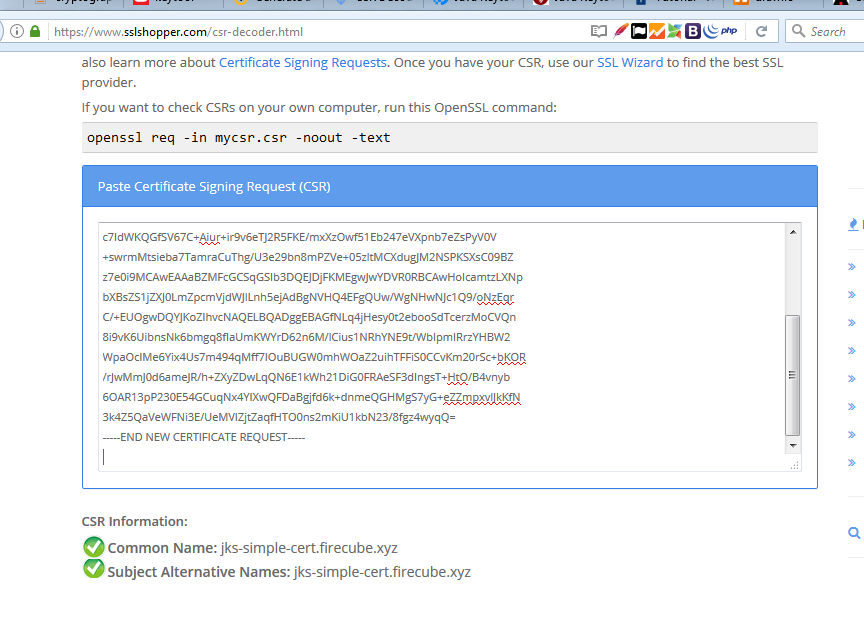
Create a CSR for simple-cert and a CSR for san-cert
Like most processes (e.g. OpenSSL) we generate a CSR from a Private key.
In the case of JKS we are going to use the existing keys in the JKS to create two CSRs.
having a look at the tool help we can see the various options
One option that is not covered is the -ext option which allows us to have X509 V3 extensions (specifically SANs)
CSRS:
The first CSR we will create will have the following parameters
Domain Name: jks-simple-cert.firecube.xyz
SAN Name: jks-simple-cert.firecube.xyz
Key Name (alias): simple-cert
Command:
keytool -certreq -alias simple-cert -keystore letsencrypt.jks -file jks-simple-cert_firecube_xyz.csr -storepass test12345 -ext san=dns:jks-simple-cert.firecube.xyz
The Second CSR we will create will have the following parameters
Domain Name: jks-san-cert.firecube.xyz
SAN Name: jks-san-cert.firecube.xyz, jks-san-cert1.firecube.xyz, jks-san-cert2.firecube.xyz
Key Name (alias): san-cert
Command:
Note: Quote Marks are needed for windows may not be needed for linux
keytool -certreq -alias san-cert -keystore letsencrypt.jks -file jks-san-cert_firecube_xyz.csr -storepass test12345 -ext "san=dns:jks-san-cert.firecube.xyz,dns:jks-san-cert1.firecube.xyz,dns:jks-san-cert2.firecube.xyz"
![]()