@webprofusion
Thank you. Would cycling IIS be sufficient or does it always need a full server reboot?
Also, how safe is IISCrypto?
No unfortunately cycling IIS is not enough, Schannel is the windows secure sockets layer at the kernel level (which IIS is a consumer of), and in my experience it needs a reboot to apply.
I don't personally know the authors of IISCrypto (I don't think so anyway) but I've been using it myself, and recommending it to Certify The Web users, for many years. The name is a bit confusing because it sounds like some kind of unfortunate ransomware, but it's a pretty well respected utility. You can do this stuff with powershell as well, but I wouldn't know exactly what you do or don't need to apply.
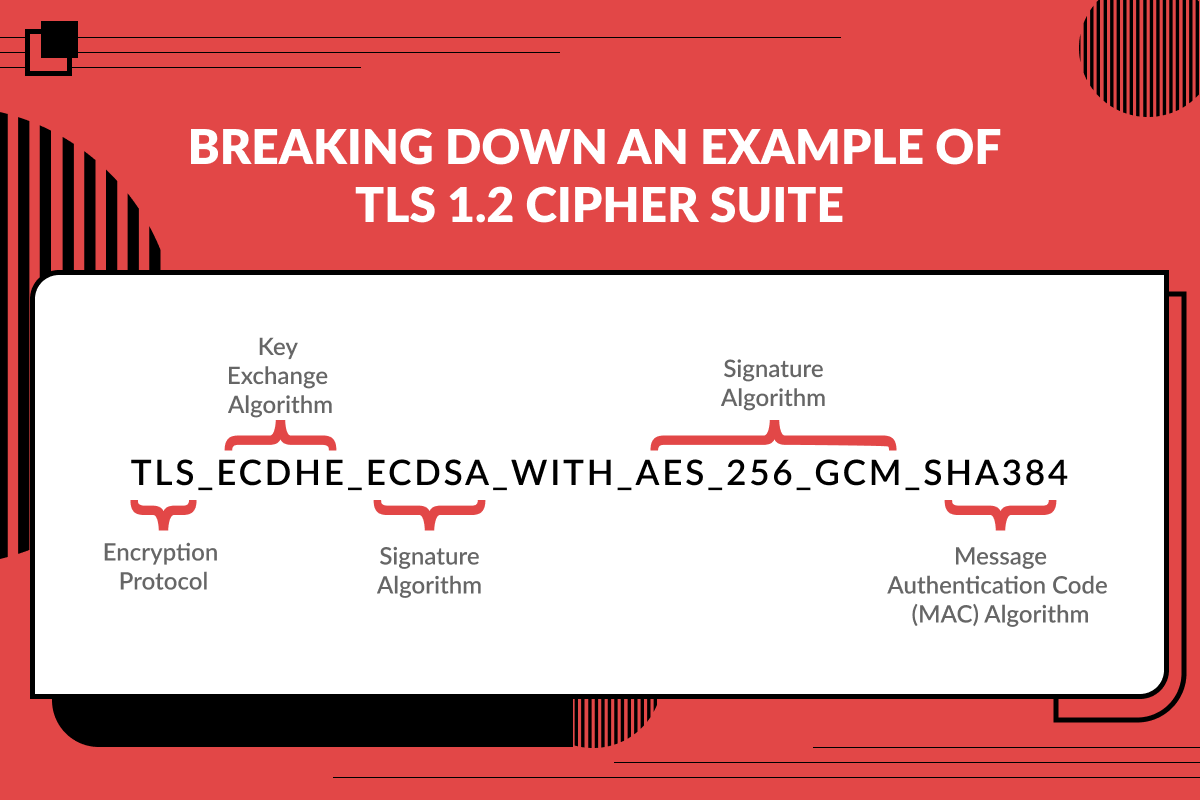
So that's only the RSA-based cipher suites, which will mean that you can't connect to any systems using ECDSA, which is a bigger and bigger part of the Internet.
The ECDSA ones shouldn't be considered "weak". Even if you don't want to use the Nartac software directly, their list of best practice cipher suites looks pretty good to me.
The Microsoft cipher suite documentation (click through the link there to your specific OS version) says,
- To use group policy, configure SSL Cipher Suite Order under Computer Configuration > Administrative Templates > Network > SSL Configuration Settings with the priority list for all cipher suites you want enabled.
So that's probably the "official" method, though I think the utility is just doing the same thing under the hood. How did you disable these cipher suites in the first place? You can probably use the same method to reenable the ECDSA ones.
Be aware that Let's Encrypt regularly changes where they're validating from. They need to make sure that you control the domain name as seen from everywhere on the Internet, since they're issuing a certificate that's valid for everywhere on the Internet. I'm going to post again the link that Bruce posted:
An update:
I tried, via a combination of IISCrypto and manual editing in the Group Policy, to add the ECDHE_ECDSA ciphers that apparently were needed to connect to acme-v02.api.letsencrypt.org .
This didn’t make those ciphers get picked up by SSLlabs.com in a test…
However, retrying the certificate issuing did work this time.
I quickly ran a test on acme-v02.api.letsencrypt.org via SSLlabs to see if they had added other ciphers back in on their side, but they haven’t…
What we’ll do is let things run over the weekend and then we can check the logs on Monday to see if the daily processes connected ok. I don’t understand why the ciphers listed in IISCrypto and through (get-tlsciphersuite).name in Powershell differ from those in Group Policy, why the ECDHE_ECDSA ones listed in those places don’t show in SSLLabs and why Let’s Encrypt worked after this. However, work it did!
I'll report back on Monday about whether it went back to failing to connect. Meanwhile thanks for all the help.
SSLLabs checking your site is testing which cipher suites your server is accepting. If you're using an RSA key, then the ECDSA ones wouldn't be in that list. All that's changed is the key type of the Let's Encrypt API. You need to enable them for your server's outbound connections, even though you wouldn't be using them for your server's inbound connections.
ok, so the ECDSA ones could be active then for outbound even if SSLlabs doesn't list them.
Interesting and a bit over my head but if it works that's great!
So many useful replies, can multiple be marked as solutions?
Yes, you've got it.
No, you have to just pick one. But I don't know how many people are keeping score of who gets what solution count anyway. (I know I'm not.)
Just for info, if your own site has a certificate using an RSA public/privatekey pair then the client communication (Qualsys talking to you) uses a cipher suite that includes RSA. If you used an EC key instead for your own cert then the cipher suites negotiated would be different (ECDSA).
All good for 3 days so updating the ciphers looks good as the fix.
Thank you
This topic was automatically closed 30 days after the last reply. New replies are no longer allowed.