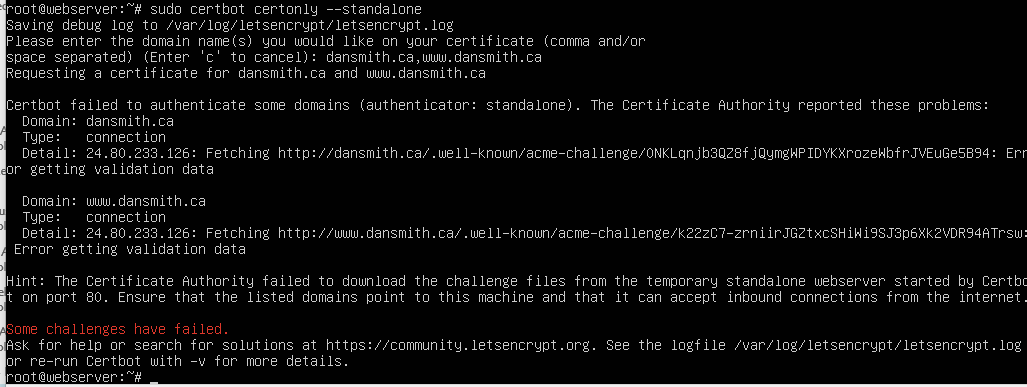
My domain is: dansmith.ca
I ran this command: certbot certonly, certbot certonly --apache, certbot certonly --standalone, certbot certonly --webroot, certbot certonly (all failed with acme challenge response)
It produced this output: "Invalid response from http://www.dansmith.ca/.well-known/acme-challenge/<random_string>: 404
My web server is (include version): Ubuntu Linux 20.04.2 LTS (command line)
The operating system my web server runs on is (include version): Ubuntu Linux 20.04.2 LTS (Hyper-V virtual machine)
My hosting provider, if applicable, is: self-hosted
I can login to a root shell on my machine (yes or no, or I don't know): Yes
I'm using a control panel to manage my site (no, or provide the name and version of the control panel): No
The version of my client is (e.g. output of certbot --version or certbot-auto --version if you're using Certbot): 2.5.0
Ok, so I currently have a Hyper-V Windows 2019 virtual server running my sites which are secured already with a valid cert, and have recently set up a Ubuntu Linux server so I can move everything over to it and retire the Windows web server. However, when I go to run certbot using any of the commands above, I get the "Some challenges have failed" message. Is this because when Certbot goes out LetsEncrypt, does it see that I already have a certificate and refuse to issue a new one?
Regarding the .well-known/acme-challenges, the folder is writable (777), so I know that writing to the folder is not an issue. Also I think that certbot is supposed to TELL me what the acme-challenge is BEFORE it tries to write to the folder and create the cert, isn't it? It does not tell me what the challenge is so when I go to the freedns to make a TXT entry with my challenge, I can put it there and then Certbot will go look at it and say it's OK and process the challenge normally.
UFW tells me that Apache Full, OpenSSH, 80, 443, and 22 are all open and allowed.
But still, it fails, and I have no idea why. How do I start from scratch without rebuilding Linux and doing all this over again?
I have no problems running my site LOCALLY on HTTP but I can't run it on the WEB with HTTPS.
Thanks to anyone who can help.