Please fill out the fields below so we can help you better. Note: you must provide your domain name to get help. Domain names for issued certificates are all made public in Certificate Transparency logs (e.g. crt.sh | example.com), so withholding your domain name here does not increase secrecy, but only makes it harder for us to provide help.
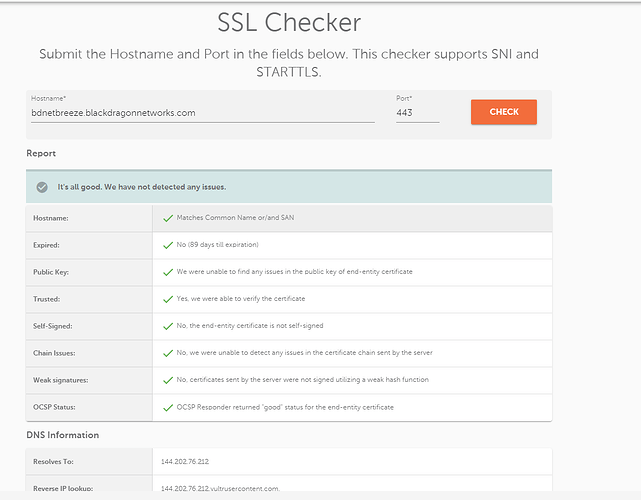
My domain is:bdnetbreeze.blackdragonnetworks.com
I ran this command:certbot
It produced this output:
How would you like to authenticate and install certificates?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: Apache Web Server plugin (apache)
2: Nginx Web Server plugin (nginx)
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 1
Plugins selected: Authenticator apache, Installer apache
Starting new HTTPS connection (1): acme-v02.api.letsencrypt.org
No names were found in your configuration files. Please enter in your domain
name(s) (comma and/or space separated) (Enter 'c' to cancel): bdnetbreeze.blackdragonnetworks.com
Cert is due for renewal, auto-renewing...
Renewing an existing certificate for bdnetbreeze.blackdragonnetworks.com
Performing the following challenges:
http-01 challenge for bdnetbreeze.blackdragonnetworks.com
Cleaning up challenges
Unable to find a virtual host listening on port 80 which is currently needed for Certbot to prove to the CA that you control your domain. Please add a virtual host for port 80.
Here's the log file:
root@bdnetbreeze letsencrypt]# cat letsencrypt.log
2023-09-14 17:34:16,605:DEBUG:certbot._internal.main:certbot version: 1.11.0
2023-09-14 17:34:16,605:DEBUG:certbot._internal.main:Location of certbot entry point: /usr/bin/certbot
2023-09-14 17:34:16,605:DEBUG:certbot._internal.main:Arguments: []
2023-09-14 17:34:16,605:DEBUG:certbot._internal.main:Discovered plugins: PluginsRegistry(PluginEntryPoint#apache,PluginEntryPoint#manual,PluginEntryPoint#nginx,PluginEntryPoint#null,PluginEntryPoint#standalone,PluginEntryPoint#webroot)
2023-09-14 17:34:16,620:DEBUG:certbot._internal.log:Root logging level set at 20
2023-09-14 17:34:16,620:INFO:certbot._internal.log:Saving debug log to /var/log/letsencrypt/letsencrypt.log
2023-09-14 17:34:16,620:DEBUG:certbot._internal.plugins.selection:Requested authenticator None and installer None
2023-09-14 17:34:16,716:DEBUG:certbot_apache._internal.configurator:Apache version is 2.4.6
2023-09-14 17:34:17,151:DEBUG:certbot._internal.plugins.selection:Multiple candidate plugins: * apache
Description: Apache Web Server plugin
Interfaces: IAuthenticator, IInstaller, IPlugin
Entry point: apache = certbot_apache._internal.entrypoint:ENTRYPOINT
Initialized: <certbot_apache._internal.override_centos.CentOSConfigurator object at 0x7fe643f5b790>
Prep: True
* nginx
Description: Nginx Web Server plugin
Interfaces: IAuthenticator, IInstaller, IPlugin
Entry point: nginx = certbot_nginx._internal.configurator:NginxConfigurator
Initialized: <certbot_nginx._internal.configurator.NginxConfigurator object at 0x7fe643f5bd50>
Prep: True
2023-09-14 17:34:24,495:DEBUG:certbot._internal.plugins.selection:Selected authenticator <certbot_nginx._internal.configurator.NginxConfigurator object at 0x7fe643f5bd50> and installer <certbot_nginx._internal.configurator.NginxConfigurator object at 0x7fe643f5bd50>
2023-09-14 17:34:24,496:INFO:certbot._internal.plugins.selection:Plugins selected: Authenticator nginx, Installer nginx
2023-09-14 17:34:24,526:DEBUG:certbot._internal.main:Picked account: <Account(RegistrationResource(body=Registration(status=None, terms_of_service_agreed=None, agreement=None, only_return_existing=None, contact=(), key=None, external_account_binding=None), uri=u'https://acme-v02.api.letsencrypt.org/acme/acct/105472978', new_authzr_uri=None, terms_of_service=None), 73f5f7d43c9116eea6f3a761ed7e7155, Meta(creation_host=u'bdnetbreeze', register_to_eff=None, creation_dt=datetime.datetime(2020, 12, 7, 23, 12, 27, tzinfo=<UTC>)))>
2023-09-14 17:34:24,528:DEBUG:acme.client:Sending GET request to https://acme-v02.api.letsencrypt.org/directory.
2023-09-14 17:34:24,535:INFO:urllib3.connectionpool:Starting new HTTPS connection (1): acme-v02.api.letsencrypt.org
2023-09-14 17:34:24,732:DEBUG:urllib3.connectionpool:"GET /directory HTTP/1.1" 200 752
2023-09-14 17:34:24,733:DEBUG:acme.client:Received response:
HTTP 200
content-length: 752
strict-transport-security: max-age=604800
server: nginx
connection: keep-alive
cache-control: public, max-age=0, no-cache
date: Thu, 14 Sep 2023 22:34:24 GMT
x-frame-options: DENY
content-type: application/json
{
"S_ZuFDZMH-Y": "https://community.letsencrypt.org/t/adding-random-entries-to-the-directory/33417",
"keyChange": "https://acme-v02.api.letsencrypt.org/acme/key-change",
"meta": {
"caaIdentities": [
"letsencrypt.org"
],
"termsOfService": "https://letsencrypt.org/documents/LE-SA-v1.3-September-21-2022.pdf",
"website": "https://letsencrypt.org"
},
"newAccount": "https://acme-v02.api.letsencrypt.org/acme/new-acct",
"newNonce": "https://acme-v02.api.letsencrypt.org/acme/new-nonce",
"newOrder": "https://acme-v02.api.letsencrypt.org/acme/new-order",
"renewalInfo": "https://acme-v02.api.letsencrypt.org/draft-ietf-acme-ari-01/renewalInfo/",
"revokeCert": "https://acme-v02.api.letsencrypt.org/acme/revoke-cert"
}
2023-09-14 17:34:28,062:DEBUG:certbot._internal.plugins.selection:Requested authenticator <certbot._internal.cli.cli_utils._Default object at 0x7fe649d70c90> and installer <certbot._internal.cli.cli_utils._Default object at 0x7fe649d70c90>
2023-09-14 17:34:28,078:DEBUG:certbot.ocsp:Querying OCSP for /etc/letsencrypt/archive/bdnetbreeze.blackdragonnetworks.com/cert16.pem
2023-09-14 17:34:28,079:DEBUG:certbot.ocsp:openssl ocsp -no_nonce -issuer /etc/letsencrypt/archive/bdnetbreeze.blackdragonnetworks.com/chain16.pem -cert /etc/letsencrypt/archive/bdnetbreeze.blackdragonnetworks.com/cert16.pem -CAfile /etc/letsencrypt/archive/bdnetbreeze.blackdragonnetworks.com/chain16.pem -verify_other /etc/letsencrypt/archive/bdnetbreeze.blackdragonnetworks.com/chain16.pem -trust_other -timeout 10 -header Host r3.o.lencr.org -url http://r3.o.lencr.org
2023-09-14 17:34:28,099:DEBUG:certbot._internal.storage:Should renew, less than 30 days before certificate expiry 2023-10-03 21:01:39 UTC.
2023-09-14 17:34:28,099:INFO:certbot._internal.renewal:Cert is due for renewal, auto-renewing...
2023-09-14 17:34:28,100:DEBUG:certbot.display.util:Notifying user: Renewing an existing certificate for bdnetbreeze.blackdragonnetworks.com
2023-09-14 17:34:28,191:DEBUG:certbot.crypto_util:Generating RSA key (2048 bits): /etc/letsencrypt/keys/0066_key-certbot.pem
2023-09-14 17:34:28,194:DEBUG:certbot.crypto_util:Creating CSR: /etc/letsencrypt/csr/0066_csr-certbot.pem
2023-09-14 17:34:28,194:DEBUG:acme.client:Requesting fresh nonce
2023-09-14 17:34:28,194:DEBUG:acme.client:Sending HEAD request to https://acme-v02.api.letsencrypt.org/acme/new-nonce.
2023-09-14 17:34:28,244:DEBUG:urllib3.connectionpool:"HEAD /acme/new-nonce HTTP/1.1" 200 0
2023-09-14 17:34:28,245:DEBUG:acme.client:Received response:
HTTP 200
strict-transport-security: max-age=604800
server: nginx
connection: keep-alive
link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
cache-control: public, max-age=0, no-cache
date: Thu, 14 Sep 2023 22:34:28 GMT
x-frame-options: DENY
replay-nonce: jHwWLmW4EjZtLo5ZAdn5Ilne1w50mqV9UObIbm0c9Npr3kC6aqM
2023-09-14 17:34:28,245:DEBUG:acme.client:Storing nonce: jHwWLmW4EjZtLo5ZAdn5Ilne1w50mqV9UObIbm0c9Npr3kC6aqM
2023-09-14 17:34:28,245:DEBUG:acme.client:JWS payload:
{
"identifiers": [
{
"type": "dns",
"value": "bdnetbreeze.blackdragonnetworks.com"
}
]
}
2023-09-14 17:34:28,247:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/new-order:
{
"protected": "eyJub25jZSI6ICJqSHdXTG1XNEVqWnRMbzVaQWRuNUlsbmUxdzUwbXFWOVVPYklibTBjOU5wcjNrQzZhcU0iLCAidXJsIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL25ldy1vcmRlciIsICJraWQiOiAiaHR0cHM6Ly9hY21lLXYwMi5hcGkubGV0c2VuY3J5cHQub3JnL2FjbWUvYWNjdC8xMDU0NzI5NzgiLCAiYWxnIjogIlJTMjU2In0",
"payload": "ewogICJpZGVudGlmaWVycyI6IFsKICAgIHsKICAgICAgInR5cGUiOiAiZG5zIiwgCiAgICAgICJ2YWx1ZSI6ICJiZG5ldGJyZWV6ZS5ibGFja2RyYWdvbm5ldHdvcmtzLmNvbSIKICAgIH0KICBdCn0",
"signature": "1n7p8eP1fA4Bk3ZV5FLPIlamGRiJG4PDjzCOqpOplmuiO4dyXZcSJJdLkYY6sMs9JDA0HsKw2RWltIdK71isEc7rLvlXyFPecEvGoE_15JAYgoZZdk28rNjI_gSeYN6QzbPFMrwVh2XocrnuGtnUCT4ZnmXJ-0iLcK70_MpDIIPeZFEUhu0cpiXY0a1IUhiFRVjSdxB_47dbPCUDtJq_Zg2LLbIphxArLixXmeCM7pl_hlTiZXBUiZ8laOkDloI2UhMc4mLlbKqLYs7jzmhrcPGiIJdgA-PD8iczIzT1C9wpjS6dOBGlr6YnYG2ezYV_pl2MB2lNRqiqCFtDgRwNtQ"
}
2023-09-14 17:34:28,328:DEBUG:urllib3.connectionpool:"POST /acme/new-order HTTP/1.1" 201 360
2023-09-14 17:34:28,328:DEBUG:acme.client:Received response:
HTTP 201
content-length: 360
cache-control: public, max-age=0, no-cache
strict-transport-security: max-age=604800
server: nginx
connection: keep-alive
link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
location: https://acme-v02.api.letsencrypt.org/acme/order/105472978/208415540586
boulder-requester: 105472978
date: Thu, 14 Sep 2023 22:34:28 GMT
x-frame-options: DENY
content-type: application/json
replay-nonce: jHwWLmW4j_FDKlangJLvymSNUHHElV0_9Glj00IyDIK7bVTtXF0
{
"status": "pending",
"expires": "2023-09-21T22:34:28Z",
"identifiers": [
{
"type": "dns",
"value": "bdnetbreeze.blackdragonnetworks.com"
}
],
"authorizations": [
"https://acme-v02.api.letsencrypt.org/acme/authz-v3/264476644846"
],
"finalize": "https://acme-v02.api.letsencrypt.org/acme/finalize/105472978/208415540586"
}
2023-09-14 17:34:28,328:DEBUG:acme.client:Storing nonce: jHwWLmW4j_FDKlangJLvymSNUHHElV0_9Glj00IyDIK7bVTtXF0
2023-09-14 17:34:28,329:DEBUG:acme.client:JWS payload:
2023-09-14 17:34:28,330:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/authz-v3/264476644846:
{
"protected": "eyJub25jZSI6ICJqSHdXTG1XNGpfRkRLbGFuZ0pMdnltU05VSEhFbFYwXzlHbGowMEl5RElLN2JWVHRYRjAiLCAidXJsIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2F1dGh6LXYzLzI2NDQ3NjY0NDg0NiIsICJraWQiOiAiaHR0cHM6Ly9hY21lLXYwMi5hcGkubGV0c2VuY3J5cHQub3JnL2FjbWUvYWNjdC8xMDU0NzI5NzgiLCAiYWxnIjogIlJTMjU2In0",
"payload": "",
"signature": "tSgRwfZFHQmXMJbZ3meJ_h0QjHy6XgqM_Dd09xGBqRi66kUScqYdRjiOlljf8uTVyJEqbncElu_Lz-GhB7W7XPcA-ZJrnkacy13DmUU0BMX7QpGA3k8TrIGrKGt_nsZNWUWswN-lOg9xHFSlZilRoDJiw2Nw8bgu8P7TvLn8uDd-fQJn81csnH-NglVQQ8ehT5dixaBWe9S4O91aymQrZ6bRsj2xsXvTdIv396KhMBQHT-V09FlPrmA9VNFA6JzmMIeXbN4OzR4yCGMNHIKtLDf4GTcG-6huB_JsjjNLHaZOx0PMshJ6hNVq4IQW3_TIfeW2byu5YgrGPUHPgKrohw"
}
2023-09-14 17:34:28,381:DEBUG:urllib3.connectionpool:"POST /acme/authz-v3/264476644846 HTTP/1.1" 200 819
2023-09-14 17:34:28,382:DEBUG:acme.client:Received response:
HTTP 200
content-length: 819
cache-control: public, max-age=0, no-cache
strict-transport-security: max-age=604800
server: nginx
connection: keep-alive
link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
boulder-requester: 105472978
date: Thu, 14 Sep 2023 22:34:28 GMT
x-frame-options: DENY
content-type: application/json
replay-nonce: jHwWLmW4p-LD-oM821kSeYdZ3UGYs3E0XNxUCYev5l87SgNpZW8
{
"identifier": {
"type": "dns",
"value": "bdnetbreeze.blackdragonnetworks.com"
},
"status": "pending",
"expires": "2023-09-21T22:34:28Z",
"challenges": [
{
"type": "http-01",
"status": "pending",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/264476644846/LQxWYA",
"token": "hz-Gi3duw_OBYXYxvj8w4PMxqEh_U1xr-XMcXSIHmH8"
},
{
"type": "dns-01",
"status": "pending",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/264476644846/M3Q8Xw",
"token": "hz-Gi3duw_OBYXYxvj8w4PMxqEh_U1xr-XMcXSIHmH8"
},
{
"type": "tls-alpn-01",
"status": "pending",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/264476644846/rsJ6_A",
"token": "hz-Gi3duw_OBYXYxvj8w4PMxqEh_U1xr-XMcXSIHmH8"
}
]
}
2023-09-14 17:34:28,382:DEBUG:acme.client:Storing nonce: jHwWLmW4p-LD-oM821kSeYdZ3UGYs3E0XNxUCYev5l87SgNpZW8
2023-09-14 17:34:28,383:INFO:certbot._internal.auth_handler:Performing the following challenges:
2023-09-14 17:34:28,383:INFO:certbot._internal.auth_handler:http-01 challenge for bdnetbreeze.blackdragonnetworks.com
2023-09-14 17:34:28,395:INFO:certbot_nginx._internal.http_01:Using default addresses 80 and [::]:80 ipv6only=on for authentication.
2023-09-14 17:34:28,397:DEBUG:certbot_nginx._internal.http_01:Generated server block:
[[['server'], [['listen', '80'], ['listen', '[::]:80'], ['server_name', u'bdnetbreeze.blackdragonnetworks.com'], ['root', '/var/lib/letsencrypt/http_01_nonexistent'], [['location', '=', u'/.well-known/acme-challenge/hz-Gi3duw_OBYXYxvj8w4PMxqEh_U1xr-XMcXSIHmH8'], [['default_type', 'text/plain'], ['return', '200', u'hz-Gi3duw_OBYXYxvj8w4PMxqEh_U1xr-XMcXSIHmH8.aw7Fck4lK_DPKN2EdwgFdeZn_RNJYeN6NgTlNkCvUF0']]]]]]
2023-09-14 17:34:28,397:DEBUG:certbot.reverter:Creating backup of /usr/share/nginx/modules/mod-http-image-filter.conf
2023-09-14 17:34:28,398:DEBUG:certbot.reverter:Creating backup of /etc/letsencrypt/options-ssl-nginx.conf
2023-09-14 17:34:28,398:DEBUG:certbot.reverter:Creating backup of /usr/share/nginx/modules/mod-stream.conf
2023-09-14 17:34:28,398:DEBUG:certbot.reverter:Creating backup of /usr/share/nginx/modules/mod-http-xslt-filter.conf
2023-09-14 17:34:28,398:DEBUG:certbot.reverter:Creating backup of /etc/nginx/mime.types
2023-09-14 17:34:28,399:DEBUG:certbot.reverter:Creating backup of /usr/share/nginx/modules/mod-mail.conf
2023-09-14 17:34:28,399:DEBUG:certbot.reverter:Creating backup of /etc/nginx/nginx.conf
2023-09-14 17:34:28,399:DEBUG:certbot.reverter:Creating backup of /usr/share/nginx/modules/mod-http-perl.conf
2023-09-14 17:34:28,401:DEBUG:certbot_nginx._internal.parser:Writing nginx conf tree to /etc/nginx/nginx.conf:
# For more information on configuration, see:
# * Official English Documentation: http://nginx.org/en/docs/
# * Official Russian Documentation: http://nginx.org/ru/docs/
user nginx;
worker_processes auto;
error_log /var/log/nginx/error.log;
pid /run/nginx.pid;
# Load dynamic modules. See /usr/share/doc/nginx/README.dynamic.
include /usr/share/nginx/modules/*.conf;
events {
worker_connections 1024;
}
http {
include /etc/letsencrypt/le_http_01_cert_challenge.conf;
server_names_hash_bucket_size 128;
log_format main '$remote_addr - $remote_user [$time_local] "$request" '
'$status $body_bytes_sent "$http_referer" '
'"$http_user_agent" "$http_x_forwarded_for"';
access_log /var/log/nginx/access.log main;
sendfile on;
tcp_nopush on;
tcp_nodelay on;
keepalive_timeout 65;
types_hash_max_size 2048;
include /etc/nginx/mime.types;
default_type application/octet-stream;
# Load modular configuration files from the /etc/nginx/conf.d directory.
# See http://nginx.org/en/docs/ngx_core_module.html#include
# for more information.
include /etc/nginx/conf.d/*.conf;
server {
server_name bdnetbreeze.blackdragonnetworks.com; # managed by Certbot
root /usr/share/nginx/html;
# Load configuration files for the default server block.
include /etc/nginx/default.d/*.conf;
location /.well-known
{
}
location / {
proxy_buffers 64 64k;
proxy_buffer_size 2k;
proxy_pass http://127.0.0.1:8082/;
}
error_page 404 /404.html;
location = /404.html {
}
error_page 500 502 503 504 /50x.html;
location = /50x.html {
}
listen [::]:443 ssl ipv6only=on; # managed by Certbot
listen 443 ssl; # managed by Certbot
ssl_certificate /etc/letsencrypt/live/bdnetbreeze.blackdragonnetworks.com/fullchain.pem; # managed by Certbot
ssl_certificate_key /etc/letsencrypt/live/bdnetbreeze.blackdragonnetworks.com/privkey.pem; # managed by Certbot
include /etc/letsencrypt/options-ssl-nginx.conf; # managed by Certbot
ssl_dhparam /etc/letsencrypt/ssl-dhparams.pem; # managed by Certbot
}}
2023-09-14 17:34:29,425:INFO:certbot._internal.auth_handler:Waiting for verification...
2023-09-14 17:34:29,426:DEBUG:acme.client:JWS payload:
{}
2023-09-14 17:34:29,428:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/chall-v3/264476644846/LQxWYA:
{
"protected": "eyJub25jZSI6ICJqSHdXTG1XNHAtTEQtb004MjFrU2VZZFozVUdZczNFMFhOeFVDWWV2NWw4N1NnTnBaVzgiLCAidXJsIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2NoYWxsLXYzLzI2NDQ3NjY0NDg0Ni9MUXhXWUEiLCAia2lkIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMTA1NDcyOTc4IiwgImFsZyI6ICJSUzI1NiJ9",
"payload": "e30",
"signature": "Y3hQZKce51TPCEwY03kLurpHqpTQlqse9GUOq8g92P5X0cXtLw4mPPTX4v0UU16BZp7OAQjXR3NJuvwO0UACI8Obeq6lEmwpzTQQd7oHYceURGd76FAxl_a61Ec7bLLIzkcGPjB3ZxM7VagoO0ny0YQ7enBInI7XNfDXqnpHrEUm2zprVnEGyF-CDzuHUblatmS-3IOkyIBEdjDN8ywN_iB_hdo5zblX7kRpBVyHPBVayJpKDtC0b07J9i81xx_-t3V-cIZXNcJUGcktZcEU0ORG2V8XqJPKSdmYQh0__gCI4U39Y1oRuMYsU_mH02_zu8zZf8nFlcVi8KNeYqHzKg"
}
2023-09-14 17:34:29,504:DEBUG:urllib3.connectionpool:"POST /acme/chall-v3/264476644846/LQxWYA HTTP/1.1" 200 187
2023-09-14 17:34:29,504:DEBUG:acme.client:Received response:
HTTP 200
content-length: 187
cache-control: public, max-age=0, no-cache
strict-transport-security: max-age=604800
server: nginx
connection: keep-alive
link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index", <https://acme-v02.api.letsencrypt.org/acme/authz-v3/264476644846>;rel="up"
location: https://acme-v02.api.letsencrypt.org/acme/chall-v3/264476644846/LQxWYA
boulder-requester: 105472978
date: Thu, 14 Sep 2023 22:34:29 GMT
x-frame-options: DENY
content-type: application/json
replay-nonce: b7AR8yeiVMmqXX4hO5QAe0Dx1uv3Ack5r7MRLDPAFSZQ2caY5Z8
{
"type": "http-01",
"status": "pending",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/264476644846/LQxWYA",
"token": "hz-Gi3duw_OBYXYxvj8w4PMxqEh_U1xr-XMcXSIHmH8"
}
2023-09-14 17:34:29,505:DEBUG:acme.client:Storing nonce: b7AR8yeiVMmqXX4hO5QAe0Dx1uv3Ack5r7MRLDPAFSZQ2caY5Z8
2023-09-14 17:34:30,506:DEBUG:acme.client:JWS payload:
2023-09-14 17:34:30,508:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/authz-v3/264476644846:
{
"protected": "eyJub25jZSI6ICJiN0FSOHllaVZNbXFYWDRoTzVRQWUwRHgxdXYzQWNrNXI3TVJMRFBBRlNaUTJjYVk1WjgiLCAidXJsIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2F1dGh6LXYzLzI2NDQ3NjY0NDg0NiIsICJraWQiOiAiaHR0cHM6Ly9hY21lLXYwMi5hcGkubGV0c2VuY3J5cHQub3JnL2FjbWUvYWNjdC8xMDU0NzI5NzgiLCAiYWxnIjogIlJTMjU2In0",
"payload": "",
"signature": "AL9E80ih5IlqgwGANLbr2IpiGAKvwNwZ5UxOYCxuUPjDU6VYt3-O2LTlOX_ZRVbPPOcXafPqoUz27FsQ6RYl7oHjayFAOWAfDsr6tlYCbGEFl6CdEcdv0G5qRupZeJ8wX_sRTPZjX1TQqwrp8JsrrNKfIVRcRQyWqPH-O-C_9VQxVBwOvJoSfZSOPcePO1bpxicW3yCpFyxpU6AVaN5pSOwrzx0AYTmH3leYddMnLwCwNzYVxZsFO5vb2eXu-3qiZrQTmQpxf_0AUKGL0OyYraYqGNaPMY-0WwcE4-fYprv3SAh-hDqDKPBuN3ineMi-NUObfBk2no3POlYvQwVghw"
}
2023-09-14 17:34:30,679:DEBUG:urllib3.connectionpool:"POST /acme/authz-v3/264476644846 HTTP/1.1" 200 1111
2023-09-14 17:34:30,680:DEBUG:acme.client:Received response:
HTTP 200
content-length: 1111
cache-control: public, max-age=0, no-cache
strict-transport-security: max-age=604800
server: nginx
connection: keep-alive
link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
boulder-requester: 105472978
date: Thu, 14 Sep 2023 22:34:30 GMT
x-frame-options: DENY
content-type: application/json
replay-nonce: b7AR8yeipretuO9qJrwjVFxF5j2ndMS16f8dcVRk6kyi2cJ5pNk
{
"identifier": {
"type": "dns",
"value": "bdnetbreeze.blackdragonnetworks.com"
},
"status": "invalid",
"expires": "2023-09-21T22:34:28Z",
"challenges": [
{
"type": "http-01",
"status": "invalid",
"error": {
"type": "urn:ietf:params:acme:error:unauthorized",
"detail": "144.202.76.212: Invalid response from http://bdnetbreeze.blackdragonnetworks.com/.well-known/acme-challenge/hz-Gi3duw_OBYXYxvj8w4PMxqEh_U1xr-XMcXSIHmH8: 404",
"status": 403
},
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/264476644846/LQxWYA",
"token": "hz-Gi3duw_OBYXYxvj8w4PMxqEh_U1xr-XMcXSIHmH8",
"validationRecord": [
{
"url": "http://bdnetbreeze.blackdragonnetworks.com/.well-known/acme-challenge/hz-Gi3duw_OBYXYxvj8w4PMxqEh_U1xr-XMcXSIHmH8",
"hostname": "bdnetbreeze.blackdragonnetworks.com",
"port": "80",
"addressesResolved": [
"144.202.76.212"
],
"addressUsed": "144.202.76.212"
}
],
"validated": "2023-09-14T22:34:29Z"
}
]
}
2023-09-14 17:34:30,680:DEBUG:acme.client:Storing nonce: b7AR8yeipretuO9qJrwjVFxF5j2ndMS16f8dcVRk6kyi2cJ5pNk
2023-09-14 17:34:30,681:WARNING:certbot._internal.auth_handler:Challenge failed for domain bdnetbreeze.blackdragonnetworks.com
2023-09-14 17:34:30,681:INFO:certbot._internal.auth_handler:http-01 challenge for bdnetbreeze.blackdragonnetworks.com
2023-09-14 17:34:30,681:DEBUG:certbot._internal.reporter:Reporting to user: The following errors were reported by the server:
Domain: bdnetbreeze.blackdragonnetworks.com
Type: unauthorized
Detail: 144.202.76.212: Invalid response from http://bdnetbreeze.blackdragonnetworks.com/.well-known/acme-challenge/hz-Gi3duw_OBYXYxvj8w4PMxqEh_U1xr-XMcXSIHmH8: 404
To fix these errors, please make sure that your domain name was entered correctly and the DNS A/AAAA record(s) for that domain contain(s) the right IP address.
2023-09-14 17:34:30,681:DEBUG:certbot._internal.error_handler:Encountered exception:
Traceback (most recent call last):
File "/usr/lib/python2.7/site-packages/certbot/_internal/auth_handler.py", line 91, in handle_authorizations
self._poll_authorizations(authzrs, max_retries, best_effort)
File "/usr/lib/python2.7/site-packages/certbot/_internal/auth_handler.py", line 180, in _poll_authorizations
raise errors.AuthorizationError('Some challenges have failed.')
AuthorizationError: Some challenges have failed.
2023-09-14 17:34:30,682:DEBUG:certbot._internal.error_handler:Calling registered functions
2023-09-14 17:34:30,682:INFO:certbot._internal.auth_handler:Cleaning up challenges
2023-09-14 17:34:31,813:DEBUG:certbot._internal.log:Exiting abnormally:
Traceback (most recent call last):
File "/usr/bin/certbot", line 9, in <module>
load_entry_point('certbot==1.11.0', 'console_scripts', 'certbot')()
File "/usr/lib/python2.7/site-packages/certbot/main.py", line 15, in main
return internal_main.main(cli_args)
File "/usr/lib/python2.7/site-packages/certbot/_internal/main.py", line 1421, in main
return config.func(config, plugins)
File "/usr/lib/python2.7/site-packages/certbot/_internal/main.py", line 1156, in run
certname, lineage)
File "/usr/lib/python2.7/site-packages/certbot/_internal/main.py", line 124, in _get_and_save_cert
renewal.renew_cert(config, domains, le_client, lineage)
File "/usr/lib/python2.7/site-packages/certbot/_internal/renewal.py", line 331, in renew_cert
new_cert, new_chain, new_key, _ = le_client.obtain_certificate(domains, new_key)
File "/usr/lib/python2.7/site-packages/certbot/_internal/client.py", line 374, in obtain_certificate
orderr = self._get_order_and_authorizations(csr.data, self.config.allow_subset_of_names)
File "/usr/lib/python2.7/site-packages/certbot/_internal/client.py", line 421, in _get_order_and_authorizations
authzr = self.auth_handler.handle_authorizations(orderr, best_effort)
File "/usr/lib/python2.7/site-packages/certbot/_internal/auth_handler.py", line 91, in handle_authorizations
self._poll_authorizations(authzrs, max_retries, best_effort)
File "/usr/lib/python2.7/site-packages/certbot/_internal/auth_handler.py", line 180, in _poll_authorizations
raise errors.AuthorizationError('Some challenges have failed.')
AuthorizationError: Some challenges have failed.
2023-09-14 17:34:31,815:ERROR:certbot._internal.log:Some challenges have failed.
My web server is (include version):apache
The operating system my web server runs on is (include version):Centos 7
My hosting provider, if applicable, is: Vultr
I can login to a root shell on my machine (yes or no, or I don't know):yes
I'm using a control panel to manage my site (no, or provide the name and version of the control panel):
The version of my client is (e.g. output of certbot --version or certbot-auto --version if you're using Certbot):1.11.0