when i try access my server from android system the certificate appear as not trusted, so is there any setting or batched for this ?
Hi @allam, as far as I know, it should work from Android 2.3.6 so if you have a newer version maybe the problem is that you didn’t include the intermediate certificate in your web server. If you can provide your domain name we could check it for you.
Cheers,
sahsanu
https://ebank.reb.sy
the error is:
The site’s security certificate is not trusted!
You attempted to reach ebank.reb.sy, but the server presented a certificate issued by an entity that is not trusted by your computer’s operating system. This may mean that the server has generated its own security credentials, which Chrome cannot rely on for identity information, or an attacker may be trying to intercept your communications.
You cannot proceed because the website operator has requested heightened security for this domain.
Back to safety
Help me understand
@allam, yes, your web server doesn’t include the intermediate cert, well, it includes one intermediate certificate but not the right one, you are serving the intermediate certificate for Let's Encrypt Authority X1 but you should include the right intermediate cert that in your case is Let's Encrypt Authority X3.
Edit: I think you are using IIS so maybe you are suffering a caching problem and your IIS is still serving the old X1 intermediate certificate, if that is the case, this thread could be useful to you IIS 8.5 building incorrect chain with Lets Encrypt Authority X3 and this post provides a solution IIS 8.5 building incorrect chain with Lets Encrypt Authority X3
I hope this helps.
sahsanu

this is what i find on intermediate on iis server
I’ve just edited my previous post but I answer again, you should remove the X1 certificate. The problem is that even removing the X1 certificate IIS could be serving it and it is because the certificate is held by SYSTEM user, as I said, this is the thread IIS 8.5 building incorrect chain with Lets Encrypt Authority X3 and this is the solution to remove the X1 certificate IIS 8.5 building incorrect chain with Lets Encrypt Authority X3 .
First try to remove the X1 certificate and if it still doesn’t work, try the solution in above post to remove it using the SYSTEM user.
completely unrelated…
But the site security could be improved:
https://www.ssllabs.com/ssltest/analyze.html?d=ebank.reb.sy&hideResults=on
shows:
server cipher preferred order is not in most to least secure order
TLS_RSA_WITH_AES_128_CBC_SHA256 (0x3c) 128
TLS_RSA_WITH_AES_128_CBC_SHA (0x2f) 128
TLS_RSA_WITH_AES_256_CBC_SHA256 (0x3d) 256
TLS_RSA_WITH_AES_256_CBC_SHA (0x35) 256
TLS_RSA_WITH_3DES_EDE_CBC_SHA (0xa) WEAK 112
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (0xc027) ECDH secp256r1 (eq. 3072 bits RSA) FS 128
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (0xc013) ECDH secp256r1 (eq. 3072 bits RSA) FS 128
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (0xc014) ECDH secp256r1 (eq. 3072 bits RSA) FS 256
and most browsers will be forced to connect without forwarding secrecy.
Also: ECDH public server param reuse Yes
even the curves are in weakest to strongest order:
Supported EC Named Curves secp256r1, secp384r1 (server preferred order)
Hi @sahsanu
IIS is smart enough to use the correct certificate to include in the chain even if non relevant Intermediates are installed.
Also the correct intermediate is now being served https://www.ssllabs.com/ssltest/analyze.html?d=ebank.reb.sy&hideResults=on
@allam if you have a look at the results
For clients with your current SSL configuration
If you have a native app running certificates should be trusted so should fairly new versions of chrome.
What browser is the user using or are they using a native app?
Below is an emulated Galaxy5 device with your website showing no issues
Andrei
Hi @ahaw021,
It seems not so smart enough regarding the previous and long post ![]() IIS 8.5 building incorrect chain with Lets Encrypt Authority X3
IIS 8.5 building incorrect chain with Lets Encrypt Authority X3
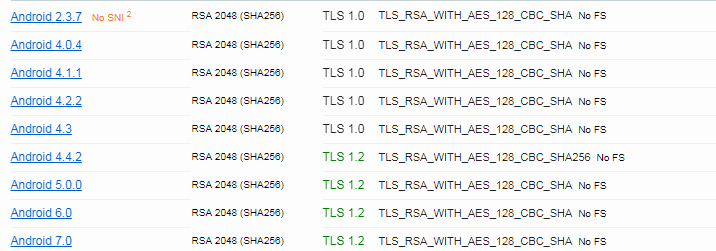
Well, it is and it isn't ;), right now it is serving the intermediate certificate for Let's Encrypt Authority X3 BUT issued by ISRG Root X1 instead of the one issued by DST Root CA X3. As far as I know ISRG Root X1 is not included yet in Android, at least it is not in my Android version 7.0.
@allam, just to test, try to remove the intermediate certificate Let's Encrypt Authority X3 issued by ISRG Root X1 and left only the one issued by DST Root CA X3.
Cheers,
sahsanu
hi @sahsanu
I think it is 
Will review the other post. It’s building the right chain as far as I can see.
Micorosoft is also able to differentiate between the two Intermediates
If the intermediate is not present microsoft will show a broken chain not use the “nearest” certificate
Andrei
@ahaw021, not from my side, Firefox browser works fine but Chrome is not as ISRG Root X1 is not included in my Windows version and that is the intermediate certificate server by ebank.reb.sy.
I’m off work today and I don’t have my “English” laptop near so the language of below screenshot is in spanish but you will see that ISRG Root X1 is red marked because it is not included in Trusted CAs.
The same in Android (tested with Boat Browser, Opera an Chrome), I receive an error: NET::ERR_CERT_AUTHORITY_INVALID and is because ISRG Root X1 is not yet included in the trusted CAs.
That is the reason I advice @allan to remove the intermediate certificate issued by ISRG Root X1, because for me… and sslabs it is serving this one always instead of the one signed by DST Root CA X3.
Edit: Just to give more info, I installed Firefox browser in my Android device and the site is working fine because Firefox uses its own trusted CA store.
Cheers,
sahsanu
interesting - and weird really weird
i will try the same thing on of our servers (install both Intermediate X3 certs)
will let you know the link to test.
may be a more elegant solution is to include the root in the chain as well but will see.
Andrei
Shouldn’t the fullchain.pem be the right file to serve?
Or is that what is being served and contains incorrect intermediate?
Please post the public fullchain.pem file used.
IIS does not have the concept of fullchain.pem
When you import the certificates in to the store they are broken up in to intermediates and leaf certificates by the microsoft cert store (what IIS uses to access certificates)
So pasting fullchain.pem is not much use as most windows won’t have this 
Andrei
IIS…
OK I understand the problem better now.
Just for the records, I’ve checked it again and now it is sending the DST Root CA X3 intermediate certificate so it is working fine in my Android device with all the browsers I tested.
Cheers,
sahsanu
This topic was automatically closed 30 days after the last reply. New replies are no longer allowed.