comm -23 <(postconf -n) <(postconf -d) 2>&1 | grep -E “^smtpd_”
smtpd_banner = $myhostname ESMTP
smtpd_client_connection_count_limit = 25
smtpd_client_restrictions = permit_sasl_authenticated, check_client_access hash:/etc/postfix/whitelist, permit_mynetworks, reject_unauth_destination, reject_invalid_hostname, reject_unknown_client, reject_rbl_client sbl-xbl.spamhaus.org, permit
smtpd_data_restrictions = reject_unauth_pipelining, permit
smtpd_delay_reject = yes
smtpd_enforce_tls = no
smtpd_helo_required = yes
smtpd_helo_restrictions = permit_sasl_authenticated, permit_mynetworks, check_helo_access hash:/etc/postfix/helo_access, reject_unauth_pipelining, reject_invalid_hostname, permit
smtpd_milters = unix:/spamass/spamass.sock, inet:localhost:12301
smtpd_recipient_limit = 1000
smtpd_recipient_restrictions = permit_mynetworks, permit_sasl_authenticated, check_client_access hash:/etc/postfix/whitelist, reject_invalid_hostname, reject_unauth_destination, reject_unauth_pipelining, reject_non_fqdn_recipient, reject_non_fqdn_hostname, reject_non_fqdn_sender, reject_unknown_recipient_domain, reject_unknown_sender_domain, reject_unverified_recipient, reject_rbl_client sbl-xbl.spamhaus.org, check_policy_service unix:private/policy-spf, check_client_access hash:/etc/postfix/blacklist, check_policy_service inet:127.0.0.1:10023, permit
smtpd_relay_restrictions = permit_mynetworks, permit_sasl_authenticated, reject_invalid_hostname, reject_unauth_destination, reject_unauth_pipelining, reject_non_fqdn_recipient, reject_non_fqdn_hostname, reject_non_fqdn_sender, reject_unknown_recipient_domain, reject_unknown_sender_domain, reject_unverified_recipient, reject_rbl_client sbl-xbl.spamhaus.org
smtpd_sasl_auth_enable = yes
smtpd_sasl_authenticated_header = yes
smtpd_sasl_local_domain =
smtpd_sasl_path = private/auth
smtpd_sasl_security_options = noanonymous
smtpd_sasl_tls_security_options = $smtpd_sasl_security_options
smtpd_sasl_type = dovecot
smtpd_sender_restrictions = permit_sasl_authenticated, permit_mynetworks, reject_non_fqdn_sender, reject_unknown_sender_domain, reject_unknown_address permit
smtpd_tls_auth_only = yes
smtpd_tls_chain_files = /etc/letsencrypt/live/www.eehmke.de/privkey.pem, /etc/letsencrypt/live/www.eehmke.de/fullchain.pem
smtpd_tls_loglevel = 1
smtpd_tls_protocols = !SSLv2, !SSLv3
smtpd_tls_received_header = yes
smtpd_tls_security_level = may
smtpd_use_tls = yes

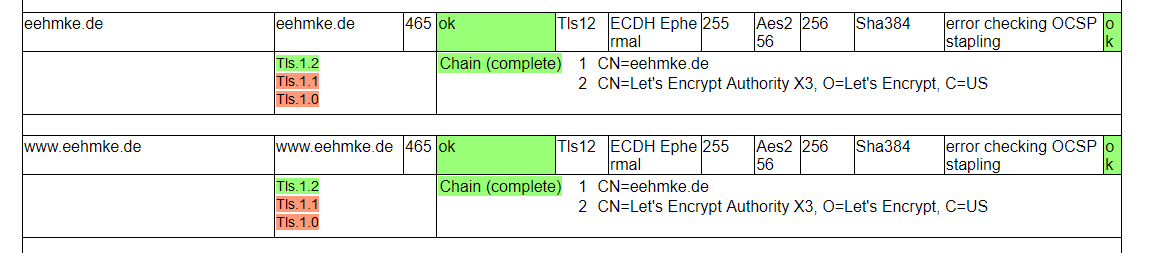

 No other ideas left.
No other ideas left.