Please fill out the fields below so we can help you better. Note: you must provide your domain name to get help. Domain names for issued certificates are all made public in Certificate Transparency logs (e.g. https://crt.sh/?q=example.com), so withholding your domain name here does not increase secrecy, but only makes it harder for us to provide help.
My domain is:kodi.pjrawlings.co.uk
I ran this command:
certbot --nginx
It produced this output:
pi@kodi:~ $ sudo certbot --nginx
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Plugins selected: Authenticator nginx, Installer nginx
Which names would you like to activate HTTPS for?
Select the appropriate numbers separated by commas and/or spaces, or leave input
blank to select all options shown (Enter 'c' to cancel): 1
Cert is due for renewal, auto-renewing...
Renewing an existing certificate
Performing the following challenges:
http-01 challenge for kodi.pjrawlings.co.uk
Waiting for verification...
Cleaning up challenges
Failed authorization procedure. kodi.pjrawlings.co.uk (http-01): urn:ietf:params:acme:error:dns :: No valid IP addresses found for kodi.pjrawlings.co.uk
IMPORTANT NOTES:
-
The following errors were reported by the server:
Domain: kodi.pjrawlings.co.uk
Type: None
Detail: No valid IP addresses found for kodi.pjrawlings.co.uk
pi@kodi:~ $
My web server is (include version):
nginx version: nginx/1.14.2
The operating system my web server runs on is (include version):
Raspbian GNU/Linux 10 (buster)
My hosting provider, if applicable, is:
IONOS
I can login to a root shell on my machine (yes or no, or I don't know):
Yes
I'm using a control panel to manage my site (no, or provide the name and version of the control panel):
No using command line
The version of my client is (e.g. output of certbot --version or certbot-auto --version if you're using Certbot):
certbot 0.31.0
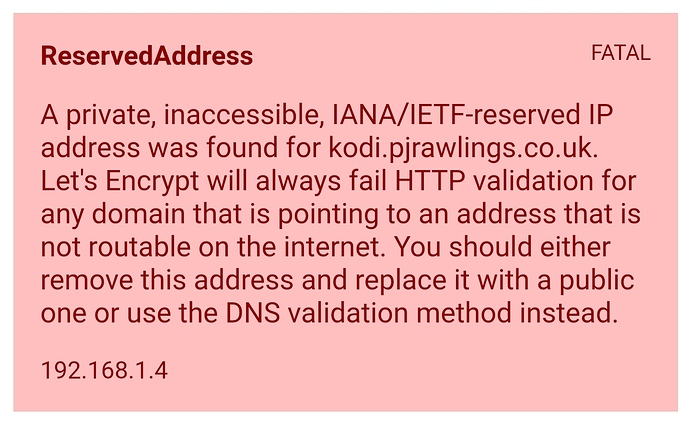
Output from https://check-your-website.server-daten.de/?q=kodi.pjrawlings.co.uk suggests I have A record so not sure what the issue is.
To date I have always created my certificates with the command
sudo certbot -d kodi.pjrawlings.co.uk --manual --preferred-challenges dns certonly --force-interactive
But as I have a nginx server on this machine I would like to use renew and hopefully work through getting this to renew automatically.