Luckily for me: Drinking and sitting mix just fine!
This was automatically generated by certbot. I have commented the ssl.conf and included this file also but still no luck.

What is the name and path to that file?
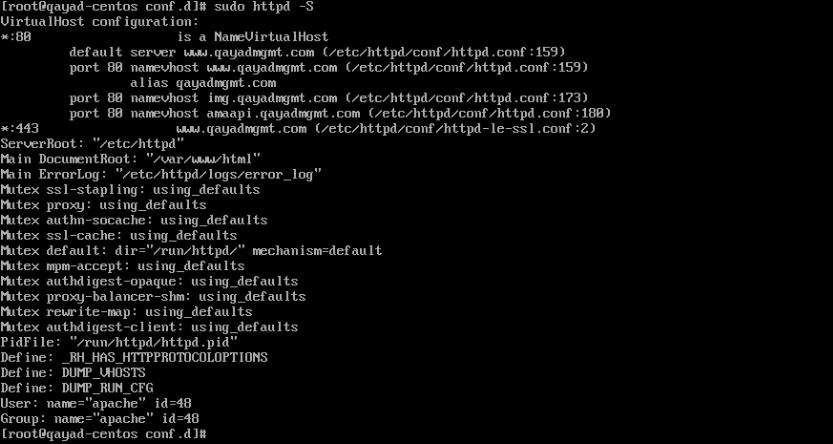
[It wasn't included in the output of "sudo httpd -S"]
Name of the file is httpd-le-ssl.conf and path is /etc/httpd/conf
I have commented the ssl.conf and included this file
If you completely excluded the ssl.conf file, then you have excluded the part that isn't within the vhost.
And if you pay close attention, you will notice there are lines within the ssl.conf vhost that aren't included in the file you included.
Here is the ssl.conf nicely decluttered and split to better emphasize the points:
Listen 443 https #######
SSLPassPhraseDialog exec:/usr/libexec/httpd-ssl-pass-dialog
SSLSessionCache shmcb:/run/httpd/sslcache(512000)
SSLSessionCacheTimeout 300
SSLRandomSeed startup file:/dev/urandom 256
SSLRandomSeed connect builtin
<VirtualHost _default_:443>
ErrorLog logs/ssl_error_log
TransferLog logs/ssl_access_log
LogLevel warn
SSLEngine on #######
SSLProtocol all -SSLv2 -SSLv3
SSLCipherSuite HIGH:3DES:!aNULL:!MD5:!SEED:!IDEA
Include /etc/letsencrypt/options-ssl-apache.conf
SSLCertificateFile /etc/letsencrypt/live/qayadmgmt.com/cert.pem
SSLCertificateKeyFile /etc/letsencrypt/live/qayadmgmt.com/privkey.pem
SSLCertificateChainFile /etc/letsencrypt/live/qayadmgmt.com/chain.pem
<Files ~ "\.(cgi|shtml|phtml|php3?)$">
SSLOptions +StdEnvVars
</Files>
<Directory "/var/www/cgi-bin">
SSLOptions +StdEnvVars
</Directory>
BrowserMatch "MSIE [2-5]" \
nokeepalive ssl-unclean-shutdown \
downgrade-1.0 force-response-1.0
CustomLog logs/ssl_request_log \
"%t %h %{SSL_PROTOCOL}x %{SSL_CIPHER}x \"%r\" %b"
</VirtualHost>
Name of the file is httpd-le-ssl.conf and path is /etc/httpd/conf
Please reshow the output of:
sudo httpd -S
sudo httpd -S
I have tried both methods by including this and yes i have excluded all the ssl.conf file. Please see the output
Please show the output of:
netstat -pant | grep -Ei 'apache|http|:443'
Also, is there a firewall that might be blocking port 443?
curl -Iki https://qayadmgmt.com
curl: (7) Failed to connect to qayadmgmt.com port 443: Connection timed out
I have excluded all the ssl.conf file
Then you might need to include:
Listen 443 https
and
SSLEngine on
appropriately within the httpd-le-ssl.conf file.
rg305:
SSLEngine on
I am able to telnet 443 with qayadmgmt.com locally.
curl: (7) Failed to connect to qayadmgmt.com port 443: Connection timed out

Ok then this needs to be looked at:
Also, is there a firewall that might be blocking port 443?
And while we wait...
You can also check (locally) on the certificate being served with:
openssl s_client -connect qayadmgmt.com:443
[everything shown would also be publicly available (once we remove the firewall block)]
[feel free to post the entire output]
FYI:
The version of OpenSSL being used (1.0.2k-fips) may do well with an update.
As would the Apache
As would the CentOS
openssl s_client -connect qayadmgmt.com:443
CONNECTED(00000003)
---
Certificate chain
0 s:/CN=qayadmgmt.com
i:/C=US/O=Let's Encrypt/CN=R3
1 s:/C=US/O=Let's Encrypt/CN=R3
i:/C=US/O=Internet Security Research Group/CN=ISRG Root X1
2 s:/C=US/O=Internet Security Research Group/CN=ISRG Root X1
i:/O=Digital Signature Trust Co./CN=DST Root CA X3
---
Server certificate
-----BEGIN CERTIFICATE-----
MIIFMjCCBBqgAwIBAgISA3ftFsnCDpc4euEL1UqIeG10MA0GCSqGSIb3DQEBCwUA
MDIxCzAJBgNVBAYTAlVTMRYwFAYDVQQKEw1MZXQncyBFbmNyeXB0MQswCQYDVQQD
EwJSMzAeFw0yMTA2MzAyMzA0MDVaFw0yMTA5MjgyMzA0MDRaMBgxFjAUBgNVBAMT
DXFheWFkbWdtdC5jb20wggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCx
Fc8/OOjXA8QQwhhALO8mUj+/ln47dGXFbuFy1lqQhAAeVv/Vxcs67Isru7qwWfAx
s9EM0GdSh+R0AdnRa7tUs3AjMxxKZTfTYNT4B/4YOwZDcGyC1Y25e+ZFkycsY93Y
PDXSMRgnfoTLj9Q5Bw90DSGLjYV2FPIuPjParD470PjU1R3O7oLfZH5Wo4iUOgbc
A3EeHwhYc6Bm6rdYnu3KPPyzP1nb+toXeIre+tNtBdH8qL7z2UvhxGnl84klA328
U2aMZG1hkpDoWOImhJVE3lXR5F/aZsKfVpkkpOY/fRqd3Oe8m2SBY+5ZFnqepe+g
KPVJhrGKJ2u7YNRmR5qTAgMBAAGjggJaMIICVjAOBgNVHQ8BAf8EBAMCBaAwHQYD
VR0lBBYwFAYIKwYBBQUHAwEGCCsGAQUFBwMCMAwGA1UdEwEB/wQCMAAwHQYDVR0O
BBYEFO6fc+Pya6nb6NJnE+MFL8fbw98+MB8GA1UdIwQYMBaAFBQusxe3WFbLrlAJ
QOYfr52LFMLGMFUGCCsGAQUFBwEBBEkwRzAhBggrBgEFBQcwAYYVaHR0cDovL3Iz
Lm8ubGVuY3Iub3JnMCIGCCsGAQUFBzAChhZodHRwOi8vcjMuaS5sZW5jci5vcmcv
MCsGA1UdEQQkMCKCDXFheWFkbWdtdC5jb22CEXd3dy5xYXlhZG1nbXQuY29tMEwG
A1UdIARFMEMwCAYGZ4EMAQIBMDcGCysGAQQBgt8TAQEBMCgwJgYIKwYBBQUHAgEW
Gmh0dHA6Ly9jcHMubGV0c2VuY3J5cHQub3JnMIIBAwYKKwYBBAHWeQIEAgSB9ASB
8QDvAHYA9lyUL9F3MCIUVBgIMJRWjuNNExkzv98MLyALzE7xZOMAAAF6X2E6cgAA
BAMARzBFAiARM0n0z5S8HRpGfuYdgZfSzUvyZr/NMvR3mm9BJulrwQIhANqinvAI
1Cco0rhQIwSVdnbcQlVZlAvhm/i+I34WltYAAHUAXNxDkv7mq0VEsV6a1FbmEDf7
1fpH3KFzlLJe5vbHDsoAAAF6X2E8XgAABAMARjBEAiAVWPWMv/IgFB7SqL5/j7Yl
fU0YUAWYtOBUqQbaRJWE/AIgYoRqSTcHsn+R1R54AR0zpVoJ86Varu70j7rEboW5
fiMwDQYJKoZIhvcNAQELBQADggEBAKNZZGpwfItG1DJd/Z9HDVG1px4ilTXZNBj1
5xECodzIpczG9GTntbazz4TXxfBKQ3hBiKwvU7v0ZJwmTMlOVXJ9ocaHsu5KG84d
bd4/KewD9maAuLnim3EaHBvoRi7s75IC6uzdP4/wtVpwRzpgSTsMZHpXL5iHSg8H
SWDjAWCmg2lXxs4U5dPXtMRlA31t0Wf5SU7ip1Fs+nprbvQXhFAIKUhAXOHZrQ4x
Xh5GSKUBjjJs0EeB3Ugrod1y8KPawnmGD8Ge3VO6fnmqFDj5iTlqf3DDozExaC78
ffwa4RwVF8YCLRcaSaD0ml3Ifj4LZBVNSSznEXN6S1Ul2+T+a28=
-----END CERTIFICATE-----
subject=/CN=qayadmgmt.com
issuer=/C=US/O=Let's Encrypt/CN=R3
---
No client certificate CA names sent
Peer signing digest: SHA512
Server Temp Key: ECDH, P-256, 256 bits
---
SSL handshake has read 4717 bytes and written 415 bytes
---
New, TLSv1/SSLv3, Cipher is ECDHE-RSA-AES256-GCM-SHA384
Server public key is 2048 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES256-GCM-SHA384
Session-ID: C2B4CC0454D15BBFC36B6FB39BD0CA3DE2DDAC7EAD1BA98652696279CE0DD71E
Session-ID-ctx:
Master-Key: FAEAD8F03FFC695C0DAB561C9FDEEC68541A6543D11CE29A8980F5FB525E061ED373CB2AB3714199D858AEA3C9D1ABBA
Key-Arg : None
Krb5 Principal: None
PSK identity: None
PSK identity hint: None
TLS session ticket lifetime hint: 7200 (seconds)
TLS session ticket:
0000 - 38 e3 81 49 e7 44 c7 44-e1 1c 29 f1 7d 5b 8f 24 8..I.D.D..).}[.$
0010 - f0 38 63 d8 c7 ee 6e 61-1b 34 3d 5e b7 11 4c 6b .8c...na.4=^..Lk
0020 - 9c c6 ca 49 4d 02 e5 62-35 8e 35 03 84 88 f5 e3 ...IM..b5.5.....
0030 - b8 f9 9b 20 97 93 e5 0e-8e 96 ac a7 b1 69 76 99 ... .........iv.
0040 - 40 20 cb a3 d2 47 9a ac-f2 81 9b e3 17 07 9a b2 @ ...G..........
0050 - e5 29 b9 b4 6f cc 40 ae-a5 57 2f 32 b6 91 c3 47 .)..o.@..W/2...G
0060 - 4f d7 3f 66 38 4e d1 67-a9 31 5e 30 5e a7 04 e1 O.?f8N.g.1^0^...
0070 - 2d a5 31 af 38 6d ac 10-f6 a4 6e 5b e9 77 28 7e -.1.8m....n[.w(~
0080 - 7a 18 87 d6 5c c6 84 95-84 cc 93 17 b7 cf 26 b3 z...\.........&.
0090 - c6 3e 79 38 f4 0f cf 27-7b d7 78 b0 a8 3f c4 59 .>y8...'{.x..?.Y
00a0 - f1 39 42 c4 73 a8 3e 17-09 4e 84 3d 34 75 04 0b .9B.s.>..N.=4u..
00b0 - e8 ab b3 eb 7b ca c2 e7-0f f2 d2 f2 19 af 0e 9e ....{...........
Start Time: 1625115656
Timeout : 300 (sec)
Verify return code: 0 (ok)
---
closed
The cert looks good as does the preferred protocol and cipher:
Protocol : TLSv1.2 Cipher : ECDHE-RSA-AES256-GCM-SHA384
I am not able to find firewalld and not iptables
Is there a NAT device inline?
It is Digitalocean server
Does DO have a control panel that operates a firewall or like a firewall?