Is there a way to debug and test a secure React (built from create-react-app) app using the certbot certificates on my system?
I've been using LetsEncrypt with certbot-managed certificates for more than a year with no issues. I understand that they require public access to port 443. This is fine once they're working -- I use the yarn build command from the base directory of the project and deploy the result to a public-facing html directory. All works fine.
Development and testing is a different story. Surely I'm not the first developer to use create-react-app and LetsEncrypt certificates together. I use Visual Studio Code (VSC) and use its facilities for launching a Chrome browser on my local system with special connections back to the dev machine that is running VSC.
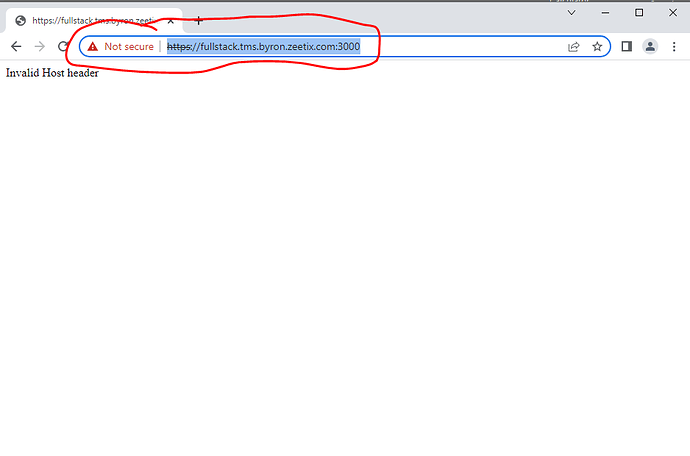
Amazingly, the resulting browser runs and correctly communicates with VDE, so that I can set and catch breakpoints and step through React code running in the browser. This is all great. The rub is that I have to click through several challenges to get to the page, and when I get there the browser reports that the page is not secure (annotated screenshot below).
I'm developing and testing site behavior that depends on having a secure connection, and so I don't want to just turn it off. FWIW, I have a related issue (though I think I have work-arounds) for the nodejs middleware services used by the front-end to connect back to the server.
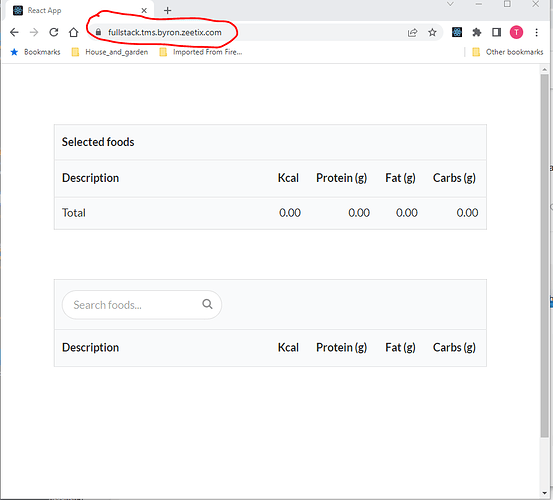
I invite community guidance about how to configure my development environment so that the "start" command issued to react-scripts in the yarn start command line results in a "clean" browser page (see second screenshot below). For any web developers reading this, how do you develop and test secure apps?
Screenshots:
Development browser (dirty)
Clean browser
Requested information
My domain is: byron.zeetix.com
My web server is (include version): Apache/2.4.37 (rocky)
The operating system my web server runs on is (include version): Rocky Linux v8.6
I can login to a root shell on my machine (yes or no, or I don't know): Yes
I'm using a control panel to manage my site (no, or provide the name and version of the control panel): no
The version of my client is (e.g. output of certbot --version or certbot-auto --version if you're using Certbot): certbot 1.30.0