Hi,yuvaspandana.in
I tried installing an SSL Certificate Using DNS Validation with acme-dns-certbot Ubuntu 18.04 by following the steps mentioned here:
The response on the terminal said: https://prnt.sc/1qv51pn
But still, I'm unable to see the SSL icon on the website.
I also tried checking if the SSL is installed properly using: SSL Checker - It said: https://prnt.sc/1qv540v
I also ran the sudo ufw status command to check the ufw status ,https://prnt.sc/1qv55xc
I'm wondering what did I miss here or do wrong? Could someone please help me out?
Osiris
August 31, 2021, 9:00am
2
That's to be expected. The guide you're refering to only lets you acquire a certificate. So now you have the certificate and you need to implement it in whatever webserver you've got running.
Also, do you actually require acme-dns-certbot? If I look at the acquired certificates for your domain at crt.sh | yuvaspandana.in I don't see a wildcard certificate, so that's probably not the reason you're using the dns-01 challenge. Maybe because your port 80 is blocked?
I do wonder what happened to all the other certificates if you're still not seeing a SSL icon on your website. Unfortunately, I'm unable to check as it seems your site is not available from my location.
Hi @Osiris , First of all - this is for one of our client's sites.
We are using Ubuntu 18.04 with Apache.
Yes, The server setup of this client is unnecessarily complicated.
They are not letting us connect to their server without a VPN - So everything including SSH Access / FTP Access we should connect to their server via a VPN as they have blocked the PORT 22
We tried the normal method - But it failed as the scripts could not access the server (due to the reason mentioned in point 1)
I also created the .well-known and tried from SSLFORFREE.COM Website - The same issue where it was unable to fetch the files.
So DNS VERIFICATIONS was the only way!
Osiris
August 31, 2021, 10:21am
4
Makes sense. Luckily, that worked!
If you're not uncomfortable with certbot modifying your Apache configuration, you could try to use the certbot install command to let certbot install the certificate into Apache.
@Osiris - My god!!! You are a life saver!
Osiris:
certbot install
And i can't believe my eyes - SSL IS NOW CONFIGURED.
I have spent days searching the internet to find a proper solution - Never knew it would have been done from this simple command..
Thanks a lot!
Just wanted to confirm, Which certificate did this command apply to now? The one I got from the acme-dns-certbot
Osiris
August 31, 2021, 10:28am
6
I'm guessing the certbot output should have told you which certificate was installed?
You can check all the available certificates in certbot with the command:
certbot certificates
It probably should show only one if you have had trouble issuing certs in the past?
Hi @Osiris
Yes, It showed only 1:
And this seems to be the one from the acme-dns-certbot
So are we good to go?
Osiris
August 31, 2021, 10:46am
8
If that's the only certificate you recently got issued and that was done using acme-dns-certbot, then yes.
vgnavada:
So are we good to go?
Probably! It's always a good thing to test renewal for in the future by using the command:
certbot renew --dry-run
Also, it wouldn't hurt to check the contents of the renewal configuration file, just to be sure it has marked the "apache" plugin as the installer, so Apache will get reloaded after the renewal. You can see its contents by running:
cat /etc/letsencrypt/renewal/yuvaspandana.in.conf
I ran this:
Osiris:
certbot renew --dry-run
This is the output:
And i also ran this:
And here is the output: Screenshot by Lightshot
Osiris
August 31, 2021, 10:57am
10
Hm, so it seems the certbot install command did NOT actually save the usage of the apache installer unfortunately.. Not sure if that's intended behaviour or a bug. The issue with this is that after a successful renewal, Apache needs to be reloaded so it will load the new certificate. Otherwise your brand new renewed certificate won't be used and the users of your site will keep seeing the old certificate, even after it has expired. So we need to make sure Apache is reloaded after a successful renewal.
Not to worry, there are other methods of doing that. Could you try running:
certbot renew --dry-run --deploy-hook "apachectl -k graceful"
And check that the deploy hook indeed gracefully reloads Apache?
Hello,
I ran this:
Here is the output:
Is it working as expected? Anything to worry?
Osiris
August 31, 2021, 11:26am
12
Hm, it seems the deploy hook is skipped when testing with --dry-run, so hard to say.
Does running the command sudo apachectl -k graceful on its own work?
I ran this, here is the output - I did not get any response:
Osiris
August 31, 2021, 11:58am
14
Neither does it on my server. However, the error_log did have the following entry:
[Tue Aug 31 13:31:18.563559 2021] [mpm_event:notice] [pid 3241:tid 139733636821952] AH00493: SIGUSR1 received. Doing graceful restart
So I guess no output is good.
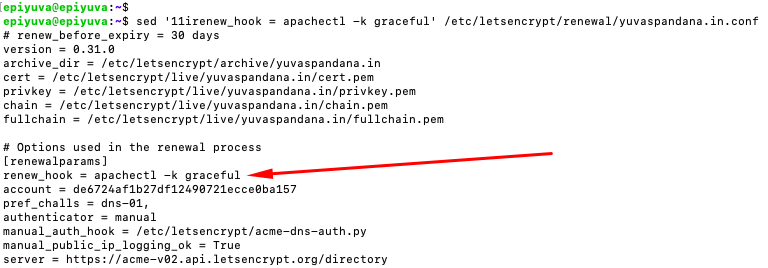
Now we only need to implement the graceful command into a working deploy hook. We can manually modify the renewal configuration file, as unfortunately there is no user interface in certbot to do so without issuing a brand new certificate unnecessarily. Luckily, it's rather simple. Please take a look to the output of the following command (note: this won't modify the renewal configuration file just yet ):
sed '11irenew_hook = apachectl -k graceful' /etc/letsencrypt/renewal/yuvaspandana.in.conf
This does the following in sed:
11 marks the line number of where we want to do somethingi is the "insert" commandthe rest of the option to sed is just the value we want to have inserted, which is the deploy hook, which for some reason is called "renew_hook" in the configuration file....
This should output your renewal configuration file but with the line
renew_hook = apachectl -k graceful
just under the [renewparams] line.
If that's the case, you can re-run the same sed command, but now with the -i option, so it will actually modify the renewal configuration file:
sed -i '11irenew_hook = apachectl -k graceful' /etc/letsencrypt/renewal/yuvaspandana.in.conf
After that, you can test the newly made renewal configuration file using: certbot renew --dry-run. It should output:
Dry run: skipping deploy hook command: apachectl -k graceful
If that's the case, you're good to go!
Hi @Osiris ,
Here is the output. It did come as you said:
Then, I re-ran this:
No output: https://prnt.sc/1qvmgfz
Finally, I ran:
Here is the output: https://prnt.sc/1qvmo7i
All good?
Osiris
August 31, 2021, 12:27pm
16
vgnavada:
All good?
As far as I can tell: yes!
For 200 % certainty, you can check if apt installed the systemd timer which will automatically renew your certificate:
systemctl show certbot.timer
I got a huge response, Unable to parse it:
epiyuva@epiyuva:~$ systemctl show certbot.timer
Unit=certbot.service
NextElapseUSecRealtime=Tue 2021-08-31 22:29:33 IST
NextElapseUSecMonotonic=0
LastTriggerUSec=Tue 2021-08-31 00:06:13 IST
LastTriggerUSecMonotonic=0
Result=success
AccuracyUSec=1min
RandomizedDelayUSec=12h
Persistent=yes
WakeSystem=no
RemainAfterElapse=yes
Id=certbot.timer
Names=certbot.timer
Requires=sysinit.target -.mount
WantedBy=timers.target
Conflicts=shutdown.target
Before=shutdown.target certbot.service timers.target
After=sysinit.target -.mount time-sync.target
Triggers=certbot.service
RequiresMountsFor=/var/lib/systemd/timers
Description=Run certbot twice daily
LoadState=loaded
ActiveState=active
SubState=waiting
FragmentPath=/lib/systemd/system/certbot.timer
UnitFileState=enabled
UnitFilePreset=enabled
StateChangeTimestamp=Tue 2021-08-31 12:44:40 IST
StateChangeTimestampMonotonic=7105889
InactiveExitTimestamp=Tue 2021-08-31 12:44:40 IST
InactiveExitTimestampMonotonic=7105889
ActiveEnterTimestamp=Tue 2021-08-31 12:44:40 IST
ActiveEnterTimestampMonotonic=7105889
ActiveExitTimestampMonotonic=0
InactiveEnterTimestampMonotonic=0
CanStart=yes
CanStop=yes
CanReload=no
CanIsolate=no
StopWhenUnneeded=no
RefuseManualStart=no
RefuseManualStop=no
AllowIsolate=no
DefaultDependencies=yes
lines 1-44...skipping...
Unit=certbot.service
NextElapseUSecRealtime=Tue 2021-08-31 22:29:33 IST
NextElapseUSecMonotonic=0
LastTriggerUSec=Tue 2021-08-31 00:06:13 IST
LastTriggerUSecMonotonic=0
Result=success
AccuracyUSec=1min
RandomizedDelayUSec=12h
Persistent=yes
WakeSystem=no
RemainAfterElapse=yes
Id=certbot.timer
Names=certbot.timer
Requires=sysinit.target -.mount
WantedBy=timers.target
Conflicts=shutdown.target
Before=shutdown.target certbot.service timers.target
After=sysinit.target -.mount time-sync.target
Triggers=certbot.service
RequiresMountsFor=/var/lib/systemd/timers
Description=Run certbot twice daily
LoadState=loaded
ActiveState=active
SubState=waiting
FragmentPath=/lib/systemd/system/certbot.timer
UnitFileState=enabled
UnitFilePreset=enabled
StateChangeTimestamp=Tue 2021-08-31 12:44:40 IST
StateChangeTimestampMonotonic=7105889
InactiveExitTimestamp=Tue 2021-08-31 12:44:40 IST
InactiveExitTimestampMonotonic=7105889
ActiveEnterTimestamp=Tue 2021-08-31 12:44:40 IST
ActiveEnterTimestampMonotonic=7105889
ActiveExitTimestampMonotonic=0
InactiveEnterTimestampMonotonic=0
CanStart=yes
CanStop=yes
CanReload=no
CanIsolate=no
StopWhenUnneeded=no
RefuseManualStart=no
RefuseManualStop=no
AllowIsolate=no
DefaultDependencies=yes
OnFailureJobMode=replace
lines 1-45...skipping...
Unit=certbot.service
NextElapseUSecRealtime=Tue 2021-08-31 22:29:33 IST
NextElapseUSecMonotonic=0
LastTriggerUSec=Tue 2021-08-31 00:06:13 IST
LastTriggerUSecMonotonic=0
Result=success
AccuracyUSec=1min
RandomizedDelayUSec=12h
Persistent=yes
WakeSystem=no
RemainAfterElapse=yes
Id=certbot.timer
Names=certbot.timer
Requires=sysinit.target -.mount
WantedBy=timers.target
Conflicts=shutdown.target
Before=shutdown.target certbot.service timers.target
After=sysinit.target -.mount time-sync.target
Triggers=certbot.service
RequiresMountsFor=/var/lib/systemd/timers
Description=Run certbot twice daily
LoadState=loaded
ActiveState=active
SubState=waiting
FragmentPath=/lib/systemd/system/certbot.timer
UnitFileState=enabled
UnitFilePreset=enabled
StateChangeTimestamp=Tue 2021-08-31 12:44:40 IST
StateChangeTimestampMonotonic=7105889
InactiveExitTimestamp=Tue 2021-08-31 12:44:40 IST
InactiveExitTimestampMonotonic=7105889
ActiveEnterTimestamp=Tue 2021-08-31 12:44:40 IST
ActiveEnterTimestampMonotonic=7105889
ActiveExitTimestampMonotonic=0
InactiveEnterTimestampMonotonic=0
CanStart=yes
CanStop=yes
CanReload=no
CanIsolate=no
StopWhenUnneeded=no
RefuseManualStart=no
RefuseManualStop=no
AllowIsolate=no
DefaultDependencies=yes
OnFailureJobMode=replace
IgnoreOnIsolate=no
lines 1-46...skipping...
Unit=certbot.service
NextElapseUSecRealtime=Tue 2021-08-31 22:29:33 IST
NextElapseUSecMonotonic=0
LastTriggerUSec=Tue 2021-08-31 00:06:13 IST
LastTriggerUSecMonotonic=0
Result=success
AccuracyUSec=1min
RandomizedDelayUSec=12h
Persistent=yes
WakeSystem=no
RemainAfterElapse=yes
Id=certbot.timer
Names=certbot.timer
Requires=sysinit.target -.mount
WantedBy=timers.target
Conflicts=shutdown.target
Before=shutdown.target certbot.service timers.target
After=sysinit.target -.mount time-sync.target
Triggers=certbot.service
RequiresMountsFor=/var/lib/systemd/timers
Description=Run certbot twice daily
LoadState=loaded
ActiveState=active
SubState=waiting
FragmentPath=/lib/systemd/system/certbot.timer
UnitFileState=enabled
UnitFilePreset=enabled
StateChangeTimestamp=Tue 2021-08-31 12:44:40 IST
StateChangeTimestampMonotonic=7105889
InactiveExitTimestamp=Tue 2021-08-31 12:44:40 IST
InactiveExitTimestampMonotonic=7105889
ActiveEnterTimestamp=Tue 2021-08-31 12:44:40 IST
ActiveEnterTimestampMonotonic=7105889
ActiveExitTimestampMonotonic=0
InactiveEnterTimestampMonotonic=0
CanStart=yes
CanStop=yes
CanReload=no
CanIsolate=no
StopWhenUnneeded=no
RefuseManualStart=no
RefuseManualStop=no
AllowIsolate=no
DefaultDependencies=yes
OnFailureJobMode=replace
IgnoreOnIsolate=no
NeedDaemonReload=no
lines 1-47...skipping...
Unit=certbot.service
NextElapseUSecRealtime=Tue 2021-08-31 22:29:33 IST
NextElapseUSecMonotonic=0
LastTriggerUSec=Tue 2021-08-31 00:06:13 IST
LastTriggerUSecMonotonic=0
Result=success
AccuracyUSec=1min
RandomizedDelayUSec=12h
Persistent=yes
WakeSystem=no
RemainAfterElapse=yes
Id=certbot.timer
Names=certbot.timer
Requires=sysinit.target -.mount
WantedBy=timers.target
Conflicts=shutdown.target
Before=shutdown.target certbot.service timers.target
After=sysinit.target -.mount time-sync.target
Triggers=certbot.service
RequiresMountsFor=/var/lib/systemd/timers
Description=Run certbot twice daily
LoadState=loaded
ActiveState=active
SubState=waiting
FragmentPath=/lib/systemd/system/certbot.timer
UnitFileState=enabled
UnitFilePreset=enabled
StateChangeTimestamp=Tue 2021-08-31 12:44:40 IST
StateChangeTimestampMonotonic=7105889
InactiveExitTimestamp=Tue 2021-08-31 12:44:40 IST
InactiveExitTimestampMonotonic=7105889
ActiveEnterTimestamp=Tue 2021-08-31 12:44:40 IST
ActiveEnterTimestampMonotonic=7105889
ActiveExitTimestampMonotonic=0
InactiveEnterTimestampMonotonic=0
CanStart=yes
CanStop=yes
CanReload=no
CanIsolate=no
StopWhenUnneeded=no
RefuseManualStart=no
RefuseManualStop=no
AllowIsolate=no
DefaultDependencies=yes
OnFailureJobMode=replace
IgnoreOnIsolate=no
NeedDaemonReload=no
JobTimeoutUSec=infinity
lines 1-48...skipping...
Unit=certbot.service
NextElapseUSecRealtime=Tue 2021-08-31 22:29:33 IST
NextElapseUSecMonotonic=0
LastTriggerUSec=Tue 2021-08-31 00:06:13 IST
LastTriggerUSecMonotonic=0
Result=success
AccuracyUSec=1min
RandomizedDelayUSec=12h
Persistent=yes
WakeSystem=no
RemainAfterElapse=yes
Id=certbot.timer
Names=certbot.timer
Requires=sysinit.target -.mount
WantedBy=timers.target
Conflicts=shutdown.target
Before=shutdown.target certbot.service timers.target
After=sysinit.target -.mount time-sync.target
Triggers=certbot.service
RequiresMountsFor=/var/lib/systemd/timers
Description=Run certbot twice daily
LoadState=loaded
ActiveState=active
SubState=waiting
FragmentPath=/lib/systemd/system/certbot.timer
UnitFileState=enabled
UnitFilePreset=enabled
StateChangeTimestamp=Tue 2021-08-31 12:44:40 IST
StateChangeTimestampMonotonic=7105889
InactiveExitTimestamp=Tue 2021-08-31 12:44:40 IST
InactiveExitTimestampMonotonic=7105889
ActiveEnterTimestamp=Tue 2021-08-31 12:44:40 IST
ActiveEnterTimestampMonotonic=7105889
ActiveExitTimestampMonotonic=0
InactiveEnterTimestampMonotonic=0
CanStart=yes
CanStop=yes
CanReload=no
CanIsolate=no
StopWhenUnneeded=no
RefuseManualStart=no
RefuseManualStop=no
AllowIsolate=no
DefaultDependencies=yes
OnFailureJobMode=replace
IgnoreOnIsolate=no
NeedDaemonReload=no
JobTimeoutUSec=infinity
JobRunningTimeoutUSec=infinity
lines 1-49...skipping...
Unit=certbot.service
NextElapseUSecRealtime=Tue 2021-08-31 22:29:33 IST
NextElapseUSecMonotonic=0
LastTriggerUSec=Tue 2021-08-31 00:06:13 IST
LastTriggerUSecMonotonic=0
Result=success
AccuracyUSec=1min
RandomizedDelayUSec=12h
Persistent=yes
WakeSystem=no
RemainAfterElapse=yes
Id=certbot.timer
Names=certbot.timer
Requires=sysinit.target -.mount
WantedBy=timers.target
Conflicts=shutdown.target
Before=shutdown.target certbot.service timers.target
After=sysinit.target -.mount time-sync.target
Triggers=certbot.service
RequiresMountsFor=/var/lib/systemd/timers
Description=Run certbot twice daily
LoadState=loaded
ActiveState=active
SubState=waiting
FragmentPath=/lib/systemd/system/certbot.timer
UnitFileState=enabled
UnitFilePreset=enabled
StateChangeTimestamp=Tue 2021-08-31 12:44:40 IST
StateChangeTimestampMonotonic=7105889
InactiveExitTimestamp=Tue 2021-08-31 12:44:40 IST
InactiveExitTimestampMonotonic=7105889
ActiveEnterTimestamp=Tue 2021-08-31 12:44:40 IST
ActiveEnterTimestampMonotonic=7105889
ActiveExitTimestampMonotonic=0
InactiveEnterTimestampMonotonic=0
CanStart=yes
CanStop=yes
CanReload=no
CanIsolate=no
StopWhenUnneeded=no
RefuseManualStart=no
RefuseManualStop=no
AllowIsolate=no
DefaultDependencies=yes
OnFailureJobMode=replace
IgnoreOnIsolate=no
NeedDaemonReload=no
JobTimeoutUSec=infinity
JobRunningTimeoutUSec=infinity
JobTimeoutAction=none
lines 1-50...skipping...
Unit=certbot.service
NextElapseUSecRealtime=Tue 2021-08-31 22:29:33 IST
NextElapseUSecMonotonic=0
LastTriggerUSec=Tue 2021-08-31 00:06:13 IST
LastTriggerUSecMonotonic=0
Result=success
AccuracyUSec=1min
RandomizedDelayUSec=12h
Persistent=yes
WakeSystem=no
RemainAfterElapse=yes
Id=certbot.timer
Names=certbot.timer
Requires=sysinit.target -.mount
WantedBy=timers.target
Conflicts=shutdown.target
Before=shutdown.target certbot.service timers.target
After=sysinit.target -.mount time-sync.target
Triggers=certbot.service
RequiresMountsFor=/var/lib/systemd/timers
Description=Run certbot twice daily
LoadState=loaded
ActiveState=active
SubState=waiting
FragmentPath=/lib/systemd/system/certbot.timer
UnitFileState=enabled
UnitFilePreset=enabled
StateChangeTimestamp=Tue 2021-08-31 12:44:40 IST
StateChangeTimestampMonotonic=7105889
InactiveExitTimestamp=Tue 2021-08-31 12:44:40 IST
InactiveExitTimestampMonotonic=7105889
ActiveEnterTimestamp=Tue 2021-08-31 12:44:40 IST
ActiveEnterTimestampMonotonic=7105889
ActiveExitTimestampMonotonic=0
InactiveEnterTimestampMonotonic=0
CanStart=yes
CanStop=yes
CanReload=no
CanIsolate=no
StopWhenUnneeded=no
RefuseManualStart=no
RefuseManualStop=no
AllowIsolate=no
DefaultDependencies=yes
OnFailureJobMode=replace
IgnoreOnIsolate=no
NeedDaemonReload=no
JobTimeoutUSec=infinity
JobRunningTimeoutUSec=infinity
JobTimeoutAction=none
ConditionResult=yes
lines 1-51...skipping...
Unit=certbot.service
NextElapseUSecRealtime=Tue 2021-08-31 22:29:33 IST
NextElapseUSecMonotonic=0
LastTriggerUSec=Tue 2021-08-31 00:06:13 IST
LastTriggerUSecMonotonic=0
Result=success
AccuracyUSec=1min
RandomizedDelayUSec=12h
Persistent=yes
WakeSystem=no
RemainAfterElapse=yes
Id=certbot.timer
Names=certbot.timer
Requires=sysinit.target -.mount
WantedBy=timers.target
Conflicts=shutdown.target
Before=shutdown.target certbot.service timers.target
After=sysinit.target -.mount time-sync.target
Triggers=certbot.service
RequiresMountsFor=/var/lib/systemd/timers
Description=Run certbot twice daily
LoadState=loaded
ActiveState=active
SubState=waiting
FragmentPath=/lib/systemd/system/certbot.timer
UnitFileState=enabled
UnitFilePreset=enabled
StateChangeTimestamp=Tue 2021-08-31 12:44:40 IST
StateChangeTimestampMonotonic=7105889
InactiveExitTimestamp=Tue 2021-08-31 12:44:40 IST
InactiveExitTimestampMonotonic=7105889
ActiveEnterTimestamp=Tue 2021-08-31 12:44:40 IST
ActiveEnterTimestampMonotonic=7105889
ActiveExitTimestampMonotonic=0
InactiveEnterTimestampMonotonic=0
CanStart=yes
CanStop=yes
CanReload=no
CanIsolate=no
StopWhenUnneeded=no
RefuseManualStart=no
RefuseManualStop=no
AllowIsolate=no
DefaultDependencies=yes
OnFailureJobMode=replace
IgnoreOnIsolate=no
NeedDaemonReload=no
JobTimeoutUSec=infinity
JobRunningTimeoutUSec=infinity
JobTimeoutAction=none
ConditionResult=yes
AssertResult=yes
ConditionTimestamp=Tue 2021-08-31 12:44:40 IST
ConditionTimestampMonotonic=7105839
AssertTimestamp=Tue 2021-08-31 12:44:40 IST
AssertTimestampMonotonic=7105839
Transient=no
Perpetual=no
StartLimitIntervalUSec=10s
StartLimitBurst=5
StartLimitAction=none
FailureAction=none
SuccessAction=none
InvocationID=5869c97e110049e89cbc1e986cce07f6
CollectMode=inactive
Is this what we are looking for?
Osiris
August 31, 2021, 12:44pm
18
Euh, to be honest, I don't use systemd myself. But it looks like the timer has been installed and has been running certbot, looking at a few of those items like LastTriggerUSec, Result, LoadState and ActiveState.
Seems to me you're all set!
1 Like
@Osiris - Thanks a lot for your time and support!
1 Like