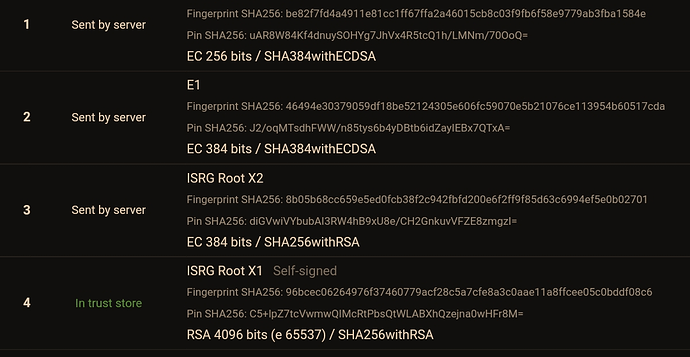
With regards to cipher suites, yes. On TLSv1.2, the cipher suite signature algorithm (RSA/ECDSA) needs to match the one from the cert. The exact elliptic curve used is not negotiated in the cipher suite, though clients can indicate what they support (supported groups extension and others).
Though this is only what the standards say and Microsoft apparently doesn't care too much about those. As I write, I recall that Microsoft used to actually encode the elliptic curve in the internal cipher suite!
(This is solely an internal config thing and has no impact on protocol level cipher suite naming/handling)
That's a very temporary solution though, as Let's Encrypt isn't going to keep the allow-list forever.
As for the Android 7.0 bug, I no longer have access to a test device and it's been some years since I checked the facts, but I believe the BoringSSL version shipped there explicitly states that it will only handle P-256 (in the signature_algorithms extension, or via the supported_groups extension - not sure, maybe both).
OpenSSL servers (at least partially) respect this, but only with regards to the leaf certificate. So if your server is sending a P-256 leaf, but your issuer is P-384, OpenSSL will send the ECDSA certificate, even though that fails on a 7.0 device. However, if your ECDSA leaf is also P-384, OpenSSL should see the incompatibility and fall back to RSA certs, if those are available.
So in theory the 7.0 bug can be worked around by using P-384 leafs and having a fallback RSA ready. Writing this, this makes me considering if I should switch my current ECDSA leafs to P-384. But on the other hand, 7.0 doesn't trust ISRG Root X1 anyway, so the chain offered by LE won't validate by default. Also note that this is only a theory - I was unable to validate this, as my Android 7.0 emulator ships a patched version that handles P-384 just fine (this is also what Qualys states for 7.0) - which is not the case for all real-world 7.0 devices.
[To add to all this confusion, we need to remember that there are actually two algorithms involved that may use ECC: The ECDH(E) key exchange and the ECDSA algorithm. Those algorithms may use different curves in the handshake and may also not support the same ones - in fact, some curves like Curve25519 are not supposed to be used with ECDSA (they're used together with EdDSA)]