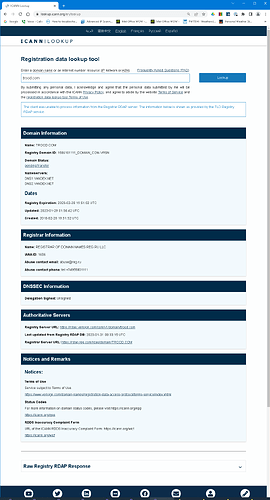
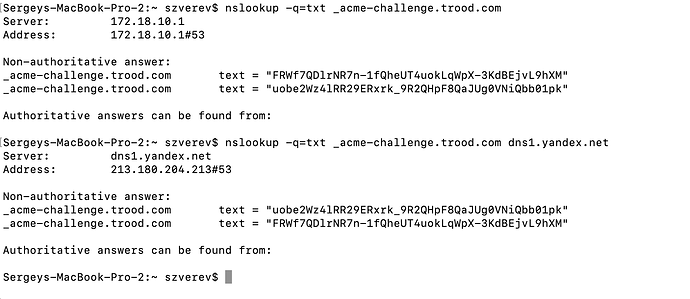
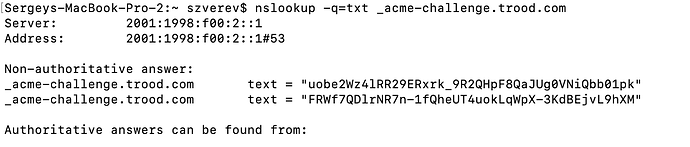
Yes @rg305 you are correct, thanks! 
Raw Registry RDAP Response
{
"objectClassName": "domain",
"handle": "1586101111_DOMAIN_COM-VRSN",
"ldhName": "TROOD.COM",
"links": [
{
"value": "https://rdap.verisign.com/com/v1/domain/TROOD.COM",
"rel": "self",
"href": "https://rdap.verisign.com/com/v1/domain/TROOD.COM",
"type": "application/rdap+json"
},
{
"value": "https://rdap.reg.com/rdap/domain/TROOD.COM",
"rel": "related",
"href": "https://rdap.reg.com/rdap/domain/TROOD.COM",
"type": "application/rdap+json"
}
],
"status": [
"pending transfer"
],
"entities": [
{
"objectClassName": "entity",
"handle": "1606",
"roles": [
"registrar"
],
"publicIds": [
{
"type": "IANA Registrar ID",
"identifier": "1606"
}
],
"vcardArray": [
"vcard",
[
[
"version",
{},
"text",
"4.0"
],
[
"fn",
{},
"text",
"REGISTRAR OF DOMAIN NAMES REG.RU LLC"
]
]
],
"entities": [
{
"objectClassName": "entity",
"roles": [
"abuse"
],
"vcardArray": [
"vcard",
[
[
"version",
{},
"text",
"4.0"
],
[
"fn",
{},
"text",
""
],
[
"tel",
{
"type": "voice"
},
"uri",
"tel:+74955801111"
],
[
"email",
{},
"text",
"abuse@reg.ru"
]
]
]
}
]
}
],
"events": [
{
"eventAction": "registration",
"eventDate": "2010-02-20T19:51:52Z"
},
{
"eventAction": "expiration",
"eventDate": "2023-02-20T19:51:52Z"
},
{
"eventAction": "last changed",
"eventDate": "2023-01-29T01:56:42Z"
},
{
"eventAction": "last update of RDAP database",
"eventDate": "2023-01-31T16:33:15Z"
}
],
"secureDNS": {
"delegationSigned": false
},
"nameservers": [
{
"objectClassName": "nameserver",
"ldhName": "DNS1.YANDEX.NET"
},
{
"objectClassName": "nameserver",
"ldhName": "DNS2.YANDEX.NET"
}
],
"rdapConformance": [
"rdap_level_0",
"icann_rdap_technical_implementation_guide_0",
"icann_rdap_response_profile_0"
],
"notices": [
{
"title": "Terms of Use",
"description": [
"Service subject to Terms of Use."
],
"links": [
{
"href": "https://www.verisign.com/domain-names/registration-data-access-protocol/terms-service/index.xhtml",
"type": "text/html"
}
]
},
{
"title": "Status Codes",
"description": [
"For more information on domain status codes, please visit https://icann.org/epp"
],
"links": [
{
"href": "https://icann.org/epp",
"type": "text/html"
}
]
},
{
"title": "RDDS Inaccuracy Complaint Form",
"description": [
"URL of the ICANN RDDS Inaccuracy Complaint Form: https://icann.org/wicf"
],
"links": [
{
"href": "https://icann.org/wicf",
"type": "text/html"
}
]
}
]
}