Replay
May 24, 2019, 11:49am
1
Hi, wizards.
I run simple wordpress server on CentOS7 + Nginx 1.14 + Certbot 0.31. I plan to serve several websites with unique domain names on single IP (SNI is enabled). My first LE cert obtained for elementarno.pro worked correctly, until I’ve requested one more cert for webdiz.men . Two certs counteract with each other, causing warnings at ssllabs.com and making second website redirect to first.
I’ve tried to delete certs and issue them again one by one and in reverse order, but this didn’t help and soon I was informed of having 5 duplicates of certs for single domain. Compared to prior redirects problem - there’s possibly invalid cert. I thought every time I use certbot delete , the cert is removed at LetsEncrypt as well. Now I’m in confusion - how to manage these duplicate entries? How should I know which of them is currently in use?
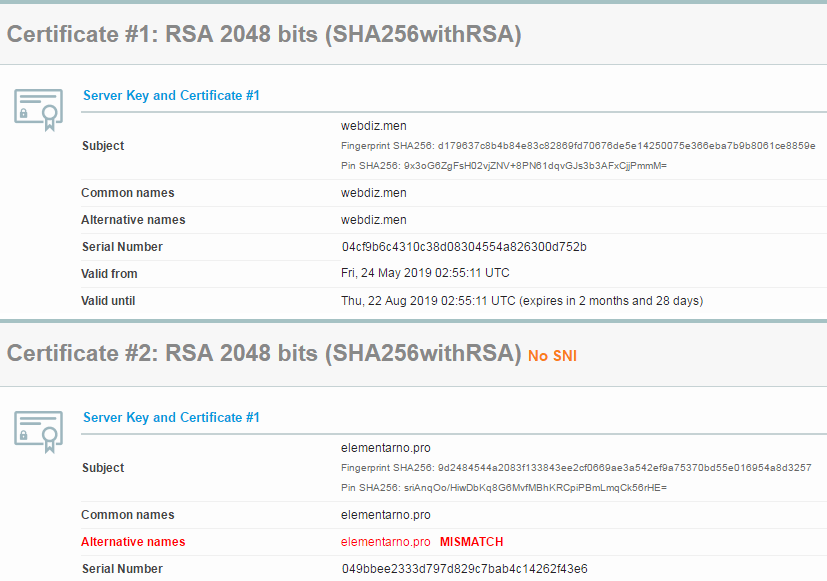
This is ssllabs.com output for webdiz.men:
Hi @Replay
Replay:
webdiz.men:
there are some checks of your domain - https://check-your-website.server-daten.de/?q=webdiz.men
You have created a certificate with one domain name:
CN=webdiz.men
24.05.2019
22.08.2019
expires in 90 days webdiz.men - 1 entry
So you can't use that certificate with your www - version:
There is a NameMismatch - error.
The No-SNI - part is completely irrelevant. That's always wrong if you have more then one certificate on the same ip address, that's the idea of SNI.
First check your vHost configuration with
nginx -T
You should have one vHost with both domain names (non-www and www).
Then create one certificate with both domain names. But you have already created 5 certificates:
|925579447 |CN=Let's Encrypt Authority X3, O=Let's Encrypt, C=US|2019-05-22 10:40:58|2019-08-20 10:40:58|webdiz.men, www.webdiz.men
What says
certbot certificates
certbot certificates
Found the following certs:
I use one vHost for both domain names. Here is short summary of each vHost config:
server {
Replay:
certbot certificates
Why aren't there the certificates with both domain names?
Where are these?
That's good. But that requires a certificate with both domain names.
Here it is (certbot certonly --renew-by-default -d www.webdiz.men ). Nothing has changed.
Found the following certs:
Replay:
Here it is
No, there is nothing. There should be one certificate with
Domains: webdiz.men, www.webdiz.men
And you have created such certificates - https://check-your-website.server-daten.de/?q=webdiz.men#ct-logs
CertSpotter-Id
Issuer
not before
not after
Domain names
LE-Duplicate
next LE
928537099 CN=Let's Encrypt Authority X3, O=Let's Encrypt, C=US
2019-05-24 02:59:21
2019-08-22 02:59:21
www.webdiz.men
1 entries
duplicate nr. 2
928533591 CN=Let's Encrypt Authority X3, O=Let's Encrypt, C=US
2019-05-24 02:55:11
2019-08-22 02:55:11
webdiz.men
1 entries
duplicate nr. 2
927654103 CN=Let's Encrypt Authority X3, O=Let's Encrypt, C=US
2019-05-23 14:03:01
2019-08-21 14:03:01
p9m1a.webdiz.men
1 entries
duplicate nr. 1
926089317 CN=Let's Encrypt Authority X3, O=Let's Encrypt, C=US
2019-05-22 17:53:47
2019-08-20 17:53:47
www.webdiz.men
1 entries
duplicate nr. 1
925870418 CN=Let's Encrypt Authority X3, O=Let's Encrypt, C=US
2019-05-22 14:35:38
2019-08-20 14:35:38
webdiz.men
1 entries
duplicate nr. 1
925579447 CN=Let's Encrypt Authority X3, O=Let's Encrypt, C=US
2019-05-22 10:40:58
2019-08-20 10:40:58
webdiz.men, www.webdiz.men
2 entries
duplicate nr. 5
next Letsencrypt certificate: 2019-05-25 10:37:13
925433978 CN=Let's Encrypt Authority X3, O=Let's Encrypt, C=US
2019-05-22 09:00:13
2019-08-20 09:00:13
webdiz.men, www.webdiz.men
2 entries
duplicate nr. 4
925213975 CN=Let's Encrypt Authority X3, O=Let's Encrypt, C=US
2019-05-22 06:31:28
2019-08-20 06:31:28
elementarno.pro, webdiz.men, www.elementarno.pro, www.webdiz.men
4 entries
duplicate nr. 2
925189766 CN=Let's Encrypt Authority X3, O=Let's Encrypt, C=US
2019-05-22 06:15:39
2019-08-20 06:15:39
elementarno.pro, webdiz.men, www.elementarno.pro, www.webdiz.men
4 entries
duplicate nr. 1
924325988 CN=Let's Encrypt Authority X3, O=Let's Encrypt, C=US
2019-05-21 19:32:10
2019-08-19 19:32:10
webdiz.men, www.webdiz.men
2 entries
duplicate nr. 3
924157217 CN=Let's Encrypt Authority X3, O=Let's Encrypt, C=US
2019-05-21 17:57:05
2019-08-19 17:57:05
webdiz.men, www.webdiz.men
2 entries
duplicate nr. 2
918468578 CN=Let's Encrypt Authority X3, O=Let's Encrypt, C=US
2019-05-18 10:37:13
2019-08-16 10:37:13
webdiz.men, www.webdiz.men
2 entries
duplicate nr. 1
5 identical certificates with both domain names - first 2019-05-18.
Thanks for pointing it out. But how can I enable this very cert and disable duplicates?
Took few days to reissue cert for webdiz.men. The problem persists, and reports are very demonstrative:
sudo certbot certificates
There is a new check of your domain - https://check-your-website.server-daten.de/?q=webdiz.men
The non-www has the correct certificate with both domain names:
CN=www.webdiz.men
30.05.2019
28.08.2019
expires in 90 days
webdiz.men, www.webdiz.men - 2 entries
So this certificate is correct.
But your www version doesn't use it.
Replay:
…server {
remove the wrong www vHost and merge the content with your correct non-www https vHost. So both versions (non-www and www) are using the same vHost with the certificate.
1 Like
Replay
June 5, 2019, 12:20pm
10
I've removed the www vHost and merged the content. The counteraction error is still listed in ssllabs.com reports. So I performed a test. I've deleted entire elementarno.pro certificate and restarted Nginx:
sudo certbot delete
Results are speaking for themselves: now browsers don't open https://webdiz.men Assessment failed: No secure protocols supported
How could it happen certificates become linked? What I supposed to do to unlink them?
If you delete a certificate, it's not deleted in your webserver config file. So the webserver want's to load the file - but you have deleted it. Restore it from your backup.
Or create a self signed certificate and change your config file, so the self signed is used.
Replay
June 5, 2019, 1:32pm
12
O course I’ve commented (#) certificate in elementarno.pro.conf nginx config file. That’s why I ask for help.
You can't use a https port without a certificate. The result:
So you have to remove the port 443 vHost or you have to replace the certificate with another certificate.
1 Like
Replay
June 7, 2019, 3:59am
14
Thanks a lot, Juergen. It worked.
2 Likes
system
July 7, 2019, 3:59am
15
This topic was automatically closed 30 days after the last reply. New replies are no longer allowed.