Do you have such a file with that name present?
[quote=“jtl, post:102, topic:2436, full:true”]Do you have such a file with that name present?[/quote]Yes, I generated it with openssl.
It depends what other key exchanges you allow and whether it allows forward secrecy etc. It’s not about your best effort but the combination of all possible key exchanges.
Awesome thanks so much, getting the dhparam to work turned out to be quite troublesome on Apache but your way of appending it to the certificate file works a treat with a nice A+ score 
Keep in mind that this setup will lower your SEO.
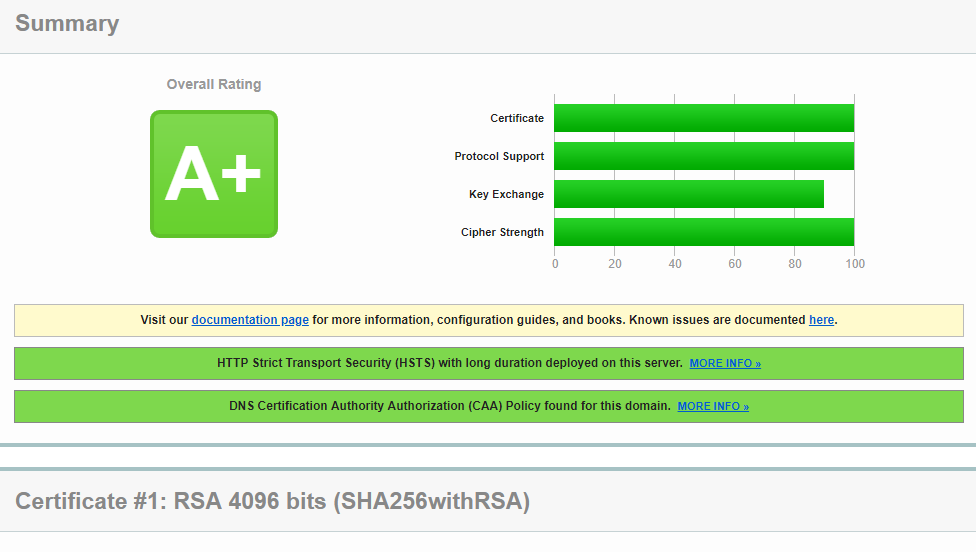
My first time to post. I’m intrigued as to why i can’t get a full 100% on my site. My only problem is that the key exchange is at around 85% Wonder what I am still missing 
You’d need to share either the rest of that report, or your actual domain, before anyone can meaningfully help you with that.
Hi Jared, this is the report on my website
I believe it's because you still have the cipher suites they list as "weak" available. This is a bit of a tradeoff, though, because if you disabled these I believe you would lose a lot of compatibility with anything other than very modern browsers and devices.
EDIT: Actually, I don't think you'll break compatibility by removing those three as well. At least, not with anything for which compatibility was tested. This probably will break it for quite old things.
TLS_RSA_WITH_AES_256_GCM_SHA384 (0x9d) WEAK 256 TLS_RSA_WITH_AES_256_CBC_SHA256 (0x3d) WEAK 256 TLS_RSA_WITH_AES_256_CBC_SHA (0x35) WEAK 256
May i know what would be the updated cipher suite i need to use? shall i add !RSA?
@jared.m It's not the suits itself which are causing the key exchange to get a lower rating.
If you check the SSL Server Rating Guide, you'll see the following table for the key exchange:
Table 4. Key exchange rating guide
- Key exchange aspect Score
- Weak key (Debian OpenSSL flaw) 0%
- Anonymous key exchange (no authentication) 0%
- Key or DH parameter strength < 512 bits 20%
- Exportable key exchange (limited to 512 bits) 40%
- Key or DH parameter strength < 1024 bits (e.g., 512) 40%
- Key or DH parameter strength < 2048 bits (e.g., 1024) 80%
- Key or DH parameter strength < 4096 bits (e.g., 2048) 90%
- Key or DH parameter strength >= 4096 bits (e.g., 4096) 100%
As you can see, for 100 % you'll need a key exchange equivalent to or better than 4096 bits. The certificates public key is 4096, no problems there. So the cipher suits you put forwared aren't the problem: the key exchange would be 100 %.
BUT!
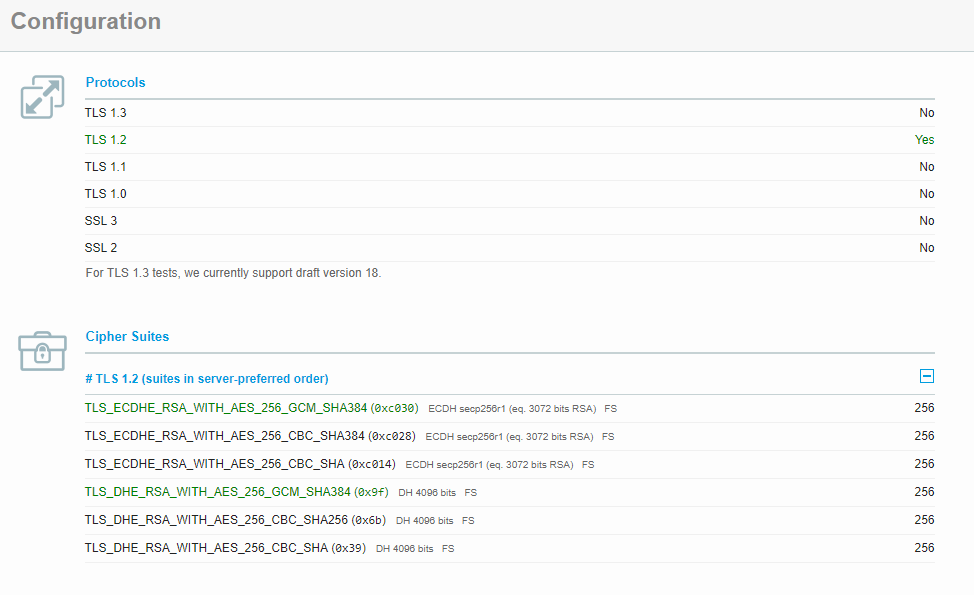
@edmonaft also uses forward secrecy cipher suits (which are GOOD, better even than just RSA key exchange!)
For example, three ephemeral Diffie-Hellman suits (no elliptic curve exploits possible, ephemeral [=good], but slow/resource intensive):
TLS_DHE_RSA_WITH_AES_256_GCM_SHA384 (0x9f) DH 4096 bits FS 256
TLS_DHE_RSA_WITH_AES_256_CBC_SHA256 (0x6b) DH 4096 bits FS 256
TLS_DHE_RSA_WITH_AES_256_CBC_SHA (0x39) DH 4096 bits FS
The Diffie-Hellman primes used are 4096 bits. Which is GOOD. And forward secrecy. Very nice.
But... Also a few ephemeral elliptic curve Diffie-Hellman key exchanges:
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (0xc030) ECDH secp256r1 (eq. 3072 bits RSA) FS 256
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (0xc028) ECDH secp256r1 (eq. 3072 bits RSA) FS 256
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (0xc014) ECDH secp256r1 (eq. 3072 bits RSA) FS
The elliptic curve used here is secp256r1, which is equivalent to only 3072 bits of a RSA key. Which doesn't conform to the 100 % demands of the test.
You can select more ECDHE curves in Apaches SSL configuration with:
SSLOpenSSLConfCmd Curves secp521r1:secp384r1:prime256v1
You might remove the secp521r1 curve b/c it isn't necessary and as far as I know, not every browser supports it.
It might or might not be necessary to add the following line:
SSLOpenSSLConfCmd ECDHParameters Automatic
Try just the first one at first, if it doesn't select another curve, try adding the second one.
BTW, i used !RSA and with the updated cipher suite is not anymore showing any weak information. However, Key Exchange is still at 90% 
Hi Osiris, I followed this guide for the DH params, but I instead used 4096-bits.
I will change the line it states to the one you mentioned here. Will update you on the results!
Update : still the same. it’s still stuck at 90% 
My bad! I need to enter both commands: I now have 100% Key Exchange rate!
SSLOpenSSLConfCmd Curves secp521r1:secp384r1:prime256v1
SSLOpenSSLConfCmd ECDHParameters Automatic