Hi folks - I previously had Let's Encrypt working but made the mistake of updating about thirty packages at once, so now things are broken and I'm not sure what to roll back. I only figured this out because of a very helpful "your cert is expiring" reminder email from LE.
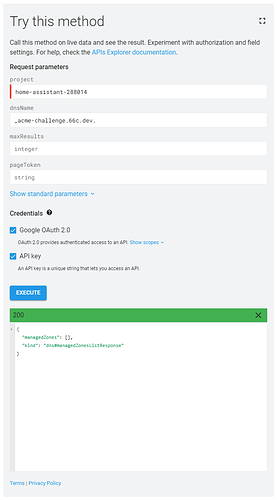
My base domain (66c.dev) is hosted on Google Domains. The _acme-challenge subdomain is CNAMED to _acme-challenge.acme.66c.dev; the entire acme.66c.dev subdomain is managed by Google Cloud DNS (and this is where certbot used to add / remove challenge records).
I distinctly remember that I needed to patch a line to make this work last time, which I've done per this thread: DNS plugins don't work if _acme-challenge is a separate zone · Issue #7701 · certbot/certbot · GitHub
But I'm still getting this mystery error:
Unable to determine managed zone for 66c.dev using zone names: ['_acme_challenge.66c.dev', '66c.dev', 'dev'].
This surprises me because _acme_challenge.66c.dev does exist. What am I missing?
The Google specific code is here.
My domain is:
*.66c.dev
I ran this command:
I'm using the Let's Encrypt Home Assistant plugin.
It produced this output:
[s6-init] making user provided files available at /var/run/s6/etc...exited 0.
[s6-init] ensuring user provided files have correct perms...exited 0.
[fix-attrs.d] applying ownership & permissions fixes...
[fix-attrs.d] done.
[cont-init.d] executing container initialization scripts...
[cont-init.d] file-structure.sh: executing...
[cont-init.d] file-structure.sh: exited 0.
[cont-init.d] done.
[services.d] starting services
[services.d] done.
[22:31:49] INFO: Selected DNS Provider: dns-google
[22:31:49] INFO: Use propagation seconds: 60
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Requesting a certificate for *.66c.dev
Error finding zone. Skipping cleanup.
Unable to determine managed zone for 66c.dev using zone names: ['_acme_challenge.66c.dev', '66c.dev', 'dev'].
Ask for help or search for solutions at https://community.letsencrypt.org. See the logfile /var/log/letsencrypt/letsencrypt.log or re-run Certbot with -v for more details.
[cont-finish.d] executing container finish scripts...
[cont-finish.d] done.
[s6-finish] waiting for services.
[s6-finish] sending all processes the TERM signal.
[s6-finish] sending all processes the KILL signal and exiting.
My web server is (include version):
Using DNS challenge.
The operating system my web server runs on is (include version):
Ubuntu latest.
My hosting provider, if applicable, is:
N/A
I can login to a root shell on my machine (yes or no, or I don't know):
Yes
I'm using a control panel to manage my site (no, or provide the name and version of the control panel):
Yes, Home Assistant
The version of my client is (e.g. output of certbot --version or certbot-auto --version if you're using Certbot):
Let's Encrypt
Current version: 4.12.2