
2026-01-11 16:42:48,353:DEBUG:urllib3.connectionpool:https://acme-v02.api.letsencrypt.org:443 "POST /acme/authz/2955412526/641639778556 HTTP/1.1" 200 1063
2026-01-11 16:42:48,353:DEBUG:acme.client:Received response:
HTTP 200
Server: nginx
Date: Sun, 11 Jan 2026 21:42:48 GMT
Content-Type: application/json
Content-Length: 1063
Connection: keep-alive
Boulder-Requester: 2955412526
Cache-Control: public, max-age=0, no-cache
Link: https://acme-v02.api.letsencrypt.org/directory;rel="index"
Replay-Nonce: lXCKneqJm6Y30BELPFFvUiP49iPYrp2DvxxE_HN6tnlv1j-1enc
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
{
"identifier": {
"type": "dns",
"value": "www.kitosdomain.com"
},
"status": "invalid",
"expires": "2026-01-18T21:42:40Z",
"challenges": [
{
"type": "http-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall/2955412526/641639778556/d6rP2w",
"status": "invalid",
"validated": "2026-01-11T21:42:44Z",
"error": {
"type": "urn:ietf:params:acme:error:connection",
"detail": "24.172.29.130: Fetching http://www.kitosdomain.com/.well-known/acme-challenge/TIm7sCdxnMQqAYxK6pAV1jEcjkzujqaCrm2LWg7ZNBg: Error getting validation data",
"status": 400
},
"token": "TIm7sCdxnMQqAYxK6pAV1jEcjkzujqaCrm2LWg7ZNBg",
"validationRecord": [
{
"url": "http://www.kitosdomain.com/.well-known/acme-challenge/TIm7sCdxnMQqAYxK6pAV1jEcjkzujqaCrm2LWg7ZNBg",
"hostname": "www.kitosdomain.com",
"port": "80",
"addressesResolved": [
"24.172.29.130"
],
"addressUsed": "24.172.29.130"
}
]
}
]
}
2026-01-11 16:42:48,354:DEBUG:acme.client:Storing nonce: lXCKneqJm6Y30BELPFFvUiP49iPYrp2DvxxE_HN6tnlv1j-1enc
2026-01-11 16:42:48,354:INFO:certbot._internal.auth_handler:Challenge failed for domain www.kitosdomain.com
2026-01-11 16:42:48,355:INFO:certbot._internal.auth_handler:http-01 challenge for www.kitosdomain.com
2026-01-11 16:42:48,355:DEBUG:certbot._internal.display.obj:Notifying user:
Certbot failed to authenticate some domains (authenticator: apache). The Certificate Authority reported these problems:
Domain: www.kitosdomain.com
Type: connection
Detail: 24.172.29.130: Fetching http://www.kitosdomain.com/.well-known/acme-challenge/TIm7sCdxnMQqAYxK6pAV1jEcjkzujqaCrm2LWg7ZNBg: Error getting validation data
Hint: The Certificate Authority failed to verify the temporary Apache configuration changes made by Certbot. Ensure that the listed domains point to this Apache server and that it is accessible from the internet.
2026-01-11 16:42:48,357:DEBUG:certbot._internal.error_handler:Encountered exception:
Traceback (most recent call last):
File "/usr/lib/python3.14/site-packages/certbot/_internal/auth_handler.py", line 108, in handle_authorizations
self._poll_authorizations(authzrs, max_retries, max_time_mins, best_effort)
~~~~~~~~~~~~~~~~~~~~~~~~~^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3.14/site-packages/certbot/_internal/auth_handler.py", line 212, in _poll_authorizations
raise errors.AuthorizationError('Some challenges have failed.')
certbot.errors.AuthorizationError: Some challenges have failed.
2026-01-11 16:42:48,357:DEBUG:certbot._internal.error_handler:Calling registered functions
2026-01-11 16:42:48,357:INFO:certbot._internal.auth_handler:Cleaning up challenges
2026-01-11 16:42:48,498:DEBUG:certbot._internal.log:Exiting abnormally:
Traceback (most recent call last):
File "/usr/sbin/certbot", line 8, in
sys.exit(main())
~~~~^^
File "/usr/lib/python3.14/site-packages/certbot/main.py", line 19, in main
return internal_main.main(cli_args)
~~~~~~~~~~~~~~~~~~^^^^^^^^^^
File "/usr/lib/python3.14/site-packages/certbot/_internal/main.py", line 1879, in main
return config.func(config, plugins)
~~~~~~~~~~~^^^^^^^^^^^^^^^^^
File "/usr/lib/python3.14/site-packages/certbot/_internal/main.py", line 1435, in run
new_lineage = _get_and_save_cert(le_client, config, domains,
certname, lineage)
File "/usr/lib/python3.14/site-packages/certbot/_internal/main.py", line 143, in _get_and_save_cert
lineage = le_client.obtain_and_enroll_certificate(domains, certname)
File "/usr/lib/python3.14/site-packages/certbot/_internal/client.py", line 524, in obtain_and_enroll_certificate
cert, chain, key, _ = self.obtain_certificate(domains)
~~~~~~~~~~~~~~~~~~~~~~~^^^^^^^^^
File "/usr/lib/python3.14/site-packages/certbot/_internal/client.py", line 425, in obtain_certificate
orderr = self._get_order_and_authorizations(csr.data, self.config.allow_subset_of_names)
File "/usr/lib/python3.14/site-packages/certbot/_internal/client.py", line 503, in _get_order_and_authorizations
authzr = self.auth_handler.handle_authorizations(orderr, self.config, best_effort)
File "/usr/lib/python3.14/site-packages/certbot/_internal/auth_handler.py", line 108, in handle_authorizations
self._poll_authorizations(authzrs, max_retries, max_time_mins, best_effort)
~~~~~~~~~~~~~~~~~~~~~~~~~^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3.14/site-packages/certbot/_internal/auth_handler.py", line 212, in _poll_authorizations
raise errors.AuthorizationError('Some challenges have failed.')
certbot.errors.AuthorizationError: Some challenges have failed.
2026-01-11 16:42:48,501:ERROR:certbot._internal.log:Some challenges have failed.