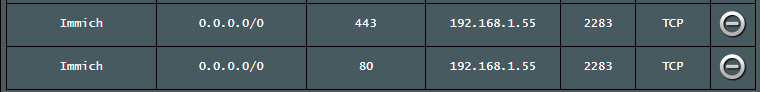
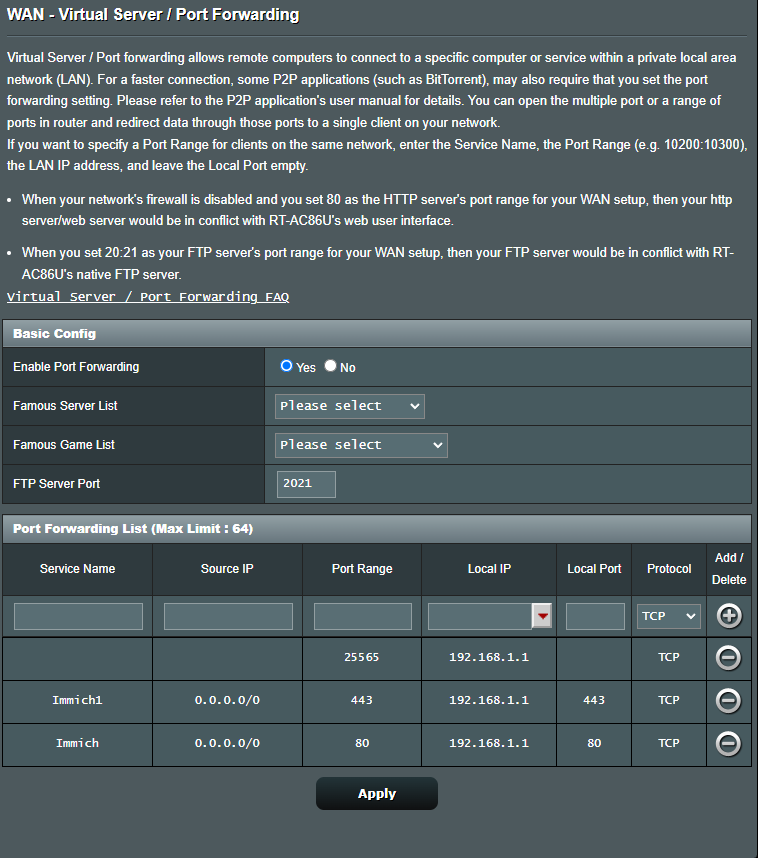
Here is the log
024-10-28 00:31:03,073:DEBUG:certbot._internal.main:certbot version: 2.1.0
2024-10-28 00:31:03,074:DEBUG:certbot._internal.main:Location of certbot entry point: /usr/bin/certbot
2024-10-28 00:31:03,074:DEBUG:certbot._internal.main:Arguments: ['-v', '-a', 'webroot', '-i', 'nginx', '-w', '/var/www/html', '-d', 'familjenisback.duckdns.org']
2024-10-28 00:31:03,074:DEBUG:certbot._internal.main:Discovered plugins: PluginsRegistry(PluginEntryPoint#manual,PluginEntryPoint#nginx,PluginEntryPoint#null,PluginEntryPoint#standalone,PluginEntryPoint#webroot)
2024-10-28 00:31:03,097:DEBUG:certbot._internal.log:Root logging level set at 20
2024-10-28 00:31:03,099:DEBUG:certbot._internal.plugins.selection:Requested authenticator webroot and installer nginx
2024-10-28 00:31:03,301:DEBUG:certbot._internal.plugins.selection:Single candidate plugin: * nginx
Description: Nginx Web Server plugin
Interfaces: Authenticator, Installer, Plugin
Entry point: nginx = certbot_nginx._internal.configurator:NginxConfigurator
Initialized: <certbot_nginx._internal.configurator.NginxConfigurator object at 0x7fb84ea790>
Prep: True
2024-10-28 00:31:03,302:DEBUG:certbot._internal.plugins.selection:Single candidate plugin: * webroot
Description: Place files in webroot directory
Interfaces: Authenticator, Plugin
Entry point: webroot = certbot._internal.plugins.webroot:Authenticator
Initialized: <certbot._internal.plugins.webroot.Authenticator object at 0x7fb52bdf10>
Prep: True
2024-10-28 00:31:03,303:DEBUG:certbot._internal.plugins.selection:Selected authenticator <certbot._internal.plugins.webroot.Authenticator object at 0x7fb52bdf10> and installer <certbot_nginx._internal.configurator.NginxConfigurator object at 0x7fb84ea790>
2024-10-28 00:31:03,303:INFO:certbot._internal.plugins.selection:Plugins selected: Authenticator webroot, Installer nginx
2024-10-28 00:31:03,619:DEBUG:certbot._internal.main:Picked account: <Account(RegistrationResource(body=Registration(key=None, contact=(), agreement=None, status=None, terms_of_service_agreed=None, only_return_existing=None, external_account_binding=None), uri='https://acme-v02.api.letsencrypt.org/acme/acct/2023045147', new_authzr_uri=None, terms_of_service=None), 74758d56be3cf24b60899126aa59204e, Meta(creation_dt=datetime.datetime(2024, 10, 27, 11, 49, 52, tzinfo=<UTC>), creation_host='pi', register_to_eff='harry.isback07@gmail.com'))>
2024-10-28 00:31:03,620:DEBUG:acme.client:Sending GET request to https://acme-v02.api.letsencrypt.org/directory.
2024-10-28 00:31:03,624:DEBUG:urllib3.connectionpool:Starting new HTTPS connection (1): acme-v02.api.letsencrypt.org:443
2024-10-28 00:31:04,063:DEBUG:urllib3.connectionpool:https://acme-v02.api.letsencrypt.org:443 "GET /directory HTTP/1.1" 200 746
2024-10-28 00:31:04,064:DEBUG:acme.client:Received response:
HTTP 200
Server: nginx
Date: Sun, 27 Oct 2024 23:31:03 GMT
Content-Type: application/json
Content-Length: 746
Connection: keep-alive
Cache-Control: public, max-age=0, no-cache
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
{
"RhJN2biOdtc": "https://community.letsencrypt.org/t/adding-random-entries-to-the-directory/33417",
"keyChange": "https://acme-v02.api.letsencrypt.org/acme/key-change",
"meta": {
"caaIdentities": [
"letsencrypt.org"
],
"termsOfService": "https://letsencrypt.org/documents/LE-SA-v1.4-April-3-2024.pdf",
"website": "https://letsencrypt.org"
},
"newAccount": "https://acme-v02.api.letsencrypt.org/acme/new-acct",
"newNonce": "https://acme-v02.api.letsencrypt.org/acme/new-nonce",
"newOrder": "https://acme-v02.api.letsencrypt.org/acme/new-order",
"renewalInfo": "https://acme-v02.api.letsencrypt.org/draft-ietf-acme-ari-03/renewalInfo",
"revokeCert": "https://acme-v02.api.letsencrypt.org/acme/revoke-cert"
}
2024-10-28 00:31:04,065:DEBUG:certbot._internal.display.obj:Notifying user: Requesting a certificate for familjenisback.duckdns.org
2024-10-28 00:31:04,071:DEBUG:certbot.crypto_util:Generating ECDSA key (2048 bits): /etc/letsencrypt/keys/0010_key-certbot.pem
2024-10-28 00:31:04,076:DEBUG:certbot.crypto_util:Creating CSR: /etc/letsencrypt/csr/0010_csr-certbot.pem
2024-10-28 00:31:04,080:DEBUG:acme.client:Requesting fresh nonce
2024-10-28 00:31:04,080:DEBUG:acme.client:Sending HEAD request to https://acme-v02.api.letsencrypt.org/acme/new-nonce.
2024-10-28 00:31:04,225:DEBUG:urllib3.connectionpool:https://acme-v02.api.letsencrypt.org:443 "HEAD /acme/new-nonce HTTP/1.1" 200 0
2024-10-28 00:31:04,226:DEBUG:acme.client:Received response:
HTTP 200
Server: nginx
Date: Sun, 27 Oct 2024 23:31:04 GMT
Connection: keep-alive
Cache-Control: public, max-age=0, no-cache
Link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
Replay-Nonce: l4CEvUUqx19CZKJulcyUWcLzXIYL6Guzwwss-eiJRxcioNps7uE
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
2024-10-28 00:31:04,227:DEBUG:acme.client:Storing nonce: l4CEvUUqx19CZKJulcyUWcLzXIYL6Guzwwss-eiJRxcioNps7uE
2024-10-28 00:31:04,227:DEBUG:acme.client:JWS payload:
b'{\n "identifiers": [\n {\n "type": "dns",\n "value": "familjenisback.duckdns.org"\n }\n ]\n}'
2024-10-28 00:31:04,238:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/new-order:
{
"protected": "eyJhbGciOiAiUlMyNTYiLCAia2lkIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMjAyMzA0NTE0NyIsICJub25jZSI6ICJsNENFdlVVcXgxOUNaS0p1bGN5VVdjTHpYSVlMNkd1end3c3MtZWlKUnhjaW9OcHM3dUUiLCAidXJsIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL25ldy1vcmRlciJ9",
"signature": "WX_DJRyWEbZVDue-tXC7Yht37-iEuxSvDvdJglivLvTZy6Bo0uVIDMCb2zhVKt50oOIZy2LcKREw7ldJ3ZR-KHSIu5lL_lS2Ur1HbllwmHNqUqEWLSno1NCt6zc33wmTCzIs9gfDb6ip5roRSqRLShVtvwtgr_BAwQ7UYWWhcgOJIPSjdK8sKBE1PuXJ9ZQKxOLgT7OAEocxe0k4Jvq3A5Cikk1aUsODI7LZeo91zf1O-ZTxgD2FsFYiBZreguaTuSLVb-diNTzc7my4Y-qqGHWiWeYC9Mebg3oCoVAR6KCfh053tZ6t0ArSzG2766eRuglXcVl2krMh-GukjhgAtA",
"payload": "ewogICJpZGVudGlmaWVycyI6IFsKICAgIHsKICAgICAgInR5cGUiOiAiZG5zIiwKICAgICAgInZhbHVlIjogImZhbWlsamVuaXNiYWNrLmR1Y2tkbnMub3JnIgogICAgfQogIF0KfQ"
}
2024-10-28 00:31:04,420:DEBUG:urllib3.connectionpool:https://acme-v02.api.letsencrypt.org:443 "POST /acme/new-order HTTP/1.1" 201 352
2024-10-28 00:31:04,421:DEBUG:acme.client:Received response:
HTTP 201
Server: nginx
Date: Sun, 27 Oct 2024 23:31:04 GMT
Content-Type: application/json
Content-Length: 352
Connection: keep-alive
Boulder-Requester: 2023045147
Cache-Control: public, max-age=0, no-cache
Link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
Location: https://acme-v02.api.letsencrypt.org/acme/order/2023045147/317645134287
Replay-Nonce: l4CEvUUqAhBOa9Jkmd89HD8CbXpNdybmanG20NV_tkzQlEAKMEw
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
{
"status": "pending",
"expires": "2024-11-03T23:31:04Z",
"identifiers": [
{
"type": "dns",
"value": "familjenisback.duckdns.org"
}
],
"authorizations": [
"https://acme-v02.api.letsencrypt.org/acme/authz-v3/422094063997"
],
"finalize": "https://acme-v02.api.letsencrypt.org/acme/finalize/2023045147/317645134287"
}
2024-10-28 00:31:04,422:DEBUG:acme.client:Storing nonce: l4CEvUUqAhBOa9Jkmd89HD8CbXpNdybmanG20NV_tkzQlEAKMEw
2024-10-28 00:31:04,422:DEBUG:acme.client:JWS payload:
b''
2024-10-28 00:31:04,428:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/authz-v3/422094063997:
{
"protected": "eyJhbGciOiAiUlMyNTYiLCAia2lkIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMjAyMzA0NTE0NyIsICJub25jZSI6ICJsNENFdlVVcUFoQk9hOUprbWQ4OUhEOENiWHBOZHlibWFuRzIwTlZfdGt6UWxFQUtNRXciLCAidXJsIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2F1dGh6LXYzLzQyMjA5NDA2Mzk5NyJ9",
"signature": "E3MRKwZF7pnvqq4KPmnmpWjsvawjDPVrKeyw-3YQkTg2erNG4MEGKU6dWww1SIGlo88SF0zMxCq1cDTkLsWjtxNF8MBWNxxA9_5jvUqFKUx5Aacn-mqDtj4uam1WVlxGd9WczOqsFkPodAk7FoP-WX3ywLzoKP207ba31JMJX1deBdm9E8BdKcvrWtDO098KGZsprzkl4H-zU9LcNp1GU8y0O1E2C1ulgEvXfLFxUJ0v7vCaak42_QZOAQSwsQ9rR2VtwjlC-AdYMuGM_LaO8xEGsNJ8_w5ao1XC57IxQuP-nps5l963MPNev_Y9Zj9S_qPPKr-9lWLWLF_MaA3CEQ",
"payload": ""
}
2024-10-28 00:31:04,577:DEBUG:urllib3.connectionpool:https://acme-v02.api.letsencrypt.org:443 "POST /acme/authz-v3/422094063997 HTTP/1.1" 200 810
2024-10-28 00:31:04,578:DEBUG:acme.client:Received response:
HTTP 200
Server: nginx
Date: Sun, 27 Oct 2024 23:31:04 GMT
Content-Type: application/json
Content-Length: 810
Connection: keep-alive
Boulder-Requester: 2023045147
Cache-Control: public, max-age=0, no-cache
Link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
Replay-Nonce: l4CEvUUq-nGLe_fLSkL7GnmewlqAFs-MNe936RWRi2u53UiTIIA
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
{
"identifier": {
"type": "dns",
"value": "familjenisback.duckdns.org"
},
"status": "pending",
"expires": "2024-11-03T23:31:04Z",
"challenges": [
{
"type": "http-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/422094063997/nsOb3Q",
"status": "pending",
"token": "FsIZGqOkE6JcvhDiGCBd2pSJZ1rInnugQcSUmbFBw_0"
},
{
"type": "tls-alpn-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/422094063997/rTK1ng",
"status": "pending",
"token": "FsIZGqOkE6JcvhDiGCBd2pSJZ1rInnugQcSUmbFBw_0"
},
{
"type": "dns-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/422094063997/N8t-VA",
"status": "pending",
"token": "FsIZGqOkE6JcvhDiGCBd2pSJZ1rInnugQcSUmbFBw_0"
}
]
}
2024-10-28 00:31:04,579:DEBUG:acme.client:Storing nonce: l4CEvUUq-nGLe_fLSkL7GnmewlqAFs-MNe936RWRi2u53UiTIIA
2024-10-28 00:31:04,580:INFO:certbot._internal.auth_handler:Performing the following challenges:
2024-10-28 00:31:04,580:INFO:certbot._internal.auth_handler:http-01 challenge for familjenisback.duckdns.org
2024-10-28 00:31:04,580:INFO:certbot._internal.plugins.webroot:Using the webroot path /var/www/html for all unmatched domains.
2024-10-28 00:31:04,580:DEBUG:certbot._internal.plugins.webroot:Creating root challenges validation dir at /var/www/html/.well-known/acme-challenge
2024-10-28 00:31:04,582:DEBUG:certbot._internal.plugins.webroot:Attempting to save validation to /var/www/html/.well-known/acme-challenge/FsIZGqOkE6JcvhDiGCBd2pSJZ1rInnugQcSUmbFBw_0
2024-10-28 00:31:04,584:DEBUG:acme.client:JWS payload:
b'{}'
2024-10-28 00:31:04,590:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/chall-v3/422094063997/nsOb3Q:
{
"protected": "eyJhbGciOiAiUlMyNTYiLCAia2lkIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMjAyMzA0NTE0NyIsICJub25jZSI6ICJsNENFdlVVcS1uR0xlX2ZMU2tMN0dubWV3bHFBRnMtTU5lOTM2UldSaTJ1NTNVaVRJSUEiLCAidXJsIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2NoYWxsLXYzLzQyMjA5NDA2Mzk5Ny9uc09iM1EifQ",
"signature": "eL6Txax__V8tawHRvZ_pCIpHW3-ZJDsRk2DTruqGcmjOHwOzN0O3Lv_ftsOxD35NdxYvhiuHRwWI2H76SlKwDgXSQqJs6d-WuZoT_iGFTkrtdeWVok9dNrMEgsivOWP66SkHd55f7zvvfS0x2fKLFlJnv6AMxhc9OhxjzlOKL_FhPi1ga58yhkgg7smeqpEZg5bt-N6qoYDt4a9TJE7k7lGcv7gXX0S7w3ifuTIxE3_9SiN0UOp6c7F6033mmO8nuwA1FHKxrgAFN7Ptv4KmP6U-BfHOjOijieSPJLCNmlGmHHzw5uJYUCvlcvIzxgirOrTyGpdnTgy286kz1pQzlQ",
"payload": "e30"
}
2024-10-28 00:31:04,746:DEBUG:urllib3.connectionpool:https://acme-v02.api.letsencrypt.org:443 "POST /acme/chall-v3/422094063997/nsOb3Q HTTP/1.1" 200 187
2024-10-28 00:31:04,747:DEBUG:acme.client:Received response:
HTTP 200
Server: nginx
Date: Sun, 27 Oct 2024 23:31:04 GMT
Content-Type: application/json
Content-Length: 187
Connection: keep-alive
Boulder-Requester: 2023045147
Cache-Control: public, max-age=0, no-cache
Link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index", <https://acme-v02.api.letsencrypt.org/acme/authz-v3/422094063997>;rel="up"
Location: https://acme-v02.api.letsencrypt.org/acme/chall-v3/422094063997/nsOb3Q
Replay-Nonce: l4CEvUUqlMA94WWODPQRn5RzulvNLPjC_EYPI7TkKv8LKwFpB6c
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
{
"type": "http-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/422094063997/nsOb3Q",
"status": "pending",
"token": "FsIZGqOkE6JcvhDiGCBd2pSJZ1rInnugQcSUmbFBw_0"
}
2024-10-28 00:31:04,748:DEBUG:acme.client:Storing nonce: l4CEvUUqlMA94WWODPQRn5RzulvNLPjC_EYPI7TkKv8LKwFpB6c
2024-10-28 00:31:04,748:INFO:certbot._internal.auth_handler:Waiting for verification...
2024-10-28 00:31:05,749:DEBUG:acme.client:JWS payload:
b''
2024-10-28 00:31:05,755:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/authz-v3/422094063997:
{
"protected": "eyJhbGciOiAiUlMyNTYiLCAia2lkIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMjAyMzA0NTE0NyIsICJub25jZSI6ICJsNENFdlVVcWxNQTk0V1dPRFBRUm41Unp1bHZOTFBqQ19FWVBJN1RrS3Y4TEt3RnBCNmMiLCAidXJsIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2F1dGh6LXYzLzQyMjA5NDA2Mzk5NyJ9",
"signature": "bcZD22O3s3g8bzP6Y849XYzr_WD7IwkADTk36wVuZJWaDuXawY3T9iMr5E2PdZqqY7sC0cHvm9jbU3MwlhGP9pXYfP0NdiRweCNFBxg7pbNQaymUJoJiV7ShADOCo3SH3FTiHl2xr3mMmZNY4TcTndHPo1wj39Otk22eDkth-yeAmzJ3n4RvmTNAPVF6-tFOzAGTilnNWJ_H1P3XBf1FOum4SipL8b7oNLrCBX_0rfXNGTyZYLeLnHei4GOZ9WAmiojS7e4sghLM0CUCRWMQUyvtrWKxDJ2psdNU2YJk7qTazCJr9hj9nJpjUV2PK7dvR3ohH9IYCVgloE66bs8Vsg",
"payload": ""
}
2024-10-28 00:31:05,909:DEBUG:urllib3.connectionpool:https://acme-v02.api.letsencrypt.org:443 "POST /acme/authz-v3/422094063997 HTTP/1.1" 200 810
2024-10-28 00:31:05,910:DEBUG:acme.client:Received response:
HTTP 200
Server: nginx
Date: Sun, 27 Oct 2024 23:31:05 GMT
Content-Type: application/json
Content-Length: 810
Connection: keep-alive
Boulder-Requester: 2023045147
Cache-Control: public, max-age=0, no-cache
Link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
Replay-Nonce: l4CEvUUq5N-hWB8BU7Su17mSqicAfCeGyIRkaUxn6cYq_1ML-YM
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
{
"identifier": {
"type": "dns",
"value": "familjenisback.duckdns.org"
},
"status": "pending",
"expires": "2024-11-03T23:31:04Z",
"challenges": [
{
"type": "tls-alpn-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/422094063997/rTK1ng",
"status": "pending",
"token": "FsIZGqOkE6JcvhDiGCBd2pSJZ1rInnugQcSUmbFBw_0"
},
{
"type": "dns-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/422094063997/N8t-VA",
"status": "pending",
"token": "FsIZGqOkE6JcvhDiGCBd2pSJZ1rInnugQcSUmbFBw_0"
},
{
"type": "http-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/422094063997/nsOb3Q",
"status": "pending",
"token": "FsIZGqOkE6JcvhDiGCBd2pSJZ1rInnugQcSUmbFBw_0"
}
]
}
2024-10-28 00:31:05,911:DEBUG:acme.client:Storing nonce: l4CEvUUq5N-hWB8BU7Su17mSqicAfCeGyIRkaUxn6cYq_1ML-YM
2024-10-28 00:31:08,912:DEBUG:acme.client:JWS payload:
b''
2024-10-28 00:31:08,930:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/authz-v3/422094063997:
{
"protected": "eyJhbGciOiAiUlMyNTYiLCAia2lkIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMjAyMzA0NTE0NyIsICJub25jZSI6ICJsNENFdlVVcTVOLWhXQjhCVTdTdTE3bVNxaWNBZkNlR3lJUmthVXhuNmNZcV8xTUwtWU0iLCAidXJsIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2F1dGh6LXYzLzQyMjA5NDA2Mzk5NyJ9",
"signature": "QCOEQzGNtc18F89fHM-8s3UW8eMGoTu2U_8JoG0_S1wnnpXo7xRC9BIVsAHV49_tQUHD-ESZkp3eh1f76bxPGzSNu6rzxxLe8xycIOQAjJFp-VXzBzcwnlno6kCyXa4lFQAHbxJGl27YW2h2uot_9K2WOe5DQSUEqdIBJsZ9McJnYBija3oEuqz8Rg1ryMJTBRtmEiKgk4PUt7-h9gfv6nPJfWtmugEnTaFpfmM85AJzGOKG1Ritlwn5PN5ZIYXRPFsMc62LokoXL-lotAidFciXS4v3zBNK0FSWI7tt-_bUkDQtjuXrmtzdTm41l8f6-JH5_nIwLfHr9Gl4LWc2WA",
"payload": ""
}
2024-10-28 00:31:09,085:DEBUG:urllib3.connectionpool:https://acme-v02.api.letsencrypt.org:443 "POST /acme/authz-v3/422094063997 HTTP/1.1" 200 810
2024-10-28 00:31:09,087:DEBUG:acme.client:Received response:
HTTP 200
Server: nginx
Date: Sun, 27 Oct 2024 23:31:09 GMT
Content-Type: application/json
Content-Length: 810
Connection: keep-alive
Boulder-Requester: 2023045147
Cache-Control: public, max-age=0, no-cache
Link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
Replay-Nonce: l4CEvUUq1RDh_BBJwmF3i5AAtbOJAwEZjZkRkNAuPosbW7byv_s
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
{
"identifier": {
"type": "dns",
"value": "familjenisback.duckdns.org"
},
"status": "pending",
"expires": "2024-11-03T23:31:04Z",
"challenges": [
{
"type": "dns-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/422094063997/N8t-VA",
"status": "pending",
"token": "FsIZGqOkE6JcvhDiGCBd2pSJZ1rInnugQcSUmbFBw_0"
},
{
"type": "http-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/422094063997/nsOb3Q",
"status": "pending",
"token": "FsIZGqOkE6JcvhDiGCBd2pSJZ1rInnugQcSUmbFBw_0"
},
{
"type": "tls-alpn-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/422094063997/rTK1ng",
"status": "pending",
"token": "FsIZGqOkE6JcvhDiGCBd2pSJZ1rInnugQcSUmbFBw_0"
}
]
}
2024-10-28 00:31:09,087:DEBUG:acme.client:Storing nonce: l4CEvUUq1RDh_BBJwmF3i5AAtbOJAwEZjZkRkNAuPosbW7byv_s
2024-10-28 00:31:12,089:DEBUG:acme.client:JWS payload:
b''
2024-10-28 00:31:12,107:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/authz-v3/422094063997:
{
"protected": "eyJhbGciOiAiUlMyNTYiLCAia2lkIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMjAyMzA0NTE0NyIsICJub25jZSI6ICJsNENFdlVVcTFSRGhfQkJKd21GM2k1QUF0Yk9KQXdFWmpaa1JrTkF1UG9zYlc3Ynl2X3MiLCAidXJsIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2F1dGh6LXYzLzQyMjA5NDA2Mzk5NyJ9",
"signature": "M7f3FpRLF8nWmdRyO-ggXG2ei1ew8i9wW34NXuGUBDqhQd8-6iA-z-oMy0qlhND5mIm9IeLCsQH-FPVLDpZApscxAt83lD8i9CgOeI0iiX4LxqPdDqolwONUrD7WF9DOf9PXlSSVdwslb8SET-cfISH8QCBxlc9QMTmxUuBJ2sJnJnkV7GHHNG7B9I5mQjSzYNJmeKYf-Pb0g6KVAeg8W3gRq-sWScuaGy5TU_VjM_oYsLHs36TbgiN-X1pXjNGQZeJs4GUI8nlHA3MSvKC0TkpMfhc9_zc4-1nL2BgA-fd-NLwtYSJHin3i_27SVpR2LfulYx_jLItIIsjTJy4r8g",
"payload": ""
}
2024-10-28 00:31:12,266:DEBUG:urllib3.connectionpool:https://acme-v02.api.letsencrypt.org:443 "POST /acme/authz-v3/422094063997 HTTP/1.1" 200 810
2024-10-28 00:31:12,268:DEBUG:acme.client:Received response:
HTTP 200
Server: nginx
Date: Sun, 27 Oct 2024 23:31:12 GMT
Content-Type: application/json
Content-Length: 810
Connection: keep-alive
Boulder-Requester: 2023045147
Cache-Control: public, max-age=0, no-cache
Link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
Replay-Nonce: l4CEvUUq00iH4i2m3Ux8EBTCfx-PByuxYPwsFYYS3o5FJqBspy8
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
{
"identifier": {
"type": "dns",
"value": "familjenisback.duckdns.org"
},
"status": "pending",
"expires": "2024-11-03T23:31:04Z",
"challenges": [
{
"type": "tls-alpn-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/422094063997/rTK1ng",
"status": "pending",
"token": "FsIZGqOkE6JcvhDiGCBd2pSJZ1rInnugQcSUmbFBw_0"
},
{
"type": "dns-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/422094063997/N8t-VA",
"status": "pending",
"token": "FsIZGqOkE6JcvhDiGCBd2pSJZ1rInnugQcSUmbFBw_0"
},
{
"type": "http-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/422094063997/nsOb3Q",
"status": "pending",
"token": "FsIZGqOkE6JcvhDiGCBd2pSJZ1rInnugQcSUmbFBw_0"
}
]
}
2024-10-28 00:31:12,269:DEBUG:acme.client:Storing nonce: l4CEvUUq00iH4i2m3Ux8EBTCfx-PByuxYPwsFYYS3o5FJqBspy8
2024-10-28 00:31:15,271:DEBUG:acme.client:JWS payload:
b''
2024-10-28 00:31:15,289:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/authz-v3/422094063997:
{
"protected": "eyJhbGciOiAiUlMyNTYiLCAia2lkIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMjAyMzA0NTE0NyIsICJub25jZSI6ICJsNENFdlVVcTAwaUg0aTJtM1V4OEVCVENmeC1QQnl1eFlQd3NGWVlTM281RkpxQnNweTgiLCAidXJsIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2F1dGh6LXYzLzQyMjA5NDA2Mzk5NyJ9",
"signature": "bcxNmHCApQ5vs1ch8CFzoDT6fDAabILGNOF43DkV5XsGaXhQIvvbK_lOr4EUSE0RLpIZFnW52jsuTXK1xZrxedXw8Rr2L_rMjMRJTLf2kZM_Z4buPZU5MRPPbLpy9rmOAmovGUctK8Ooog2UDvRbI89KFbBvyDy546gi0B0boGeHfCXaKUlPHA6tiOd6ANG_I3OcRUW3_gCChckPt_mxCVSs10gjln7-FciOG3-leQ8ogqG3nP6R8FnBF-Zo1-IH7_SvKkEcjC2WX-3jm49TEqaKl3sF4npumboj2g-LNglGh64-Bd7ste5cXKJsyCj9t6WJ9lVTnqwgTgKtQPl2tQ",
"payload": ""
}
2024-10-28 00:31:15,445:DEBUG:urllib3.connectionpool:https://acme-v02.api.letsencrypt.org:443 "POST /acme/authz-v3/422094063997 HTTP/1.1" 200 810
2024-10-28 00:31:15,447:DEBUG:acme.client:Received response:
HTTP 200
Server: nginx
Date: Sun, 27 Oct 2024 23:31:15 GMT
Content-Type: application/json
Content-Length: 810
Connection: keep-alive
Boulder-Requester: 2023045147
Cache-Control: public, max-age=0, no-cache
Link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
Replay-Nonce: l4CEvUUqd-EQ1KUTvBLaCFIOq1LzVDxyulqeOiQxz9qSHWaDTOQ
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
{
"identifier": {
"type": "dns",
"value": "familjenisback.duckdns.org"
},
"status": "pending",
"expires": "2024-11-03T23:31:04Z",
"challenges": [
{
"type": "dns-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/422094063997/N8t-VA",
"status": "pending",
"token": "FsIZGqOkE6JcvhDiGCBd2pSJZ1rInnugQcSUmbFBw_0"
},
{
"type": "tls-alpn-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/422094063997/rTK1ng",
"status": "pending",
"token": "FsIZGqOkE6JcvhDiGCBd2pSJZ1rInnugQcSUmbFBw_0"
},
{
"type": "http-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/422094063997/nsOb3Q",
"status": "pending",
"token": "FsIZGqOkE6JcvhDiGCBd2pSJZ1rInnugQcSUmbFBw_0"
}
]
}
2024-10-28 00:31:15,448:DEBUG:acme.client:Storing nonce: l4CEvUUqd-EQ1KUTvBLaCFIOq1LzVDxyulqeOiQxz9qSHWaDTOQ
2024-10-28 00:31:18,450:DEBUG:acme.client:JWS payload:
b''
2024-10-28 00:31:18,460:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/authz-v3/422094063997:
{
"protected": "eyJhbGciOiAiUlMyNTYiLCAia2lkIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMjAyMzA0NTE0NyIsICJub25jZSI6ICJsNENFdlVVcWQtRVExS1VUdkJMYUNGSU9xMUx6VkR4eXVscWVPaVF4ejlxU0hXYURUT1EiLCAidXJsIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2F1dGh6LXYzLzQyMjA5NDA2Mzk5NyJ9",
"signature": "OD8WBT_o-hPjSGmtVqhSoaB4ashPB4fKX-7tTr8fLAr7nz5NnysuhP4Nr8rDMY3xTHXouEF2nysGlpbURZx5ZmGx8LI-MQOMkrxjWlGFz7-zt_vGxwQHF0IcP8VVNReWRrrrMvzGGuErYQde4BtSq8jjHloHNL6i_heab9Tdebbr0s_sqhZQhtBGErpSsmaIn01LLTIVfUbJY6kP4lnsO20lQ8Jj01PtDoO4DW9ubShyYa1d-Uw8eO0fKub7qAZe_LYXhk2O5N3g5mpR5l5AkwwOXoSo6Bq5LUO80hES0xNPlhOMh_MHF7MTpVDbYkQ0r13q7fVXSGKLUH5Fi4-kzw",
"payload": ""
}
2024-10-28 00:31:18,626:DEBUG:urllib3.connectionpool:https://acme-v02.api.letsencrypt.org:443 "POST /acme/authz-v3/422094063997 HTTP/1.1" 200 810
2024-10-28 00:31:18,627:DEBUG:acme.client:Received response:
HTTP 200
Server: nginx
Date: Sun, 27 Oct 2024 23:31:18 GMT
Content-Type: application/json
Content-Length: 810
Connection: keep-alive
Boulder-Requester: 2023045147
Cache-Control: public, max-age=0, no-cache
Link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
Replay-Nonce: l4CEvUUq9tTC8253_E3YcuQLpgqvaa6SVw5fdUBwXGktfkV9Zik
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
{
"identifier": {
"type": "dns",
"value": "familjenisback.duckdns.org"
},
"status": "pending",
"expires": "2024-11-03T23:31:04Z",
"challenges": [
{
"type": "http-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/422094063997/nsOb3Q",
"status": "pending",
"token": "FsIZGqOkE6JcvhDiGCBd2pSJZ1rInnugQcSUmbFBw_0"
},
{
"type": "dns-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/422094063997/N8t-VA",
"status": "pending",
"token": "FsIZGqOkE6JcvhDiGCBd2pSJZ1rInnugQcSUmbFBw_0"
},
{
"type": "tls-alpn-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/422094063997/rTK1ng",
"status": "pending",
"token": "FsIZGqOkE6JcvhDiGCBd2pSJZ1rInnugQcSUmbFBw_0"
}
]
}
2024-10-28 00:31:18,628:DEBUG:acme.client:Storing nonce: l4CEvUUq9tTC8253_E3YcuQLpgqvaa6SVw5fdUBwXGktfkV9Zik
2024-10-28 00:31:21,629:DEBUG:acme.client:JWS payload:
b''
2024-10-28 00:31:21,647:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/authz-v3/422094063997:
{
"protected": "eyJhbGciOiAiUlMyNTYiLCAia2lkIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMjAyMzA0NTE0NyIsICJub25jZSI6ICJsNENFdlVVcTl0VEM4MjUzX0UzWWN1UUxwZ3F2YWE2U1Z3NWZkVUJ3WEdrdGZrVjlaaWsiLCAidXJsIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2F1dGh6LXYzLzQyMjA5NDA2Mzk5NyJ9",
"signature": "J5eyypHPbv1r-Bdul0a_uQIZ0rduyYbJ4YdZrSbE3bUuzy_zlFL817H59COsoPheLuk8q_-yhtCOn4X0Qln-fSv5NmS7L0CP7bVaN4zcRGo5grwMcgcyMGDtLK7FoXwrrkmwLEg3sCpoYfJYXfP5tIyjVDTqDYM8CfTsjc1IdnfG5hYbR6QkSMzCoMDFcQ-64q22AEKjnbZ3ftCcGIl2fL2HnUBXMUekaIea3mL6P7bi_F1GP29p9qQqB_6neoeUm7wvmlwtbff8JuRIYREjGpxmYjarw5wD-7l5naLJWzSjsVshhyrr6dfwt9WT00EQQKNN0NF1Z6d_mevpU7JISQ",
"payload": ""
}
2024-10-28 00:31:21,804:DEBUG:urllib3.connectionpool:https://acme-v02.api.letsencrypt.org:443 "POST /acme/authz-v3/422094063997 HTTP/1.1" 200 810
2024-10-28 00:31:21,806:DEBUG:acme.client:Received response:
HTTP 200
Server: nginx
Date: Sun, 27 Oct 2024 23:31:21 GMT
Content-Type: application/json
Content-Length: 810
Connection: keep-alive
Boulder-Requester: 2023045147
Cache-Control: public, max-age=0, no-cache
Link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
Replay-Nonce: t7QKW8KeE2aQ8U3SoAbBhLqlPZadR1uHCvk2VaslvGAHpW5nJQg
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
{
"identifier": {
"type": "dns",
"value": "familjenisback.duckdns.org"
},
"status": "pending",
"expires": "2024-11-03T23:31:04Z",
"challenges": [
{
"type": "http-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/422094063997/nsOb3Q",
"status": "pending",
"token": "FsIZGqOkE6JcvhDiGCBd2pSJZ1rInnugQcSUmbFBw_0"
},
{
"type": "tls-alpn-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/422094063997/rTK1ng",
"status": "pending",
"token": "FsIZGqOkE6JcvhDiGCBd2pSJZ1rInnugQcSUmbFBw_0"
},
{
"type": "dns-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/422094063997/N8t-VA",
"status": "pending",
"token": "FsIZGqOkE6JcvhDiGCBd2pSJZ1rInnugQcSUmbFBw_0"
}
]
}
2024-10-28 00:31:21,807:DEBUG:acme.client:Storing nonce: t7QKW8KeE2aQ8U3SoAbBhLqlPZadR1uHCvk2VaslvGAHpW5nJQg
2024-10-28 00:31:24,809:DEBUG:acme.client:JWS payload:
b''
2024-10-28 00:31:24,827:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/authz-v3/422094063997:
{
"protected": "eyJhbGciOiAiUlMyNTYiLCAia2lkIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMjAyMzA0NTE0NyIsICJub25jZSI6ICJ0N1FLVzhLZUUyYVE4VTNTb0FiQmhMcWxQWmFkUjF1SEN2azJWYXNsdkdBSHBXNW5KUWciLCAidXJsIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2F1dGh6LXYzLzQyMjA5NDA2Mzk5NyJ9",
"signature": "JNuIfXyStHQTS-VKeuTM33uveXAbPr7ws0P76apKL-7OMJB2WV3UYQ9pBFn-uNvTY91D0eZ8Vi3jL-TpOXvrbGUwRbC5FAHC1BwecyIGtrLMxT9xFvJTAg5Y56WiFt48SRwpcgndj8wP1mMsaEtdzjOzodGNgWVkw-vOKfQo57K0lYXvZF8xVwNX3fMm8e52WlqgEllJk5j5lpTnrfbWiqEtsgZeDbxmEspkGmy0oSMSpU53ARa4gXbJ8VmTO-yZixcJ57KxjEgfoDCH4Hx4ye8qSVpHL9lW8VfMexCgk_8qzPQ2TDXQWWmoSK-A6UR6IunPs0Cnv5CIoKkvTABz3g",
"payload": ""
}
2024-10-28 00:31:24,984:DEBUG:urllib3.connectionpool:https://acme-v02.api.letsencrypt.org:443 "POST /acme/authz-v3/422094063997 HTTP/1.1" 200 810
2024-10-28 00:31:24,986:DEBUG:acme.client:Received response:
HTTP 200
Server: nginx
Date: Sun, 27 Oct 2024 23:31:24 GMT
Content-Type: application/json
Content-Length: 810
Connection: keep-alive
Boulder-Requester: 2023045147
Cache-Control: public, max-age=0, no-cache
Link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
Replay-Nonce: l4CEvUUqJSkVmie3uUw_Rya2NSCfwC21UTnsFAJk9M_ajSG0jYY
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
{
"identifier": {
"type": "dns",
"value": "familjenisback.duckdns.org"
},
"status": "pending",
"expires": "2024-11-03T23:31:04Z",
"challenges": [
{
"type": "http-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/422094063997/nsOb3Q",
"status": "pending",
"token": "FsIZGqOkE6JcvhDiGCBd2pSJZ1rInnugQcSUmbFBw_0"
},
{
"type": "tls-alpn-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/422094063997/rTK1ng",
"status": "pending",
"token": "FsIZGqOkE6JcvhDiGCBd2pSJZ1rInnugQcSUmbFBw_0"
},
{
"type": "dns-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/422094063997/N8t-VA",
"status": "pending",
"token": "FsIZGqOkE6JcvhDiGCBd2pSJZ1rInnugQcSUmbFBw_0"
}
]
}
2024-10-28 00:31:24,987:DEBUG:acme.client:Storing nonce: l4CEvUUqJSkVmie3uUw_Rya2NSCfwC21UTnsFAJk9M_ajSG0jYY
2024-10-28 00:31:27,989:DEBUG:acme.client:JWS payload:
b''
2024-10-28 00:31:28,007:DEBUG:acme.client:Sending POST request to https://acme-v02.api.letsencrypt.org/acme/authz-v3/422094063997:
{
"protected": "eyJhbGciOiAiUlMyNTYiLCAia2lkIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMjAyMzA0NTE0NyIsICJub25jZSI6ICJsNENFdlVVcUpTa1ZtaWUzdVV3X1J5YTJOU0Nmd0MyMVVUbnNGQUprOU1fYWpTRzBqWVkiLCAidXJsIjogImh0dHBzOi8vYWNtZS12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2F1dGh6LXYzLzQyMjA5NDA2Mzk5NyJ9",
"signature": "fm-CWwV5cOqlsixgivevxKOsI6BIQk8-AlgXcP4QrhYGbcotd6LBWwRjmpyjlDIANS3EV4p5nVEUHceygoSXx72FWab1v7MPb2Tw5BNacLHODweAizQjIHX5Gi11mwS8coBShUnGFoYayZmkYoxkPJ9aGoyJbDjMBr_B453FTyehLJ5CRKO7BRivsESZChUxQAPNl0o9Vci2QVSgLlkC1CpAlTPRaD7z9Uyi794AL9MVQ_wOz5HrmuvyZfTTUew55It76j94bfy8etHSnoSoJQv9GOTkYmjcrmnMZ9sTByAh8E5t0a4Ac1Lrwq-Igd2ja7D3o6Q_6Rtbua7SjMnb_g",
"payload": ""
}
2024-10-28 00:31:28,163:DEBUG:urllib3.connectionpool:https://acme-v02.api.letsencrypt.org:443 "POST /acme/authz-v3/422094063997 HTTP/1.1" 200 1099
2024-10-28 00:31:28,164:DEBUG:acme.client:Received response:
HTTP 200
Server: nginx
Date: Sun, 27 Oct 2024 23:31:28 GMT
Content-Type: application/json
Content-Length: 1099
Connection: keep-alive
Boulder-Requester: 2023045147
Cache-Control: public, max-age=0, no-cache
Link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
Replay-Nonce: l4CEvUUq4A0m1i62ydJR969_oiEOIKGyvGq6vdA0c6MYJhkVdVQ
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
{
"identifier": {
"type": "dns",
"value": "familjenisback.duckdns.org"
},
"status": "invalid",
"expires": "2024-11-03T23:31:04Z",
"challenges": [
{
"type": "http-01",
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/422094063997/nsOb3Q",
"status": "invalid",
"validated": "2024-10-27T23:31:04Z",
"error": {
"type": "urn:ietf:params:acme:error:connection",
"detail": "155.4.61.251: Fetching http://familjenisback.duckdns.org/.well-known/acme-challenge/FsIZGqOkE6JcvhDiGCBd2pSJZ1rInnugQcSUmbFBw_0: Timeout during connect (likely firewall problem)",
"status": 400
},
"token": "FsIZGqOkE6JcvhDiGCBd2pSJZ1rInnugQcSUmbFBw_0",
"validationRecord": [
{
"url": "http://familjenisback.duckdns.org/.well-known/acme-challenge/FsIZGqOkE6JcvhDiGCBd2pSJZ1rInnugQcSUmbFBw_0",
"hostname": "familjenisback.duckdns.org",
"port": "80",
"addressesResolved": [
"155.4.61.251"
],
"addressUsed": "155.4.61.251"
}
]
}
]
}
2024-10-28 00:31:28,165:DEBUG:acme.client:Storing nonce: l4CEvUUq4A0m1i62ydJR969_oiEOIKGyvGq6vdA0c6MYJhkVdVQ
2024-10-28 00:31:28,166:INFO:certbot._internal.auth_handler:Challenge failed for domain familjenisback.duckdns.org
2024-10-28 00:31:28,166:INFO:certbot._internal.auth_handler:http-01 challenge for familjenisback.duckdns.org
2024-10-28 00:31:28,167:DEBUG:certbot._internal.display.obj:Notifying user:
Certbot failed to authenticate some domains (authenticator: webroot). The Certificate Authority reported these problems:
Domain: familjenisback.duckdns.org
Type: connection
Detail: 155.4.61.251: Fetching http://familjenisback.duckdns.org/.well-known/acme-challenge/FsIZGqOkE6JcvhDiGCBd2pSJZ1rInnugQcSUmbFBw_0: Timeout during connect (likely firewall problem)
Hint: The Certificate Authority failed to download the temporary challenge files created by Certbot. Ensure that the listed domains serve their content from the provided --webroot-path/-w and that files created there can be downloaded from the internet.
2024-10-28 00:31:28,169:DEBUG:certbot._internal.error_handler:Encountered exception:
Traceback (most recent call last):
File "/usr/lib/python3/dist-packages/certbot/_internal/auth_handler.py", line 106, in handle_authorizations
self._poll_authorizations(authzrs, max_retries, best_effort)
File "/usr/lib/python3/dist-packages/certbot/_internal/auth_handler.py", line 206, in _poll_authorizations
raise errors.AuthorizationError('Some challenges have failed.')
certbot.errors.AuthorizationError: Some challenges have failed.
2024-10-28 00:31:28,170:DEBUG:certbot._internal.error_handler:Calling registered functions
2024-10-28 00:31:28,170:INFO:certbot._internal.auth_handler:Cleaning up challenges
2024-10-28 00:31:28,170:DEBUG:certbot._internal.plugins.webroot:Removing /var/www/html/.well-known/acme-challenge/FsIZGqOkE6JcvhDiGCBd2pSJZ1rInnugQcSUmbFBw_0
2024-10-28 00:31:28,171:DEBUG:certbot._internal.plugins.webroot:All challenges cleaned up
2024-10-28 00:31:28,172:DEBUG:certbot._internal.log:Exiting abnormally:
Traceback (most recent call last):
File "/usr/bin/certbot", line 33, in <module>
sys.exit(load_entry_point('certbot==2.1.0', 'console_scripts', 'certbot')())
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/certbot/main.py", line 19, in main
return internal_main.main(cli_args)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/certbot/_internal/main.py", line 1736, in main
return config.func(config, plugins)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/certbot/_internal/main.py", line 1440, in run
new_lineage = _get_and_save_cert(le_client, config, domains,
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/certbot/_internal/main.py", line 138, in _get_and_save_cert
lineage = le_client.obtain_and_enroll_certificate(domains, certname)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/certbot/_internal/client.py", line 516, in obtain_and_enroll_certificate
cert, chain, key, _ = self.obtain_certificate(domains)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/certbot/_internal/client.py", line 428, in obtain_certificate
orderr = self._get_order_and_authorizations(csr.data, self.config.allow_subset_of_names)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/certbot/_internal/client.py", line 496, in _get_order_and_authorizations
authzr = self.auth_handler.handle_authorizations(orderr, self.config, best_effort)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/certbot/_internal/auth_handler.py", line 106, in handle_authorizations
self._poll_authorizations(authzrs, max_retries, best_effort)
File "/usr/lib/python3/dist-packages/certbot/_internal/auth_handler.py", line 206, in _poll_authorizations
raise errors.AuthorizationError('Some challenges have failed.')
certbot.errors.AuthorizationError: Some challenges have failed.