Thank you for the pointer and your time to read this. I do support for other things and realize the imposition on your time.
Most of the other answers simply said I should use a DNS with on API when I stated in the original post that I am quite comfortable with editing files and don't want to switch DNS servers. BTW - I use 'vi' for changing my DNS (web and mail) and have been doing things by hand since 1992. Using Unix since 1982. However I am beginning to think of doing it or just giving up on LetsEncrypt
I followed the directions several times and each one failed at the validation. The last time I waited for the TTL to pass before I tried to validate my domain. I have included the times, 'dig' and 'whois' results to show that it should have passed. I looked through the logfile (also attached) and it just says that it failed with a traceback. The site intodns.com has no issue with my DNS.
dns-validation.txt (5.4 KB)
root@nextcloud:/usr/local/www/nextcloud/apps # certbot certonly -v --manual --preferred-challenges dns -d '*.faultline.com'
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Plugins selected: Authenticator manual, Installer None
Requesting a certificate for *.faultline.com
Performing the following challenges:
dns-01 challenge for faultline.com
Please deploy a DNS TXT record under the name:
_acme-challenge.faultline.com.
with the following value:
Y8-QfJXqlE2_VG_xlhoco55e60JneJRqZ9ujGEfXbIU
Before continuing, verify the TXT record has been deployed. Depending on the DNS
provider, this may take some time, from a few seconds to multiple minutes. You can
check if it has finished deploying with aid of online tools, such as the Google
Admin Toolbox: Dig (DNS lookup).
Look for one or more bolded line(s) below the line ';ANSWER'. It should show the
value(s) you've just added.
Press Enter to Continue
Waiting for verification...
Challenge failed for domain faultline.com
dns-01 challenge for faultline.com
Certbot failed to authenticate some domains (authenticator: manual). The Certificate Authority reported these problems:
Domain: faultline.com
Type: unauthorized
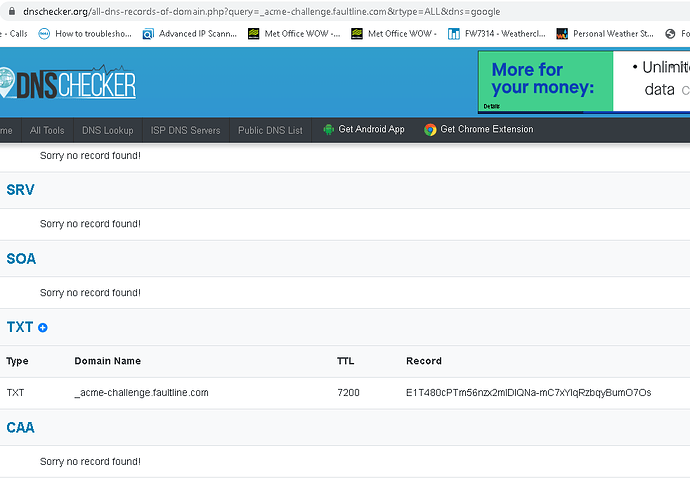
Detail: During secondary validation: Incorrect TXT record "E1T480cPTm56nzx2mlDIQNa-mC7xYlqRzbqyBumO7Os" found at _acme-challenge.faultline.com
Hint: The Certificate Authority failed to verify the manually created DNS TXT records. Ensure that you created these in the correct location, or try waiting longer for DNS propagation on the next attempt.
Cleaning up challenges
Some challenges have failed.
Ask for help or search for solutions at https://community.letsencrypt.org. See the logfile /var/log/letsencrypt/letsencrypt.log or re-run Certbot with -v for more details.
letsencrypt.log.txt (19.8 KB)
Thanks,
Carl