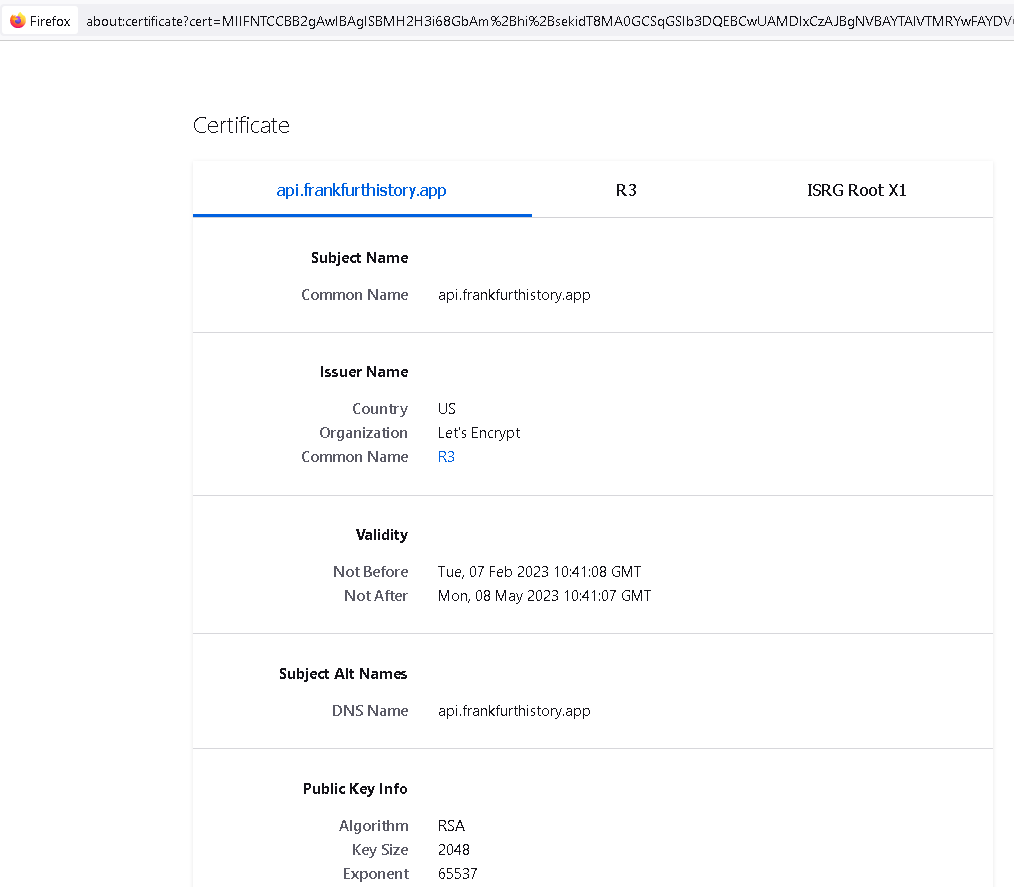
Hello,
i got the problem, that the renewal of the letsencrypt-certificate went well and i do see the new certificate, while attempting a connection via openssl. But openssl (as the browser) still complains, that the certificate has expired.
Certbot found, that the present certificate was not due to renewal, so i did a forced renewal. This went well again, but the result ist still the same: crtificate expired for browser and openssl.
I have no clue why. Any hint is much appreciated!
Cheers, Georg
Please fill out the fields below so we can help you better. Note: you must provide your domain name to get help. Domain names for issued certificates are all made public in Certificate Transparency logs (e.g. crt.sh | example.com), so withholding your domain name here does not increase secrecy, but only makes it harder for us to provide help.
My domain is: api.frankfurthistory.app
I ran this command:
openssl s_client -connect api.frankfurthistory.app:443
It produced this output:
CONNECTED(00000005)
depth=1 O = Digital Signature Trust Co., CN = DST Root CA X3
verify error:num=10:certificate has expired
notAfter=Sep 30 14:01:15 2021 GMT
Then i tried:
certbot renew
It produced this output:
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Processing /etc/letsencrypt/renewal/api.frankfurthistory.app.conf
Certificate not yet due for renewal
The following certificates are not due for renewal yet:
/etc/letsencrypt/live/api.frankfurthistory.app/fullchain.pem expires on 2023-04-04 (skipped)
No renewals were attempted.
I restarted the apache several times, and after that i get the new certificate persented when i connect via openssl, still it is complaining, that the certificate has expired.
My web server is (include version):
Apache apache2 2.4.38-3+deb10u7
The operating system my web server runs on is (include version):
debian/expat 2.2.6-2+deb10u1 in a docker-container
My hosting provider, if applicable, is:
I can login to a root shell on my machine (yes or no, or I don't know):
yes
I'm using a control panel to manage my site (no, or provide the name and version of the control panel):
no
The version of my client is (e.g. output of certbot --version or certbot-auto --version if you're using Certbot):
certbot 1.32.2