My domain is:
klubben319.se
I ran this command:
Tried to create SSL cert through web-ui.
It produced this output:
Internal Error
Error: Command failed: certbot certonly --config "/etc/letsencrypt.ini" --work-dir "/tmp/letsencrypt-lib" --logs-dir "/tmp/letsencrypt-log" --cert-name "npm-6" --agree-tos --authenticator webroot --email "andreas.back@gmail.com" --preferred-challenges "dns,http" --domains "klubben319.se"
Saving debug log to /tmp/letsencrypt-log/letsencrypt.log
Some challenges have failed.
Ask for help or search for solutions at https://community.letsencrypt.org. See the logfile /tmp/letsencrypt-log/letsencrypt.log or re-run Certbot with -v for more details.
at ChildProcess.exithandler (node:child_process:402:12)
at ChildProcess.emit (node:events:513:28)
at maybeClose (node:internal/child_process:1100:16)
at Process.ChildProcess._handle.onexit (node:internal/child_process:304:5)
From log file:
2023-09-29 17:40:31,910:DEBUG:certbot._internal.main:certbot version: 2.1.0
2023-09-29 17:40:31,910:DEBUG:certbot._internal.main:Location of certbot entry point: /usr/bin/certbot
2023-09-29 17:40:31,910:DEBUG:certbot._internal.main:Arguments: ['--config', '/etc/letsencrypt.ini', '--work-dir', '/tmp/letsencrypt-lib', '--logs-dir', '/tmp/letsencrypt-log', '--cert-name', 'npm-3', '--agree-tos', '--authenticator', 'webroot', '--email', 'andreas.back@gmail.com', '--preferred-challenges', 'dns,http', '--domains', 'klubben319.se']
2023-09-29 17:40:31,910:DEBUG:certbot._internal.main:Discovered plugins: PluginsRegistry(PluginEntryPoint#dns-cloudflare,PluginEntryPoint#dns-duckdns,PluginEntryPoint#dns-porkbun,PluginEntryPoint#manual,PluginEntryPoint#null,PluginEntryPoint#standalone,PluginEntryPoint#webroot)
2023-09-29 17:40:31,915:DEBUG:certbot._internal.log:Root logging level set at 30
2023-09-29 17:40:31,916:DEBUG:certbot._internal.plugins.selection:Requested authenticator webroot and installer None
2023-09-29 17:40:31,916:DEBUG:certbot._internal.plugins.selection:Single candidate plugin: * webroot
Description: Place files in webroot directory
Interfaces: Authenticator, Plugin
Entry point: webroot = certbot._internal.plugins.webroot:Authenticator
Initialized: <certbot._internal.plugins.webroot.Authenticator object at 0x7fd5eb4a71d0>
Prep: True
2023-09-29 17:40:31,916:DEBUG:certbot._internal.plugins.selection:Selected authenticator <certbot._internal.plugins.webroot.Authenticator object at 0x7fd5eb4a71d0> and installer None
2023-09-29 17:40:31,916:INFO:certbot._internal.plugins.selection:Plugins selected: Authenticator webroot, Installer None
2023-09-29 17:40:31,949:DEBUG:certbot._internal.main:Picked account: <Account(RegistrationResource(body=Registration(key=None, contact=(), agreement=None, status=None, terms_of_service_agreed=None, only_return_existing=None, external_account_binding=None), uri='https://acme-v02.api.letsencrypt.org/acme/acct/1335273496', new_authzr_uri=None, terms_of_service=None), 94f3fdfcfa93db5105b5a17591d79f2c, Meta(creation_dt=datetime.datetime(2023, 9, 29, 15, 32, 48, tzinfo=<UTC>), creation_host='nginxproxymanager.se', register_to_eff=None))>
2023-09-29 17:40:31,950:DEBUG:acme.client:Sending GET request to https://acme-v02.api.letsencrypt.org/directory.
2023-09-29 17:40:32,505:DEBUG:acme.client:Received response:
HTTP 200
Server: nginx
Date: Fri, 29 Sep 2023 15:40:32 GMT
Content-Type: application/json
Content-Length: 752
Connection: keep-alive
Cache-Control: public, max-age=0, no-cache
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
{
"keyChange": "https://acme-v02.api.letsencrypt.org/acme/key-change",
"meta": {
"caaIdentities": [
"letsencrypt.org"
],
"termsOfService": "https://letsencrypt.org/documents/LE-SA-v1.3-September-21-2022.pdf",
"website": "https://letsencrypt.org"
},
"newAccount": "https://acme-v02.api.letsencrypt.org/acme/new-acct",
"newNonce": "https://acme-v02.api.letsencrypt.org/acme/new-nonce",
"newOrder": "https://acme-v02.api.letsencrypt.org/acme/new-order",
"q3XPMOqHpWo": "https://community.letsencrypt.org/t/adding-random-entries-to-the-directory/33417",
"renewalInfo": "https://acme-v02.api.letsencrypt.org/draft-ietf-acme-ari-01/renewalInfo/",
"revokeCert": "https://acme-v02.api.letsencrypt.org/acme/revoke-cert"
}
2023-09-29 17:40:32,505:DEBUG:certbot._internal.display.obj:Notifying user: Requesting a certificate for klubben319.se
2023-09-29 17:40:32,508:DEBUG:certbot.crypto_util:Generating ECDSA key (2048 bits): /etc/letsencrypt/keys/0002_key-certbot.pem
2023-09-29 17:40:32,510:DEBUG:certbot.crypto_util:Creating CSR: /etc/letsencrypt/csr/0002_csr-certbot.pem
2023-09-29 17:40:32,511:DEBUG:acme.client:Requesting fresh nonce
2023-09-29 17:40:32,511:DEBUG:acme.client:Sending HEAD request to https://acme-v02.api.letsencrypt.org/acme/new-nonce.
2023-09-29 17:40:32,672:DEBUG:acme.client:Received response:
HTTP 200
Server: nginx
Date: Fri, 29 Sep 2023 15:40:32 GMT
Connection: keep-alive
Cache-Control: public, max-age=0, no-cache
Link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
Replay-Nonce: kQ7ZnGjxhB2vn8VMFPGWZbj3zCodAJDCPa2Qrh-Kjv1maR7diRc
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
2023-09-29 17:40:32,673:DEBUG:acme.client:Storing nonce: kQ7ZnGjxhB2vn8VMFPGWZbj3zCodAJDCPa2Qrh-Kjv1maR7diRc
2023-09-29 17:40:32,673:DEBUG:acme.client:JWS payload:
b'{\n "identifiers": [\n {\n "type": "dns",\n "value": "klubben319.se"\n }\n ]\n}'
2023-09-29 17:40:32,674:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/new-order:
{
"protected": "eyJhbGciOiAiUlMyNTYiLCAia2lkIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMTMzNTI3MzQ5NiIsICJub25jZSI6ICJrUTdabkdqeGhCMnZuOFZNRlBHV1piajN6Q29kQUpEQ1BhMlFyaC1LanYxbWFSN2RpUmMiLCAidXJsIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL25ldy1vcmRlciJ9",
"signature": "Ag8PqapNkPuaEyzvCFpi3gu97WKb1Po43zcei83dov-l1hsws5xG4LDN5NZe5X0NO_q4f6uJG-FInyx4SkgBZvyakRBHCQvvQNrJmqC6HyEnYRipquxrLwgsIIFvnAzdgFXnyP91_VRaF05V5ez7wzriLLiD3M0Q0qA3rwMMlpCNELoYX0q7tO2YgfyCw03IKHG9LLM2cJAj5BUoI9sHoE-Pgg7N3LgBFcRPqBwWLIuhzkG17BusDudndDM7Z6EegAoxu99WLe1SoM9EroLju1GaTO4q_y74uDB_afMQ2gxoErKWo4PBZUuemctiK6EdNaUZg9n0pe53Oy9UBOmcoQ",
"payload": "ewogICJpZGVudGlmaWVycyI6IFsKICAgIHsKICAgICAgInR5cGUiOiAiZG5zIiwKICAgICAgInZhbHVlIjogImtsdWJiZW4zMTkuc2UiCiAgICB9CiAgXQp9"
}
2023-09-29 17:40:32,883:DEBUG:acme.client:Received response:
HTTP 201
Server: nginx
Date: Fri, 29 Sep 2023 15:40:32 GMT
Content-Type: application/json
Content-Length: 339
Connection: keep-alive
Boulder-Requester: 1335273496
Cache-Control: public, max-age=0, no-cache
Link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
Location: https://acme-v02.api.letsencrypt.org/acme/order/1335273496/211691382276
Replay-Nonce: kQ7ZnGjxXi8gSgMfORXvPSn9E9Zerma3qpJ6pzIv15dvLQG8qDQ
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
{
"status": "pending",
"expires": "2023-10-06T15:40:32Z",
"identifiers": [
{
"type": "dns",
"value": "klubben319.se"
}
],
"authorizations": [
"https://acme-v02.api.letsencrypt.org/acme/authz-v3/269111998346"
],
"finalize": "https://acme-v02.api.letsencrypt.org/acme/finalize/1335273496/211691382276"
}
2023-09-29 17:40:32,883:DEBUG:acme.client:Storing nonce: kQ7ZnGjxXi8gSgMfORXvPSn9E9Zerma3qpJ6pzIv15dvLQG8qDQ
2023-09-29 17:40:32,883:DEBUG:acme.client:JWS payload:
b''
2023-09-29 17:40:32,885:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/authz-v3/269111998346:
{
"protected": "eyJhbGciOiAiUlMyNTYiLCAia2lkIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMTMzNTI3MzQ5NiIsICJub25jZSI6ICJrUTdabkdqeFhpOGdTZ01mT1JYdlBTbjlFOVplcm1hM3FwSjZwekl2MTVkdkxRRzhxRFEiLCAidXJsIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2F1dGh6LXYzLzI2OTExMTk5ODM0NiJ9",
"signature": "DC-2FT8MgYcdmBKD0y1sPOC-UrSo51eGy0_ye5tU8RiuS5360uArktjRLer4sXUoevVy54PVEVlRcRjoD2vY3LFsJ9t17L-rNWMUnWLyUKwnzOqdMhuPo6Zg2LH47tXk4SmyPwa2GCORrjvDs2bD4U2M1zASi1THTZc1wj0Ljea_cjpfu9O4DJPrZabFqydjhUIrBhNm7yD13RsvGLOrqhI_Pqxy5m8U7xlOcRyb3fGhMqqr4Eb-KIjrDXS-kyWNUUBoFTHrGlnl1qPfafIfOY1TEiFPQKfL33XzzV2C2GTayPjjvvkTN7U3F0KTbw88BAJVgjxPlKmBX5U-mCKxZw",
"payload": ""
}
2023-09-29 17:40:33,049:DEBUG:acme.client:Received response:
HTTP 200
Server: nginx
Date: Fri, 29 Sep 2023 15:40:32 GMT
Content-Type: application/json
Content-Length: 797
Connection: keep-alive
Boulder-Requester: 1335273496
Cache-Control: public, max-age=0, no-cache
Link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
Replay-Nonce: 3hclikJOPAs90NRrB1Y-F2o6pqIVKABXUMpabLoPXOM-fzcL8wk
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
{
"identifier": {
"type": "dns",
"value": "klubben319.se"
},
"status": "pending",
"expires": "2023-10-06T15:40:32Z",
"challenges": [
{
"type": "http-01",
"status": "pending",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/269111998346/0qH8Ig",
"token": "fEY1l3F53peC8bZOuY6TR575AB2aN8KlQ7xME_pW_OQ"
},
{
"type": "dns-01",
"status": "pending",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/269111998346/cY2hZg",
"token": "fEY1l3F53peC8bZOuY6TR575AB2aN8KlQ7xME_pW_OQ"
},
{
"type": "tls-alpn-01",
"status": "pending",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/269111998346/8NDvug",
"token": "fEY1l3F53peC8bZOuY6TR575AB2aN8KlQ7xME_pW_OQ"
}
]
}
2023-09-29 17:40:33,049:DEBUG:acme.client:Storing nonce: 3hclikJOPAs90NRrB1Y-F2o6pqIVKABXUMpabLoPXOM-fzcL8wk
2023-09-29 17:40:33,049:INFO:certbot._internal.auth_handler:Performing the following challenges:
2023-09-29 17:40:33,049:INFO:certbot._internal.auth_handler:http-01 challenge for klubben319.se
2023-09-29 17:40:33,049:INFO:certbot._internal.plugins.webroot:Using the webroot path /data/letsencrypt-acme-challenge for all unmatched domains.
2023-09-29 17:40:33,050:DEBUG:certbot._internal.plugins.webroot:Creating root challenges validation dir at /data/letsencrypt-acme-challenge/.well-known/acme-challenge
2023-09-29 17:40:33,050:DEBUG:certbot._internal.plugins.webroot:Attempting to save validation to /data/letsencrypt-acme-challenge/.well-known/acme-challenge/fEY1l3F53peC8bZOuY6TR575AB2aN8KlQ7xME_pW_OQ
2023-09-29 17:40:33,050:DEBUG:acme.client:JWS payload:
b'{}'
2023-09-29 17:40:33,051:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/chall-v3/269111998346/0qH8Ig:
{
"protected": "eyJhbGciOiAiUlMyNTYiLCAia2lkIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMTMzNTI3MzQ5NiIsICJub25jZSI6ICIzaGNsaWtKT1BBczkwTlJyQjFZLUYybzZwcUlWS0FCWFVNcGFiTG9QWE9NLWZ6Y0w4d2siLCAidXJsIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2NoYWxsLXYzLzI2OTExMTk5ODM0Ni8wcUg4SWcifQ",
"signature": "ScJwl7s1LWNJ_8wwMGxN1IuKuwNfbEtGmNI90iqdF5wt4lOTMWH1f6tSY8fQPZq9GXvyw0kIn5kthAjVDgC7yCqRNf6dJB4nloNyCNCH0X7pSxv92Tt-zWqvsMpwaORbeb8QGtKL9Y2-VM8qlcbrXVYEAotZQwSRgWdXQtWw3gzJxc1FqSS9VLeNVClmO4uL8peTqNlPBaHSF1NRQc9fYcW6Dpm3uYQtyNiBOxOooQ170kJWYMjnrBli9gGrb4Rr45aIE-56QxqqeqkznJsD9ycYKzUBHNDgyl4kouIZKpYQWHA0Ssp6gCUEzR7dSypY26MKdT6SHBmHZLVKbTFPMg",
"payload": "e30"
}
2023-09-29 17:40:33,218:DEBUG:acme.client:Received response:
HTTP 200
Server: nginx
Date: Fri, 29 Sep 2023 15:40:33 GMT
Content-Type: application/json
Content-Length: 187
Connection: keep-alive
Boulder-Requester: 1335273496
Cache-Control: public, max-age=0, no-cache
Link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index", <https://acme-v02.api.letsencrypt.org/acme/authz-v3/269111998346>;rel="up"
Location: https://acme-v02.api.letsencrypt.org/acme/chall-v3/269111998346/0qH8Ig
Replay-Nonce: kQ7ZnGjxpNSMd0goSQRzZy3G95bz79TDvroGvgEq2gMaU5EYvIY
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
{
"type": "http-01",
"status": "pending",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/269111998346/0qH8Ig",
"token": "fEY1l3F53peC8bZOuY6TR575AB2aN8KlQ7xME_pW_OQ"
}
2023-09-29 17:40:33,218:DEBUG:acme.client:Storing nonce: kQ7ZnGjxpNSMd0goSQRzZy3G95bz79TDvroGvgEq2gMaU5EYvIY
2023-09-29 17:40:33,219:INFO:certbot._internal.auth_handler:Waiting for verification...
2023-09-29 17:40:34,219:DEBUG:acme.client:JWS payload:
b''
2023-09-29 17:40:34,220:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/authz-v3/269111998346:
{
"protected": "eyJhbGciOiAiUlMyNTYiLCAia2lkIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMTMzNTI3MzQ5NiIsICJub25jZSI6ICJrUTdabkdqeHBOU01kMGdvU1FSelp5M0c5NWJ6NzlURHZyb0d2Z0VxMmdNYVU1RVl2SVkiLCAidXJsIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2F1dGh6LXYzLzI2OTExMTk5ODM0NiJ9",
"signature": "jAMbxu59IxQ-fBHzlhPxHyQ_MuxfsCFjjB9Fs-1RSPdf3v79jke10qlv8CNr89awzUii1j4tfwhCbofrB_w1bXZ7T8aflzHHzjeOK10id7fIR0rHc3Y2sup-JpQLyEEQDlJd1fswi8hseeGkXlJYDHZSqy3cq_iGTvYCnp-ahhul7ozhfi_RbIuX84kC4zELvwPrrbxn99bn938YMlywxUvxWWAL9kfZCIdICE7vNLRrWFqndTViGnsgy_rY96QjXaOOwBAG_NbgE2CfSJJboiRQMc1ZgMULnM-6igBZL1PXjUDCAy9RLbLWnnnZFJiDO5U1tPxcUAofvZ5k1Bn-5A",
"payload": ""
}
2023-09-29 17:40:34,384:DEBUG:acme.client:Received response:
HTTP 200
Server: nginx
Date: Fri, 29 Sep 2023 15:40:34 GMT
Content-Type: application/json
Content-Length: 1017
Connection: keep-alive
Boulder-Requester: 1335273496
Cache-Control: public, max-age=0, no-cache
Link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
Replay-Nonce: kQ7ZnGjxfuuBttMRRnjFiORUs0YSoLZqURB545lBmXVbW-EPGTQ
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
{
"identifier": {
"type": "dns",
"value": "klubben319.se"
},
"status": "invalid",
"expires": "2023-10-06T15:40:32Z",
"challenges": [
{
"type": "http-01",
"status": "invalid",
"error": {
"type": "urn:ietf:params:acme:error:unauthorized",
"detail": "5.152.152.55: Invalid response from http://klubben319.se/.well-known/acme-challenge/fEY1l3F53peC8bZOuY6TR575AB2aN8KlQ7xME_pW_OQ: 404",
"status": 403
},
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/269111998346/0qH8Ig",
"token": "fEY1l3F53peC8bZOuY6TR575AB2aN8KlQ7xME_pW_OQ",
"validationRecord": [
{
"url": "http://klubben319.se/.well-known/acme-challenge/fEY1l3F53peC8bZOuY6TR575AB2aN8KlQ7xME_pW_OQ",
"hostname": "klubben319.se",
"port": "80",
"addressesResolved": [
"5.152.152.55"
],
"addressUsed": "5.152.152.55"
}
],
"validated": "2023-09-29T15:40:33Z"
}
]
}
2023-09-29 17:40:34,384:DEBUG:acme.client:Storing nonce: kQ7ZnGjxfuuBttMRRnjFiORUs0YSoLZqURB545lBmXVbW-EPGTQ
2023-09-29 17:40:34,384:INFO:certbot._internal.auth_handler:Challenge failed for domain klubben319.se
2023-09-29 17:40:34,384:INFO:certbot._internal.auth_handler:http-01 challenge for klubben319.se
2023-09-29 17:40:34,384:DEBUG:certbot._internal.display.obj:Notifying user:
Certbot failed to authenticate some domains (authenticator: webroot). The Certificate Authority reported these problems:
Domain: klubben319.se
Type: unauthorized
Detail: 5.152.152.55: Invalid response from http://klubben319.se/.well-known/acme-challenge/fEY1l3F53peC8bZOuY6TR575AB2aN8KlQ7xME_pW_OQ: 404
Hint: The Certificate Authority failed to download the temporary challenge files created by Certbot. Ensure that the listed domains serve their content from the provided --webroot-path/-w and that files created there can be downloaded from the internet.
2023-09-29 17:40:34,385:DEBUG:certbot._internal.error_handler:Encountered exception:
Traceback (most recent call last):
File "/usr/lib/python3/dist-packages/certbot/_internal/auth_handler.py", line 106, in handle_authorizations
self._poll_authorizations(authzrs, max_retries, best_effort)
File "/usr/lib/python3/dist-packages/certbot/_internal/auth_handler.py", line 206, in _poll_authorizations
raise errors.AuthorizationError('Some challenges have failed.')
certbot.errors.AuthorizationError: Some challenges have failed.
2023-09-29 17:40:34,385:DEBUG:certbot._internal.error_handler:Calling registered functions
2023-09-29 17:40:34,385:INFO:certbot._internal.auth_handler:Cleaning up challenges
2023-09-29 17:40:34,385:DEBUG:certbot._internal.plugins.webroot:Removing /data/letsencrypt-acme-challenge/.well-known/acme-challenge/fEY1l3F53peC8bZOuY6TR575AB2aN8KlQ7xME_pW_OQ
2023-09-29 17:40:34,385:DEBUG:certbot._internal.plugins.webroot:All challenges cleaned up
2023-09-29 17:40:34,385:DEBUG:certbot._internal.log:Exiting abnormally:
Traceback (most recent call last):
File "/usr/bin/certbot", line 33, in <module>
sys.exit(load_entry_point('certbot==2.1.0', 'console_scripts', 'certbot')())
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/certbot/main.py", line 19, in main
return internal_main.main(cli_args)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/certbot/_internal/main.py", line 1736, in main
return config.func(config, plugins)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/certbot/_internal/main.py", line 1590, in certonly
lineage = _get_and_save_cert(le_client, config, domains, certname, lineage)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/certbot/_internal/main.py", line 138, in _get_and_save_cert
lineage = le_client.obtain_and_enroll_certificate(domains, certname)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/certbot/_internal/client.py", line 516, in obtain_and_enroll_certificate
cert, chain, key, _ = self.obtain_certificate(domains)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/certbot/_internal/client.py", line 428, in obtain_certificate
orderr = self._get_order_and_authorizations(csr.data, self.config.allow_subset_of_names)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/certbot/_internal/client.py", line 496, in _get_order_and_authorizations
authzr = self.auth_handler.handle_authorizations(orderr, self.config, best_effort)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/certbot/_internal/auth_handler.py", line 106, in handle_authorizations
self._poll_authorizations(authzrs, max_retries, best_effort)
File "/usr/lib/python3/dist-packages/certbot/_internal/auth_handler.py", line 206, in _poll_authorizations
raise errors.AuthorizationError('Some challenges have failed.')
certbot.errors.AuthorizationError: Some challenges have failed.
2023-09-29 17:40:34,386:ERROR:certbot._internal.log:Some challenges have failed.
My web server is (include version):
The operating system my web server runs on is (include version):
Proxmox VE 8.04 with Nginx running in LXC container with Debian
My hosting provider, if applicable, is:
I can login to a root shell on my machine (yes or no, or I don't know):
yes
I'm using a control panel to manage my site (no, or provide the name and version of the control panel):
NPM
The version of my client is (e.g. output of certbot --version or certbot-auto --version if you're using Certbot): 2.10
Additonal info:
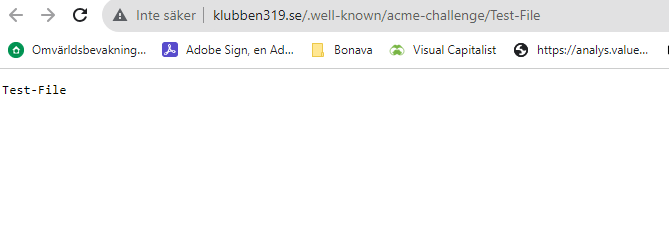
Tried to create file in /.well-known/acme-challenge and can access it:
http://klubben319.se/.well-known/acme-challenge/Test-File