Hi,
I have a server with 11 SAN certificates, each SAN has 100 domains (or close to it).
I am receiving this error when issuing any given SAN certificate:
Create new order error. Le_OrderFinalize not found. {
"type": "urn:ietf:params:acme:error:rateLimited",
"detail": "Error creating new order :: too many currently pending authorizations: see https://letsencrypt.org/docs/rate-limits/",
"status": 429
}
- I can run the
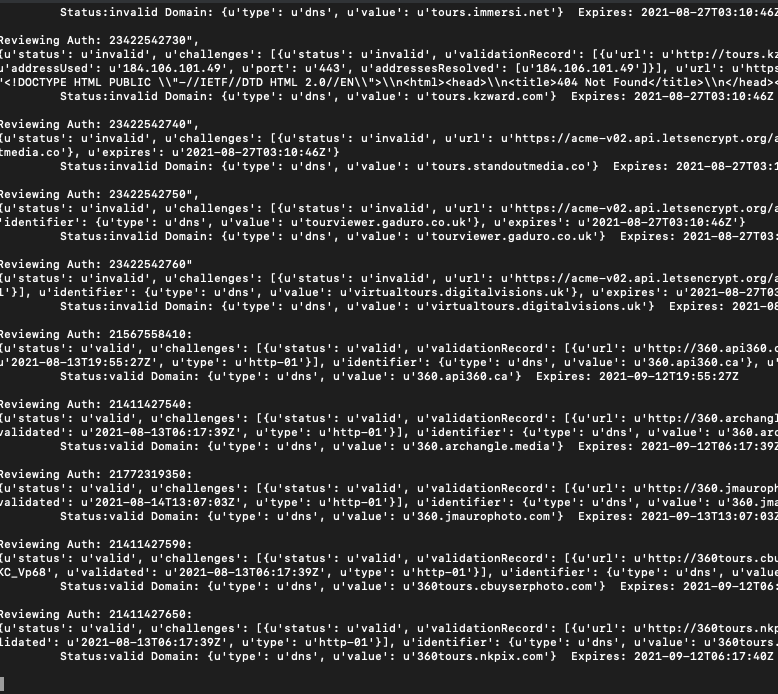
issuecommand with--stagingflag enabled and I get no errors. - I reviewed the letsEncrypt.log for open
authzrequests, but every time I observe a POST I always see a status 200 returned. Example:
2021-08-20 03:11:24,622:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/authz-v3/23422690450:
2021-08-20 03:11:24,722:DEBUG:urllib3.connectionpool:https://acme-v02.api.letsencrypt.org:443 "POST /acme/authz-v3/23422690450 HTTP/1.1" 200 794
- I reviewed the acme.sh.log for open
authzrequests, and see similar. Example:
[Fri Aug 20 04:09:27 UTC 2021] POST
[Fri Aug 20 04:09:27 UTC 2021] _post_url='https://acme-staging-v02.api.letsencrypt.org/acme/authz-v3/312028258'
[Fri Aug 20 04:09:27 UTC 2021] _CURL='curl -L --silent --dump-header /home/sslService/.acme.sh/http.header -g '
[Fri Aug 20 04:09:27 UTC 2021] _ret='0'
[Fri Aug 20 04:09:27 UTC 2021] code='200'
I'm not sure where to go from here. Any help or guidance is appreciated. This started in the past two days. Thanks for the great service and tools.
Other information
My domain is:
cert11.cloudpano.com
I ran this command:
acme.sh --issue --log -w [dir] -k 4096 --force -d cert11.cloudpano.com -d -our.homesite360.com -d hs360example.homesite360.com -d tours.4dtour.me -d [...other domains] --debug
It produced this output:
[Fri Aug 20 04:13:44 UTC 2021] Lets find script dir.
[Fri Aug 20 04:13:45 UTC 2021] _SCRIPT_='/home/sslService/.acme.sh/acme.sh'
[Fri Aug 20 04:13:45 UTC 2021] _script='/home/sslService/.acme.sh/acme.sh'
[Fri Aug 20 04:13:45 UTC 2021] _script_home='/home/sslService/.acme.sh'
[Fri Aug 20 04:13:45 UTC 2021] Using config home:/home/sslService/.acme.sh
https://github.com/acmesh-official/acme.sh
v2.8.6
[Fri Aug 20 04:13:45 UTC 2021] Running cmd: issue
[Fri Aug 20 04:13:45 UTC 2021] _main_domain='cert11.cloudpano.com'
[Fri Aug 20 04:13:45 UTC 2021] _alt_domains='tour.homesite360.com,hs360example.homesite360.com,tours.4dtour.me,[etc...]'
[Fri Aug 20 04:13:45 UTC 2021] Using config home:/home/sslService/.acme.sh
[Fri Aug 20 04:13:45 UTC 2021] ACME_DIRECTORY='https://acme-v02.api.letsencrypt.org/directory'
[Fri Aug 20 04:13:45 UTC 2021] DOMAIN_PATH='/home/sslService/.acme.sh/cert11.cloudpano.com'
[Fri Aug 20 04:13:45 UTC 2021] Using ACME_DIRECTORY: https://acme-v02.api.letsencrypt.org/directory
[Fri Aug 20 04:13:45 UTC 2021] _init api for server: https://acme-v02.api.letsencrypt.org/directory
[Fri Aug 20 04:13:45 UTC 2021] GET
[Fri Aug 20 04:13:45 UTC 2021] url='https://acme-v02.api.letsencrypt.org/directory'
[Fri Aug 20 04:13:45 UTC 2021] timeout=
[Fri Aug 20 04:13:45 UTC 2021] _CURL='curl -L --silent --dump-header /home/sslService/.acme.sh/http.header -g '
[Fri Aug 20 04:13:45 UTC 2021] ret='0'
[Fri Aug 20 04:13:45 UTC 2021] ACME_KEY_CHANGE='https://acme-v02.api.letsencrypt.org/acme/key-change'
[Fri Aug 20 04:13:45 UTC 2021] ACME_NEW_AUTHZ
[Fri Aug 20 04:13:45 UTC 2021] ACME_NEW_ORDER='https://acme-v02.api.letsencrypt.org/acme/new-order'
[Fri Aug 20 04:13:45 UTC 2021] ACME_NEW_ACCOUNT='https://acme-v02.api.letsencrypt.org/acme/new-acct'
[Fri Aug 20 04:13:45 UTC 2021] ACME_REVOKE_CERT='https://acme-v02.api.letsencrypt.org/acme/revoke-cert'
[Fri Aug 20 04:13:45 UTC 2021] ACME_AGREEMENT='https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf'
[Fri Aug 20 04:13:45 UTC 2021] ACME_NEW_NONCE='https://acme-v02.api.letsencrypt.org/acme/new-nonce'
[Fri Aug 20 04:13:45 UTC 2021] ACME_VERSION='2'
[Fri Aug 20 04:13:45 UTC 2021] Le_NextRenewTime='1634530331'
[Fri Aug 20 04:13:45 UTC 2021] _on_before_issue
[Fri Aug 20 04:13:45 UTC 2021] _chk_main_domain='cert11.cloudpano.com'
[Fri Aug 20 04:13:45 UTC 2021] _chk_alt_domains='tour.homesite360.com,hs360example.homesite360.com,tours.4dtour.me,[etc...]'
[Fri Aug 20 04:13:45 UTC 2021] Le_LocalAddress
[Fri Aug 20 04:13:45 UTC 2021] d='cert11.cloudpano.com'
[Fri Aug 20 04:13:45 UTC 2021] Check for domain='cert11.cloudpano.com'
[Fri Aug 20 04:13:45 UTC 2021] _currentRoot='/home/user/big-data-homes/build'
[Fri Aug 20 04:13:45 UTC 2021] d='tour.homesite360.com'
[Fri Aug 20 04:13:45 UTC 2021] Check for domain='tour.homesite360.com'
[Fri Aug 20 04:13:45 UTC 2021] _currentRoot='/home/user/big-data-homes/build'
[Fri Aug 20 04:13:45 UTC 2021] d='hs360example.homesite360.com'
[Fri Aug 20 04:13:45 UTC 2021] Check for domain='hs360example.homesite360.com'
[Fri Aug 20 04:13:45 UTC 2021] _currentRoot='/home/user/big-data-homes/build'
[Fri Aug 20 04:13:45 UTC 2021] d='tours.4dtour.me'
[Fri Aug 20 04:13:45 UTC 2021] Check for domain='tours.4dtour.me'
[etc...]
[Fri Aug 20 04:13:47 UTC 2021] Getting domain auth token for each domain
[Fri Aug 20 04:13:47 UTC 2021] d='tour.homesite360.com'
[Fri Aug 20 04:13:47 UTC 2021] d='hs360example.homesite360.com'
[Fri Aug 20 04:13:47 UTC 2021] d='tours.4dtour.me'
[etc...]
[Fri Aug 20 04:13:48 UTC 2021] d='tours.mozesphotography.com'
[Fri Aug 20 04:13:48 UTC 2021] d
[Fri Aug 20 04:13:48 UTC 2021] url='https://acme-v02.api.letsencrypt.org/acme/new-order'
[Fri Aug 20 04:13:48 UTC 2021] payload='{"identifiers": [{"type":"dns","value":"cert11.cloudpano.com"},{"type":"dns","value":"tour.homesite360.com"},{"type":"dns","value":"hs360example.homesite360.com"},{"type":"dns","value":"tours.4dtour.me"},[etc...],{"type":"dns","value":"tours.mozesphotography.com"}]}'
[Fri Aug 20 04:13:48 UTC 2021] RSA key
[Fri Aug 20 04:13:48 UTC 2021] HEAD
[Fri Aug 20 04:13:48 UTC 2021] _post_url='https://acme-v02.api.letsencrypt.org/acme/new-nonce'
[Fri Aug 20 04:13:48 UTC 2021] _CURL='curl -L --silent --dump-header /home/sslService/.acme.sh/http.header -g -I '
[Fri Aug 20 04:13:49 UTC 2021] _ret='0'
[Fri Aug 20 04:13:49 UTC 2021] POST
[Fri Aug 20 04:13:49 UTC 2021] _post_url='https://acme-v02.api.letsencrypt.org/acme/new-order'
[Fri Aug 20 04:13:49 UTC 2021] _CURL='curl -L --silent --dump-header /home/sslService/.acme.sh/http.header -g '
[Fri Aug 20 04:13:49 UTC 2021] _ret='0'
[Fri Aug 20 04:13:49 UTC 2021] code='429'
[Fri Aug 20 04:13:49 UTC 2021] Le_LinkOrder
[Fri Aug 20 04:13:49 UTC 2021] Le_OrderFinalize
[Fri Aug 20 04:13:49 UTC 2021] Create new order error. Le_OrderFinalize not found. {
"type": "urn:ietf:params:acme:error:rateLimited",
"detail": "Error creating new order :: too many currently pending authorizations: see https://letsencrypt.org/docs/rate-limits/",
"status": 429
}
[Fri Aug 20 04:13:49 UTC 2021] pid
[Fri Aug 20 04:13:49 UTC 2021] No need to restore nginx, skip.
[Fri Aug 20 04:13:49 UTC 2021] _clearupdns
[Fri Aug 20 04:13:49 UTC 2021] dns_entries
[Fri Aug 20 04:13:49 UTC 2021] skip dns.
[Fri Aug 20 04:13:49 UTC 2021] _on_issue_err
[Fri Aug 20 04:13:49 UTC 2021] Please check log file for more details: /home/sslService/.acme.sh/acme.sh.log
[Fri Aug 20 04:13:49 UTC 2021] socat doesn't exists.
[Fri Aug 20 04:13:49 UTC 2021] Diagnosis versions:
openssl:openssl
OpenSSL 1.1.1 11 Sep 2018
apache:
apache doesn't exists.
nginx:
nginx version: nginx/1.14.0 (Ubuntu)
built with OpenSSL 1.1.1 11 Sep 2018
TLS SNI support enabled
configure arguments: --with-cc-opt='-g -O2 -fdebug-prefix-map=/build/nginx-H4cN7P/nginx-1.14.0=. -fstack-protector-strong -Wformat -Werror=format-security -fPIC -Wdate-time -D_FORTIFY_SOURCE=2' --with-ld-opt='-Wl,-Bsymbolic-functions -Wl,-z,relro -Wl,-z,now -fPIC' --prefix=/usr/share/nginx --conf-path=/etc/nginx/nginx.conf --http-log-path=/var/log/nginx/access.log --error-log-path=/var/log/nginx/error.log --lock-path=/var/lock/nginx.lock --pid-path=/run/nginx.pid --modules-path=/usr/lib/nginx/modules --http-client-body-temp-path=/var/lib/nginx/body --http-fastcgi-temp-path=/var/lib/nginx/fastcgi --http-proxy-temp-path=/var/lib/nginx/proxy --http-scgi-temp-path=/var/lib/nginx/scgi --http-uwsgi-temp-path=/var/lib/nginx/uwsgi --with-debug --with-pcre-jit --with-http_ssl_module --with-http_stub_status_module --with-http_realip_module --with-http_auth_request_module --with-http_v2_module --with-http_dav_module --with-http_slice_module --with-threads --with-http_addition_module --with-http_geoip_module=dynamic --with-http_gunzip_module --with-http_gzip_static_module --with-http_image_filter_module=dynamic --with-http_sub_module --with-http_xslt_module=dynamic --with-stream=dynamic --with-stream_ssl_module --with-mail=dynamic --with-mail_ssl_module
socat:
My web server is (include version):
nginx/1.14.0 (Ubuntu)
The operating system my web server runs on is (include version):
Ubuntu 18.04.1 LTS
My hosting provider, if applicable, is:
Digital Ocean
I can login to a root shell on my machine (yes or no, or I don't know):
yes
I'm using a control panel to manage my site (no, or provide the name and version of the control panel):
no
The version of my client is (e.g. output of certbot --version or certbot-auto --version if you're using Certbot):
certbot 0.26.1
acme.sh v2.8.6