It seems that after our last renewal of certificates using the command "./letsencrypt-auto renew" on certs that were about to expire, we have SOME Firefox 47 clients that can no longer use our WebRTC servers over WSS.
Client Environment #1:
- Windows 7
- Firefox 47.0
- Chrome 51.0.2704.103 m
Client Environment #2:
- Windows 8
- Firefox 47.0
- Chrome 51.0.2704.103 m
Server Environment:
- CentOS 6.7
- Apache 2.2.15
- Doubango WebRTC2SIP 2.7
The same certificates issued by Let's Encrypt work fine from ALL clients, and all environments when communicating to the server in these fashions:
- Chrome over HTTPS
- Chrome over WS (non-secure)
- Chrome over WSS
- Firefox over HTTPS
- Firefox over WS (non-secure)
AND... in Client Environment #2 ONLY:
- Firefox over WSS
SO... the only scenario where we get FAILURE (which we have not had in the past) is in Client Environment #1 with Firefox over WSS.
Consistently, we receive the message ONLY from Client Environment #1:
Firefox can't establish a connection to the server at wss://website.com:10062
We do not think it is a Doubango WebRTC2SIP issue, since it works everywhere else, and as there is only 1 place to configure the SSL in its config.xml:
ssl-certificates
/etc/letsencrypt/live/website.com/privkey.pem;
/etc/letsencrypt/live/website.com/cert.pem;
*;
no
/ssl-certificates
As well all Apache HTTPS sites for fine from all environments.
In Chrome, where everything also works fine over all protocols, we can see these "Intermediate Certification Authorities" for all client environments under "Settings" > "HTTPS/SSL" > "Manage Certificates":

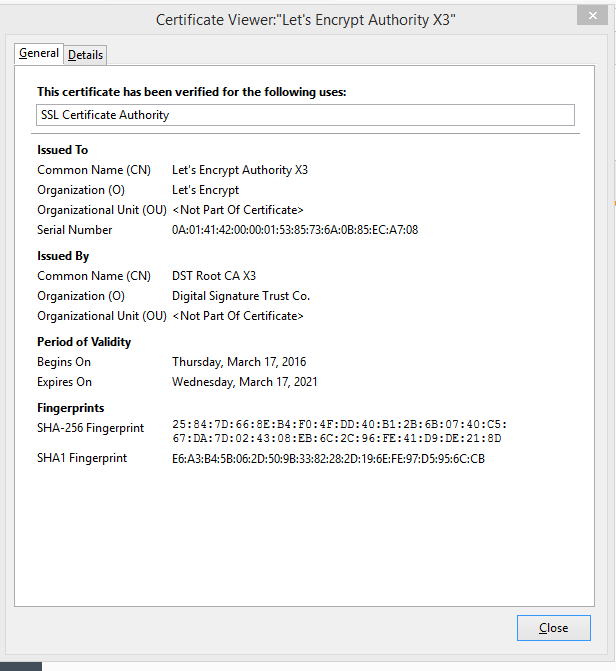
ONLY in Client Environment #2, do we the following under "Options" > "Advance" > "View Certificates":

HOWEVER in Client Environment #1, we ONLY see the following "Certificate Authorities":

SUMMARY:
- Client Environment #2 seems to work fine over WSS with the "Let's Encrypt Authority X3" installed.
- Client Environment #1 does NOT work over WSS with only "Let's Encrypt Authority X1" installed.
QUESTIONS:
-
Why does the "Let's Encrypt Authority X1" certificate authority still work in Chrome (without the need of the additional "Let's Encrypt Authority X3") ?
-
Why does the "Let's Encrypt Authority X1" no longer work in Firefox?
-
How do end-users add "Let's Encrypt Authority X3" easily to their Firefox environment?
-
Moving forward, will we have to force all browser clients to use "Let's Encrypt Authority X3" certificate authority in the future?
Thank you so much for any insight you can provide!
Sorry about the length of this post. I'm also trying to help the WebRTC community by being as descriptive as possible