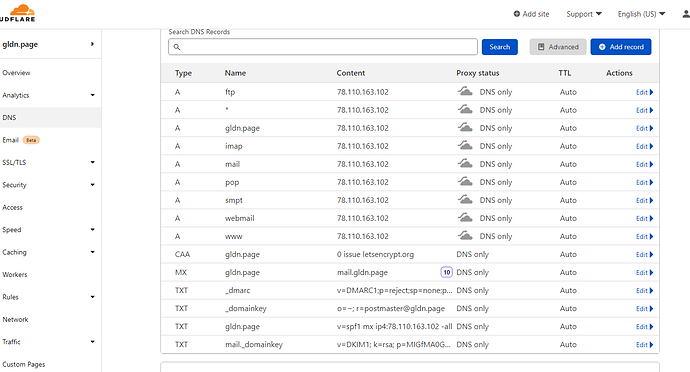
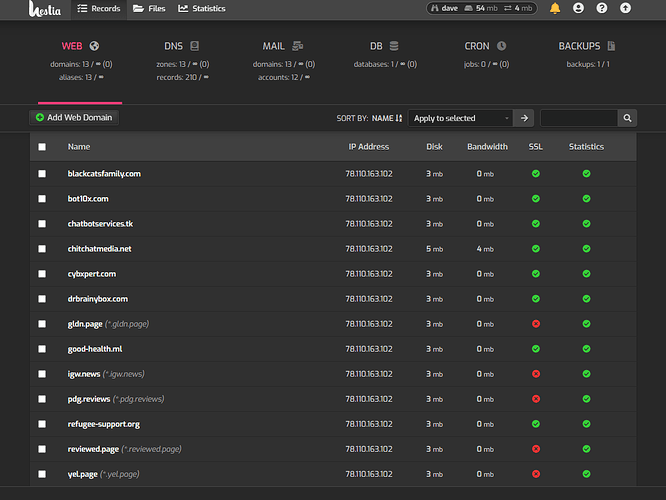
My domain is: gldn.page
I ran this command:
certbot certonly --dns-cloudflare --dns-cloudflare-credentials /root/.secrets/gldn.ini -d gldn.page,*.gldn.page
It produced this output:
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Plugins selected: Authenticator dns-cloudflare, Installer None
Obtaining a new certificate
Performing the following challenges:
dns-01 challenge for gldn.page
dns-01 challenge for gldn.page
Cleaning up challenges
Error determining zone_id: 6003 Invalid request headers. Please confirm that you have supplied valid Cloudflare API credentials. (Did you copy your entire API key?)
My web server is (include version):
Apache/2.4.53 (Ubuntu)
Also running Nginx for reverse proxy
The operating system my web server runs on is (include version):
ubuntu 20.04
My hosting provider, if applicable, is:
dedicated by UKservers.com
I can login to a root shell on my machine (yes or no, or I don't know):
yes
I'm using a control panel to manage my site (no, or provide the name and version of the control panel):
HestiaCP but it doesn't do sub-domain LE certs so I am using command line
The version of my client is (e.g. output of certbot --version or certbot-auto --version if you're using Certbot):
certbot 0.40.0
I have checked that the Cloudflare token is correct with the curl:
curl -X GET "https://api.cloudflare.com/client/v4/user/tokens/verify" -H "Authorization: Bearer my-token-here" -H "Content-Type:application/json"
and I get back :
{"result":{"id":"3dfa37378f76e29afd63ca8474b696fe","status":"active"},"success":true,"errors":,"messages":[{"code":10000,"message":"This API Token is valid and active","type":null}]}root@expressresponse:/var/log/letsencrypt#
So I was disappointed that it didn't create the cert.