Hello @StopSpazzing, and @schoen,
Thank you both for the instructions!
@StopSpazzing, I do restart the services on each change of the configuration files. However, Thanks for pointing that out! In regards to permissions, I was thinking about the same issue, however the LetsEncrypt configuration directories are owned by the “system” only. I also think these types of permissions could be a problem as Apache won’t be able to access the folder to read it’s content. So, we both have a point there!
@schoen,
You are absolutely right, Thanks also to point that out and I went back and changed the path string in both; “httpd-ssl.conf”, and “httpd-vhosts.conf” to point to;
SSLCertificateKeyFile “/etc/letsencrypt/live/domain.org/privkey.pem”
SSLCACertificateFile “/etc/letsencrypt/live/domain.org/fullchain.pem”
respectively!
However Apache refused to start and I think that goes back to @StopSpazzing in regards to permissions. In the logs it says;
[Mon Dec 28 09:27:00.586312 2015] [mpm_prefork:notice] [pid xxxxx] AH00169: caught SIGTERM, shutting down
AH00016: Configuration Failed
Starting Apache Web Server…
Exit code: 3
Stdout:
/usr/local/… : httpd could not be started
Stderr:
Syntax OK
So… I think we are going back to the permissions issue then!
Ok! Things I should tell you first!
The Server does have already a class2 Certificate for one of the ecommerce domain I am hosting. However, I think that is not relevant to the other Certificate here. If any of you think there are any conflicts in using 2 certificates for different domains with one single ip address, let me know?
Permissions: When I installed LetsEncrypt, it created the directories in the system on /etc/ with all permissions in place. Here is what is in place. Looking at the permissions, I encounter two issues;
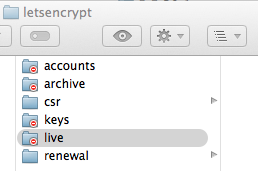
-
/var/logs/letsencrypt/ <— is owned by the system and no access. Therefore Console cannot read them neither do I.
-
LetsEncrypt directory
a. accounts
b. archive
c. csr
d. keys
e. live <--- is owned by the system and no access. Therefore, I think even thou I have the Apache performing as root, with this type of permissions, Apache cannot read them. So, the permission on live directory needs to change to something like; (system: read & write, everyone: read only)
f. renewal
Let me know if my line of thought is going to the right direction so I can change the permissions!
Thanks!
Ps: I think I know what happened with the permissions. Home Brew, one of the LetsEncrypt requirements to install Python to generate the Certificates on the Mac OS System, only install as a client in the Admin User directory and not as Root SuperUser and I think that is the reason LetsEncrypt permissions got that way.





