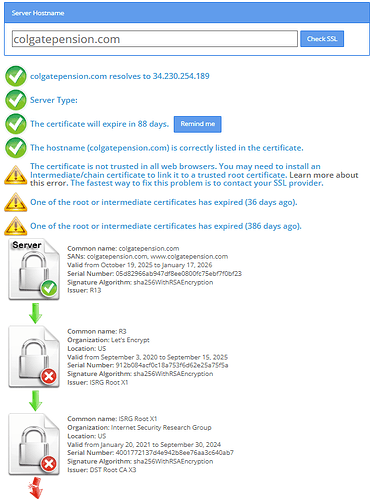
Hi Team,
I am using Lets encrypt certificates for all non www domains and currently we are facing The Certificate is not trusted in all web browsers issue.
The non www domains SSL are working intermittently. Mostly failing for some regions with SSL error that your connection is not private.
If checked through SSL checker it shows root or intermediate certs has expired.
Please find the below screenshot for your reference
My domain is: colgatepension.com
My web server is (include version): Apache/2.4.64 ()
The operating system my web server runs on is (include version): Amazon Linux 2
I can login to a root shell on my machine (yes or no, or I don't know): Yes
The version of my client is (e.g. output of certbot --version or certbot-auto --version if you're using Certbot): certbot 1.29.0
Just for reference if needed
SSLCertificateFile /opt/www/conf/certs/fullchain.pem
SSLCertificateKeyFile /opt/www/conf/certs/privkey.pem
Please note this is happening for our 2000 + non www sites which is very critical issue for us and needs to be resolved immediately with highest priority.
Please let me know the solution for this with the steps required to fix this.
Awaiting for your response.