Hello ,
My domain is crowd-genie.com i have hosted it using the firebase. I need to integrate a third part plugin it said requriment is to have a SSL certificat with data encipherment i asked the firebase Support team for upgrade of the certificate to data encipherment but they couldn’t help me out.I need to know what is data encipherment and how to update my SSL certificate to it.
Thank you
Hello Harkesh 
Might I ask which third party plug-in so that we may better evaluate the context? To me, “data encipherment” is just a long way of saying “encryption”. It could be that they are referring to encrypting stored data rather than encrypting data in transit, which is what an SSL/TLS certificate is used for. Please provide more clarity. Perhaps a link to the requirement?
What’s the third party plugin?
I don’t think you will be able to find any publicly trusted CA which will be willing to sign certificates with the dataEncipherment key usage. (Edit: turns out there’s a few but Let’s Encrypt isn’t one of them).
That would just be bare encryption using your certificate private key, which nobody does anymore due to it being quite dangerous. keyEncipherment is provided so that you can encrypt an encryption key, and then perform encryption using that.
I feel like whatever software wants that key usage probably expects you to give it a self-signed certificate or use a private PKI.
The Third party is SINGPASS it is a Singapore Government https://www.singpass.gov.sg/myinfo/intro.
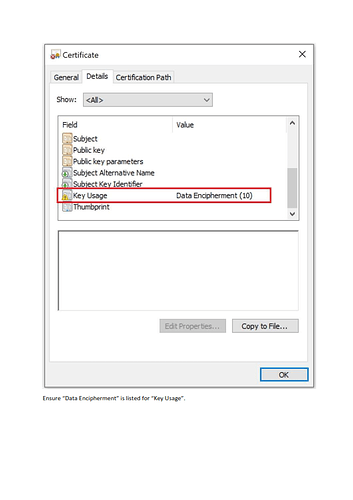
They sent the Requriment as the above Screen Shot to have an SSL in the above formate
That’s usually only seen in custom application protocols. Let’s Encrypt only offers Key Encipherment certificates, but some other companies like Digicert do offer Data Encipherment certificates.
Yes, I don’t believe Let’s Encrypt will be able to help you with this. The Key Usage field is a rather subtle policy decision for a certificate authority.
It might be interesting to know why Singpass wants this relatively unusual feature. I’m not quite sure why they expect it to provide better data security than a regular TLS connection.
I presume the rationale for choosing not to sign Data Encipherment (rather than allowing a subscriber to request it in a CSR) is that we’re confident Data Encipherment is a bad idea and hopefully not signing certificates for it discourages people from actually doing it?
Certificate’s Key Usage is defined in RFC 5280.
Public Key Cryptography is usually used for encrypting data in transit during communications between two parties, to ensure that only your intended recipient is able to read the data, without having to negotiate a shared secret. Which is why it uses 2 different cryptographic keys - private key and public key, with recipient being able to openly share their public key.
However, Public Key Cryptography is very computationally intensive, and also would require four keys during two-way communication - a key pair for each participant.
So to simplify things, real-time communication protocols such as SSL and TLS create and negotiate a small shared secret key instead during negotiation, and use Public Key Cryptography to exchange this key. All data is then encrypted using this shared key, which works a lot faster and a lot more secure (AES with 256-bit key is equivalent in strength to RSA with 15360-bit keys). The negotiation also only requires one participant to have a Public Key Cryptography key pair - a lot simpler for non-technical clients.
This is why SSL and TLS require certificates with keyEncipherment Key Usage.
Using Public Key Cryptography to encrypt data at rest to ensure that only yourself can read the data does not make much sense - using a single secret key instead of a key pair is both simpler, a lot faster, and more secure.
The only useful scenario would be for non-real-time communication where you want to encrypt data so that only someone specific is able to read it later when they access it.
However, even in such scenarios it is still a lot quicker to generate a secret key, use it for data encryption, and then use Public Key Cryptography to encrypt only the secret key and attach it to the data which it was used to encrypt - e.g. S/MIME used for non-real-time e-mail exchange between recipients (e-mail is not real-time, because recipient can be asleep or on vacation when the email is sent).
This is why certificates with dataEncipherment Key Usage are not common.
Also these types of certificates typically would be used to encrypt data by humans, not by servers.
Let’s Encrypt automatic certificate issuance process is able to authenticate only servers by their hostname, it can’t authenticate human identities by their name.
Issuing certificates with with dataEncipherment Key Usage to servers could result in incorrect certificate use, which you want to avoid.
Hope this makes sense.
If I were the OP, I would ask Singpass for these details and some examples before proceeding.
I looked up Singpass, and it's Singapore's official government online services portal. I would not be surprised if their requirement for the data encipherment certificate is for a non-SSL/TLS context, where it makes sense, and not for encoding HTTPs traffic.
I absolutely could be wrong, but...
- The image above shows ONLY data encipherment
- The certificate transparency logs show BOTH DataEncipherment and KeyEncipherment on the
singpass.gov.sgcertificates
I have a feeling they want to ensure application data is encrypted with data encipherment for compliance, and are not directly concerned with https. Again, I could very well be wrong, but given the info I've seen... this makes some sense.
I think it might be to avoid Perfect Forward Secrecy at all costs.
If they're an endpoint of the conversation, why do they care whether the data remains recoverable by the other endpoint later or not?
I don't think their concern for supporting Data Encipherment is in a TLS context. Their own site's keys have Key+Data and the https connection seemed to use Key; I think they require DataEncipherment for use in other contexts.
This topic was automatically closed 30 days after the last reply. New replies are no longer allowed.